The Good | DoJ Sentences Key Member of Raccoon Stealer Operation to Five Years In Prison
Two years since ‘Raccoon Stealer’ was dismantled by global law enforcement and one year since its comeback, a key operator behind the Malware-as-a-Service (MaaS) has been officially sentenced. Ukrainian national Mark Sokolovsky receives five years in federal prison for his role in renting out the Raccoon Stealer malware to other cybercriminals for $75 per week or $200 monthly.

Raccoon Stealer primarily targets infected devices to harvest sensitive data, trawling for login credentials, cryptocurrency wallets, credit card details, and email information across various applications and platforms. The FBI’s report highlights that Sokolovsky’s infostealer operation compromised over 52 million user credentials, leading directly to fraud, identity theft, and ransomware attacks globally.
Sokolovsky was first arrested in the Netherlands in March 2022, around the same time the Raccoon Stealer threat group suspended operations, claiming one of their lead developers was killed during the Russian invasion of Ukraine. Despite the disruption, newer versions of Raccoon Stealer emerged in 2023 and boasted enhanced features based on cyber trends as well as “customer” feedback and requests. Researchers then noted that newer Raccoon Stealer iterations focused on OpSec improvements that lower the amount of technical know-now needed by the user and make it harder for cyber defenders to trace.
After being extradited to the U.S. in February, Sokolovsky pled guilty to fraud, money laundering, and identity theft, additionally agreeing to forfeit nearly $24,000 and pay at least $910,000 in restitution. The FBI reminds victims of Raccoon Stealer to reach out for assistance while those who are suspicious may check if their information appears in seized stolen data here.
The Bad | Bitter Threat Group Deliver Espionage-Focused RATs In Attacks on Turkish Defense Sector
Using lures themed on public infrastructure investments, cyberespionage group ‘Bitter’ is targeting defense sector organizations in Turkey. The group has been observed deploying two C++-based malware families, WmRAT and MiyaRAT, in its multi-stage cyberattacks, both designed to enable exfiltration of sensitive and valuable intelligence.
Bitter group, also known as TA397, is suspected by researchers to be acting in support of South Asian government interests. It has been active since at least 2013 with the group’s sights commonly set on entities across China, Pakistan, and India.
In this latest campaign, Bitter leveraged alternate data streams (ADS) within a malicious RAR archive. The archive contained a decoy file about World Bank infrastructure projects in Madagascar, a Windows shortcut (LNK) file disguised as a PDF, and hidden ADS files containing PowerShell code. Upon execution, the LNK file retrieved a decoy document from the World Bank site and executed a Base64-encoded PowerShell script to establish a scheduled task. This task fetched the final payloads from a malicious domain.
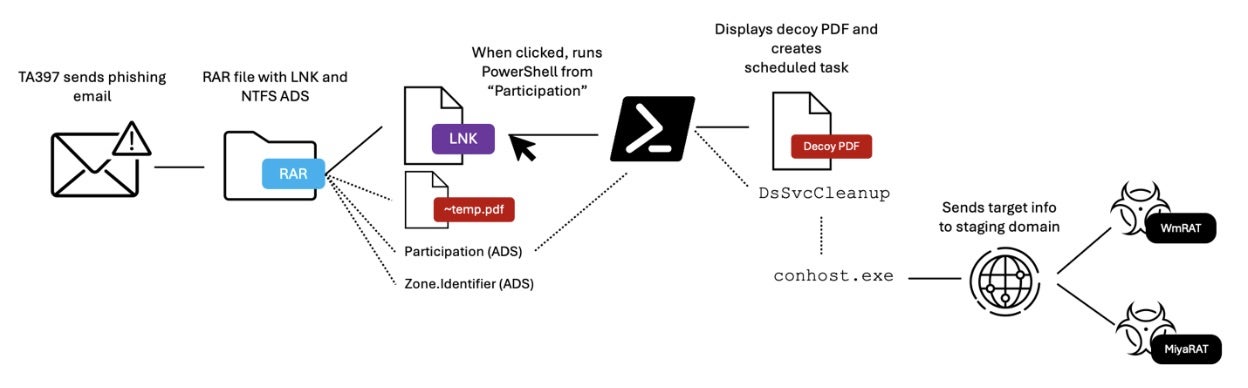
ADS is a feature of the NTFS file system and allows additional data to be concealed within a file without altering its appearance. This provides a stealthy way for threat actors to embed malicious payloads. WmRAT and MiyaRAT’s remote access capabilities enable attackers to monitor and collect system data, manipulate files, capture screenshots, and execute commands.
Given Bitter’s historically selective use of MiyaRAT in only a handful of campaigns, security researchers link this campaign to strategic intelligence-gathering efforts. As the group uses scheduled tasks to maintain access in compromised systems, researchers warn that it will continue to steal privileged information and intellectual property from high-value targets.
The Ugly | Phishing Attack Exploits Windows Management Console to Drop Backdoor Payloads
The use of lures appears as well in a new phishing campaign dubbed ‘FLUX#CONSOLE’, currently targeting organizations in Pakistan. Researchers report that the attack has been employing tax-themed lures to deliver a stealthy backdoor. These attacks likely start with phishing emails and heavily rely on Microsoft Common Console Document (MSC) files, marked by a double-extension (.pdf.msc), to disguise malicious files as PDFs before leveraging Microsoft Management Console (MMC) for execution.
