The Good
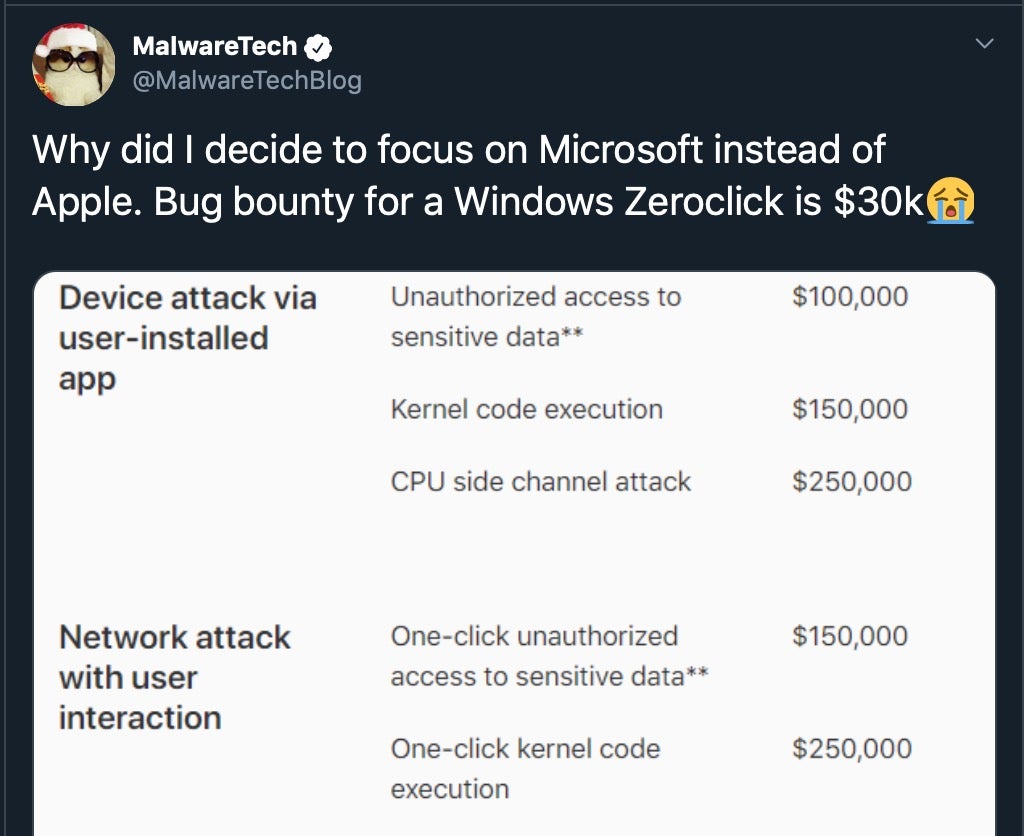
Just in the nick of time before year’s end, Apple has delivered on its promise to introduce an expanded bug bounty program in 2019 that covers all its hardware platforms and is open to anyone. The Apple Security Bounty program offers some generous payouts, and is likely to attract the interest of researchers who typically tend to focus on web applications and the Windows platform.
The ToC are a must read for anyone contemplating taking part. Among other conditions, note that the company’s digital payment service, Apple Pay, is not in scope.
Apple isn’t the only one offering extra cash to those helping to improve security this week, either. Google announced this week that its Patch Rewards Program for Open Source Community will begin offering upfront financial assistance to third-party open source projects that need development funds to focus on security issues. The new initiative will come into effect from January 1st, 2020 and should be particularly attractive to small projects on restricted budgets.
The Bad
Now is the season to be cheerful, unless you’re an Emotet victim. The trojan’s latest malspam campaign not only wants to take advantage of the seasonal round of Christmas party invites to hook unsuspecting recipients but also asks victims to “wear your tackiest/ugliest Christmas sweater” to the fake party.
