The Good | Ukrainian Ransomware Gang Busted By Cyber Cops
A ransomware gang operating out of Kyiv, Ukraine has been taken down by European police, it was announced this week. It is estimated the gang had attacked more than 250 servers across 71 countries during its active lifetime and caused losses of several hundred million euros.
A joint police task force raided 30 locations and seized over a hundred devices, resulting in the arrest of four individuals and the alleged ringleader of the gang. Europol said that the gang broke into networks using phishing emails, brute force attacks, SQL injection and stolen credentials. Once inside a network, they deployed tools such as Cobalt Strike and TrickBot to further their access. They would then remain hidden, sometimes for months, before deploying various kinds of malware, including LockerGoga, MegaCortex, HIVE and Dharma ransomware to lock files and extract payment from victims.
👮Major international operation supported by #Eurojust and @Europol against a ransomware group in Ukraine
💵Attacks caused losses of several hundred millions of euros
📢Read the full story: https://t.co/eTIfEvam8p pic.twitter.com/CS29D6jf4O
— Eurojust (@Eurojust) November 28, 2023
The gang ransomed multiple global organizations located in France, Norway, Germany, The Netherlands, Canada and the U.S. In one example, they demanded 450 BTC (around $17m today) from a leading chemical company in the Netherlands.
The raids, which took place on November 21, were part of a long-standing operation that began in 2019 to identify and disrupt cyber criminal activity in Ukraine. Previous arrests in 2021 led authorities to develop decryptors for some of the gang’s ransomware tools. The operation continues as authorities continue to hunt for other associates of the arrested suspects.
The Bad | Hacktivists Target U.S. Water Treatment Plants
CISA is warning critical infrastructure organizations to be on the alert this week after Iranian-backed threat actors were found to be attacking U.S. water treatment plants and other organizations with embedded Unitronics PLCs.
A Pro-Hamas “Hacktivist” group calling itself “Cyber Av3ngers” has perpetrated intrusions into a number of U.S. organizations by exploiting weak or default passwords in the Israeli-made ICS devices. Aliquippa’s Municipal Water Authority was breached by the threat actor as was a brewery in Pittsburgh. The attackers use network scanning tools to hunt for vulnerable devices connected to the public internet and then attempt to brute force entry through known or weak passwords.
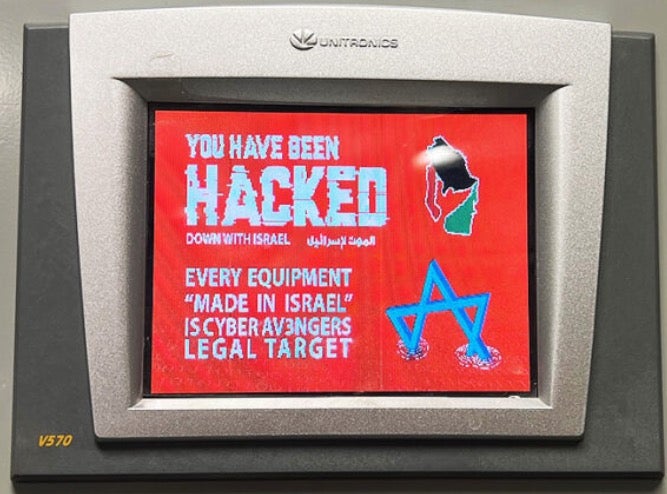
Cyber Av3ngers is known to be an arm of the Iranian IRGC, with a history of attacking industrial targets in relatively unsophisticated attacks. It makes much use of social media to broadcast sometimes false and often exaggerated claims about high-profile hacks. It has been suggested that the group’s social media persona is linked to another threat actor known as Soldiers of Solomon. Other groups that appear to be conducting campaigns against industrial infrastructure include GhostSec.
Although the damage caused in the cases seen so far appears to have been minimal and mitigation relatively quick, the fact that critical infrastructure appears to be easily compromised and is currently being targeted by active groups is a cause for concern. CISA advises all admins of embedded industrial control systems to change default settings, use strong passwords and take other mitigating measures as outlined here.
The Ugly | 3 More Zero Days Found in Chrome & Apple OSes
It’s that time of the month again. Not quite ‘Patch Tuesday’, but the increasingly frequent warning “Apple is aware of a report” that a new zero day (or two) “may have been exploited” in the wild is upon us once more. Users are being urged to update all their Apple things – and Chrome too, while they’re at it – after Google’s TAG team reported three critical severity zero days in its own and Apple’s products.
Tuesday saw Google release patches for seven vulnerabilities in Chrome including CVE-2023-6345. Few details were disclosed about the bug other than that it involves an integer overflow in the Skia Graphics Engine. Skia is used in Chrome to handle tasks such as drawing shapes, text and images on web pages. What Google did say, importantly, is that it was “aware that an exploit for CVE-2023-6345 exists in the wild.”
Meanwhile, on Thursday, Apple issued updates across its desktop and mobile platforms for two vulnerabilities in its WebKit browser engine. On Apple’s mobile platforms, WebKit is used by all browsers, not just Safari. CVE-2023-42916 is an out-of-bounds read issue that could be used to leak sensitive information when processing web content. CVE-2023-42917 is a memory corruption bug that could result in arbitrary code execution when processing web content.
Both flaws were credited to the same Google TAG researcher that reported CVE-2023-6345, suggesting that their discovery was linked. Apple said it was aware of reports that the bugs may have been exploited against versions of iOS before 16.7.1.

As 2023 begins to draw to a close, it’s worth noting that it’s been a record year for Apple zero days, with 19 reported as being ‘actively exploited’ in the wild to date. It’s a sign not only of the company’s products’ popularity but also of their vulnerability.
Apple’s closed mobile ecosystem makes malware detection and remediation challenging for even the most technical of users, while many among its macOS user base still subscribe to the outdated thinking that ‘Macs don’t get malware’. Such folks need to update both their devices and their understanding of the modern cyber threat landscape if they wish to avoid calamity down the road.


