The Good
Great news this week as details emerged of an operation in which law enforcement arrested 51 individuals accused of illegally trading the personal data of U.S., European and Ukrainian citizens. Cyber cops in Ukraine carried out raids in which around 100 databases containing stolen personal data spanning 2020-2021 were seized.

The databases reportedly contained information on some 300 million citizens of Ukraine, Europe and the United States. Depending on their content, the databases were sold from anywhere between $18 and $1800 a time. Police said they had also shut down a large site where the data was traded and blocked 30 other channels involved in the illegal dissemination of data.
19 suspects have already been charged, with more expected to follow. Ukrainian authorities said that data theft had become increasingly attractive as the number of owners and managers of personal data in the private sector had increased. This presents new challenges as many of these entities struggled with how to prevent and contain data breaches against determined, financially-motivated hackers.
The Bad
“The internet is on fire”, it was declared earlier this week, and the inferno continues to rage in the wake of the Apache Log4j2 vulnerabilities, more formerly tracked as CVE-2021-44228 and CVE-2021-45046. Admins everywhere have been scrambling to find out how exposed they are to the critical remote code execution vulnerabilities in Apache’s Java logging library.
The first vulnerability affects Log4j2 versions 2.0 beta9 to 2.14.1. This was patched in version 2.15.0 released this week, but a second vulnerability that could allow a denial of service (DOS) attack in certain non-default configurations was subsequently discovered. That means administrators need to ensure affected products are updated to Log4j2 v2.16.0.
Infosec itself lost no time in coming up with proof-of-concept exploit code and threat actors were also quick off the mark with cryptominer payloads. In the midst of the panic, predictions of widespread nation-state actor attacks and ransomware incidents have been rife, but none so far have come to light. Expect that to change, is the message everyone should be hearing.
Windows and Linux devices are particularly at risk. macOS hasn’t shipped with Java for over a decade, but there are plenty of macOS applications that require a 3rd party JRE, including Crashplan, Ghidra, Jamf Pro and Gradle. Apple’s own Xcode 13.2 also contains a vulnerable version of log4j2, though it’s unclear at this time how that could be exploited.
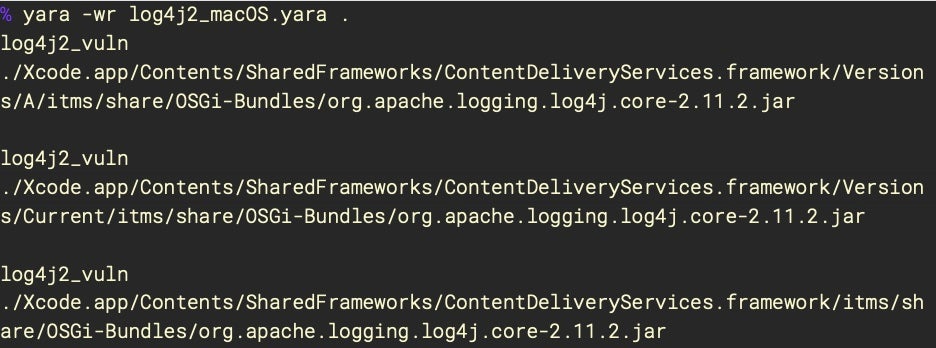
Organizations are urged to discover all internet-facing assets which use Log4j and that allow data input, to update or isolate those assets, and to monitor for anomalous traffic patterns, particularly around outbound JDNI LDAP/RMI traffic and DMZ-initiated outbound connections.
The Ugly
Sometimes, you have to just sit back and admire the dedication of both attackers and defenders to come up with, and discover, novel attacks. This week, hats off to Google’s Project Zero team for reversing and describing one of those “you wouldn’t believe it if it was in a movie” exploits, a nasty, clever, almost-impossible-to-believe exploit of Apple’s iMessage format that was used to target dissidents.
The zero-click exploit, which Project Zero describes as “one of the most technically sophisticated exploits we’ve ever seen”, was developed by the ever-notorious NSO group and sold to unknown regimes around the world. It came to light after Citizen Lab caught the zero-click exploit being used to target a Saudi activist.
The attack begins with a maliciously-crafted PDF file with a .gif file extension being sent to the target. The victim need not read or even open the message; all that is required is that the device receives it. On receipt of the iMessage and fake GIF file, Core Graphics APIs are called into action to parse the file. Here’s where things get crazy.
A zero-day vulnerability (now tracked as CVE-2021-30860) in the open-source PDF parser used by Apple allowed the attackers to construct an entire emulated computer architecture inside the parser’s JBIG2 decompression stream. As explained by Google’s Ian Beer and Samuel Groß:
The full details are well worth a read for anyone interested in just what can be done with what started, after all is said and done, from a simple integer overflow. The resulting exploit, aka FORCEDENTRY, was patched by Apple back in September and affects iOS 14.7 and earlier, all versions of macOS Big Sur prior to 11.6, and watchOS 7.6.1 and earlier.