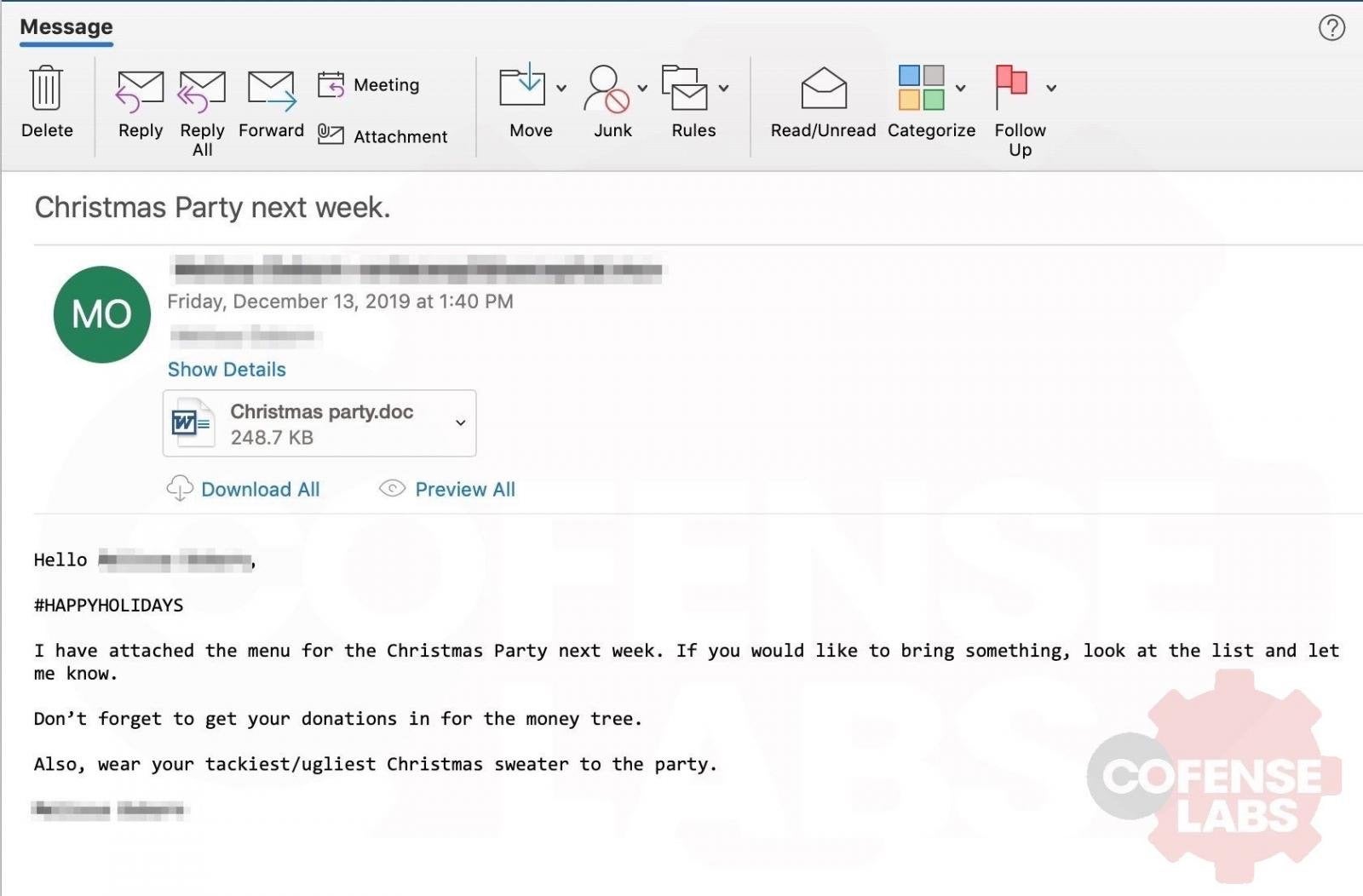
The emails carry poisoned Word documents with names such as “Christmas party.doc” and “Party menu.doc”. When a user tries to open the document, they are first requested to ‘Enable Content’ or ‘Enable Editing’. Doing so runs the malicious macros embedded in the document and serves up the Emotet trojan for an unwelcome seasonal surprise.
Meanwhile, in a graphic portrayal of the damage an enterprise-scale infection can cause, 38000 students and staff at the Justus Liebig University Gießen (JLU) in Germany have been queueing up to personally collect new passwords for their university accounts. JLU was forced to reset all account passwords after falling victim to an unspecified cyber attack. A mass clean-up is underway, with the university banning use of all campus computers until they have been disinfected and badged with a green “healthy” sticker by IT. That could take some time.
The Ugly
Data breaches are always ugly, especially when they combine the worst intentions of criminals with the failings of enterprise opsec. This week has seen more than its fair share of ugly, but the first one that caught our eye was news that Thinkrace, a Chinese manufacturer of location tracking devices widely rebranded and used in 3rd party smartwatches and other location-aware products, has been leaking location and other data through an insecure cloud platform. The leaky backend is used to communicate with and issue commands to all 47 million of its devices. The cloud platform is so vulnerable that researchers could both track device-wearer’s locations and were able to access any of over 2 million voice recordings stored on the company’s servers. The recordings contained conversations between parents and children using the manufacturer’s smartwatches with a voice-chat feature.