When launched, the MSC file runs embedded JavaScript that retrieves a decoy file, loads a malicious DLL (DismCore.dll), and executes additional code via a remote HTML file. One lure, named “Tax Reductions, Rebates and Credits 2024”, mimics a legitimate document from Pakistan’s Federal Board of Revenue (FBR). Persistence is established through scheduled tasks, enabling the backdoor to contact a remote server and execute commands for data exfiltration.
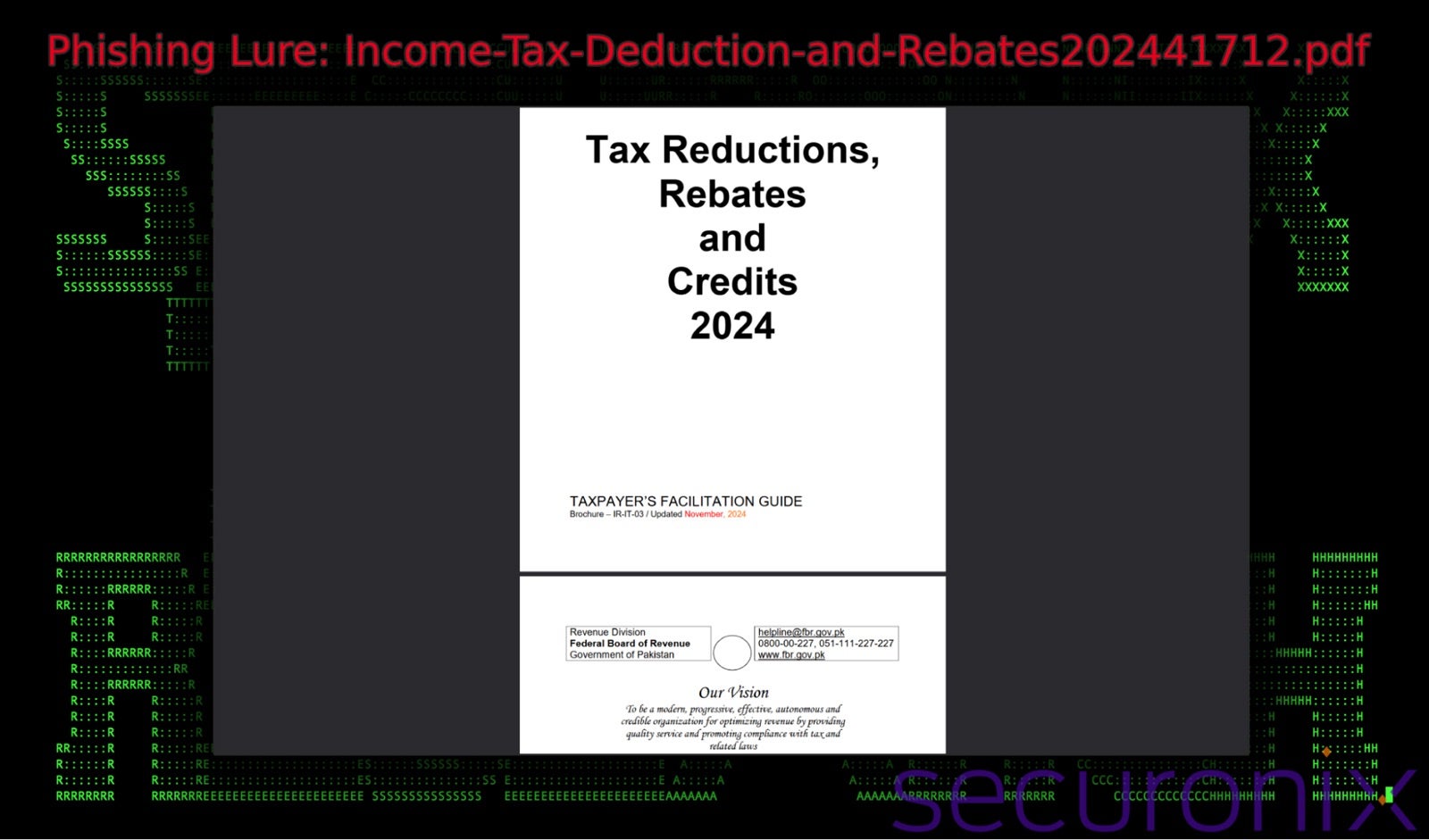
So far, attribution of this particular campaign is inconclusive, but it brings to attention the persistent use of obfuscation in malware development. Between the use of JavaScript in initial stages to deeply hidden malware in the DLL payload, this campaign highlights a shift from LNK files to MSC files, exploiting the latter’s ability to blend malicious activity with legitimate Windows administrative workflows.
Though this attack was disrupted within 24 hours of initial infection, FLUX#CONSOLE emphasizes the growing complexity and challenges related to detecting modern malware, including threat actors leveraging trusted administrative tools to evade detection, the use of advanced obfuscation techniques, and convincing lures that trick users into running the malicious payloads.