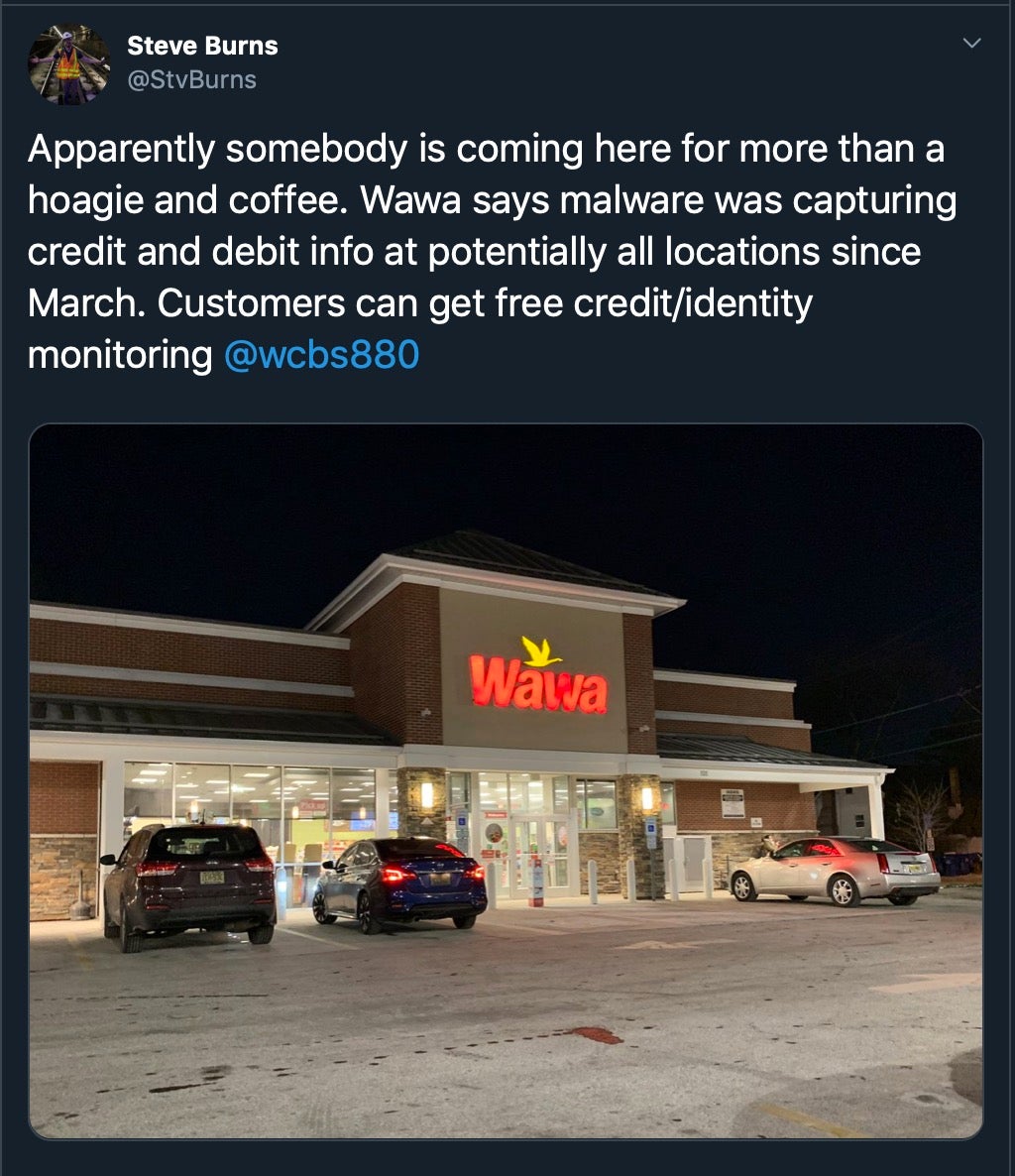
In more ugly news for consumers, it appears that cybercriminals installed malware at potentially all 700 or so Wawa convenience stores and gas stations along the East Coast of the United States from March through to December of this year. In a statement, the company said that it’s possible that any customers using a payment card at a Wawa in-store payment or fuel dispenser during that time could have had their card number, expiration date and cardholder name scraped by the malware.
Wawa says that as of December 12 the infection was removed, and ATM cash machines in the stores were not affected. However, when just doing your weekly shop or filling up the tank becomes an exercise in managing cyber risk, you know enterprise security has still got an awful lot of work to do going into 2020.