The Good
This week, three of the individuals found to be behind the GozNym family of malware were sentenced following their capture earlier this year. Krasimir Nikolov, Alexander Konovolov and Marat Kazandjian were each sentenced this past week for their roles in long-running campaigns which were all reliant on the GozNym banking trojan and supporting infrastructure. Nikolov (arrested in 2016) received credit for time served, and will now be transferred to Bulgaria. Alexander Konovolov, thought to be one of the leaders of the group, was sentenced to seven years in prison, with Kazandjian receiving a sentence of 5 years.
Starting in 2012, GozNym grew into a highly prolific and successful malware toolset. The threat came to incorporate core banking trojan features (Gozi) along with additional offshoots able to function as ransomware and a backdoor (Nymaim). The trojans were primarily spread via email spam campaigns and were used heavily to steal banking credentials and redirect funds from numerous victims.
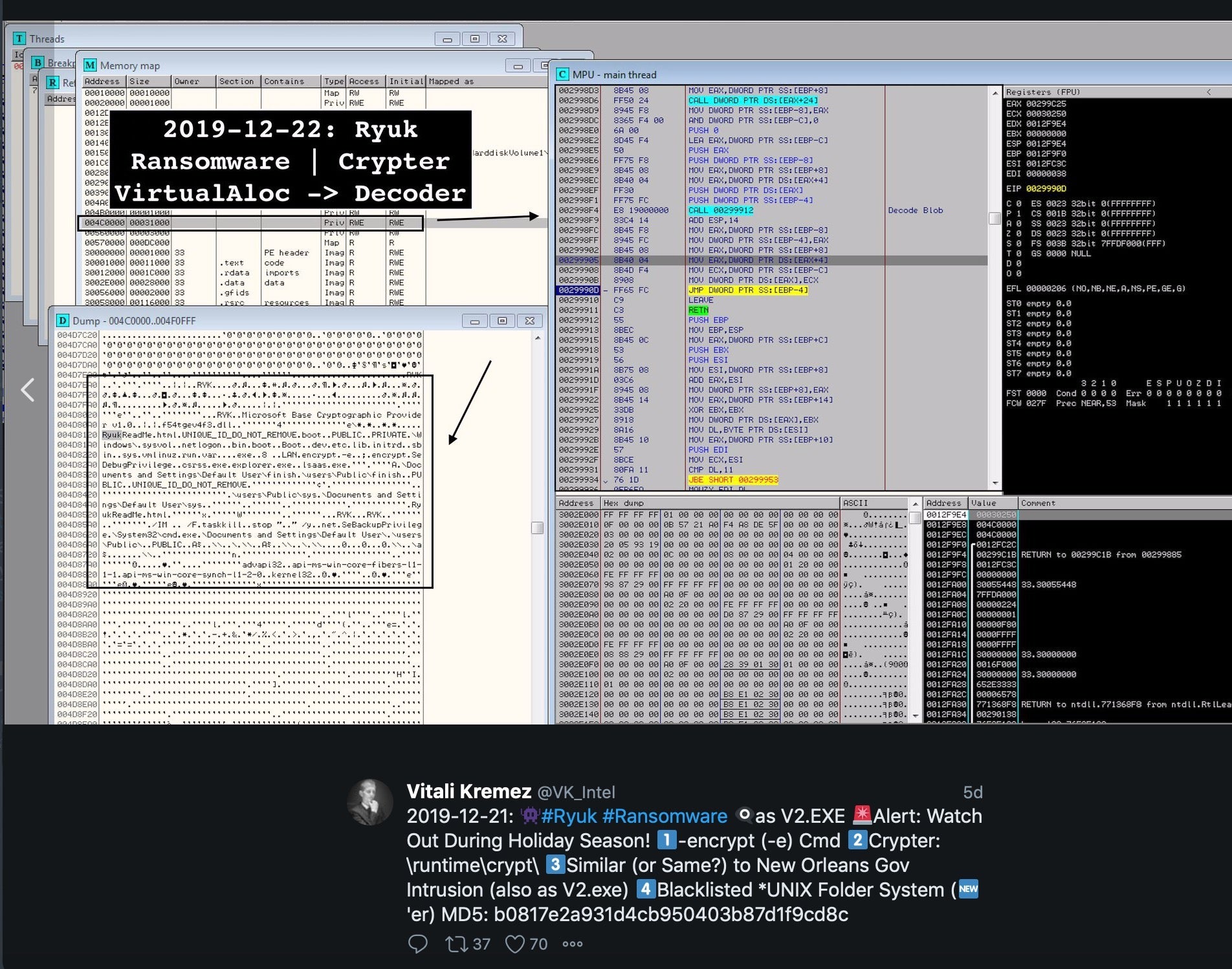
On the slightly lighter side of things…it seems Ryuk is giving WSL (Windows Subsystem for Linux) a bit of a break in recent variants. After analyzing recent samples, researcher Vitali Kremez noted that there are hard-coded exclusions for specific folder names and structures that are inherent to most *nix installations. At first, this was a tad perplexing as there is no “known” *nix variant of Ryuk ransomware, nor is it common for the entire Linux file structure to be shared amongst infectible Windows clients. That being said, further review suggests that the exclusions are meant to accommodate WSL and associated folders. At the end of the day, ransomware authors need their victims’ machines to work to close the circle and facilitate payment. It is believed this is the motivation behind the feature.
The Bad
Things have certainly not slowed down for the ‘Maze Crew’. The actors behind Maze (covered here recently) have continued to deliver on their threat of releasing data from non-compliant victims. Over the last week, additional data from Busch’s and the City of Pensacola was released. While this represents but a small sliver of what the attackers have claimed to exfiltrate from these targeted environments, it serves as an ongoing reminder of how serious the issue of ransomware and related extortion is. As we have stated previously, prevention is critical, the only way to truly be safe from these multi-pronged campaigns is to prevent them in the first place. Targeted environments that were able to restore their encrypted data while circumventing the attackers demands are still at risk due to the data-release component being used here.
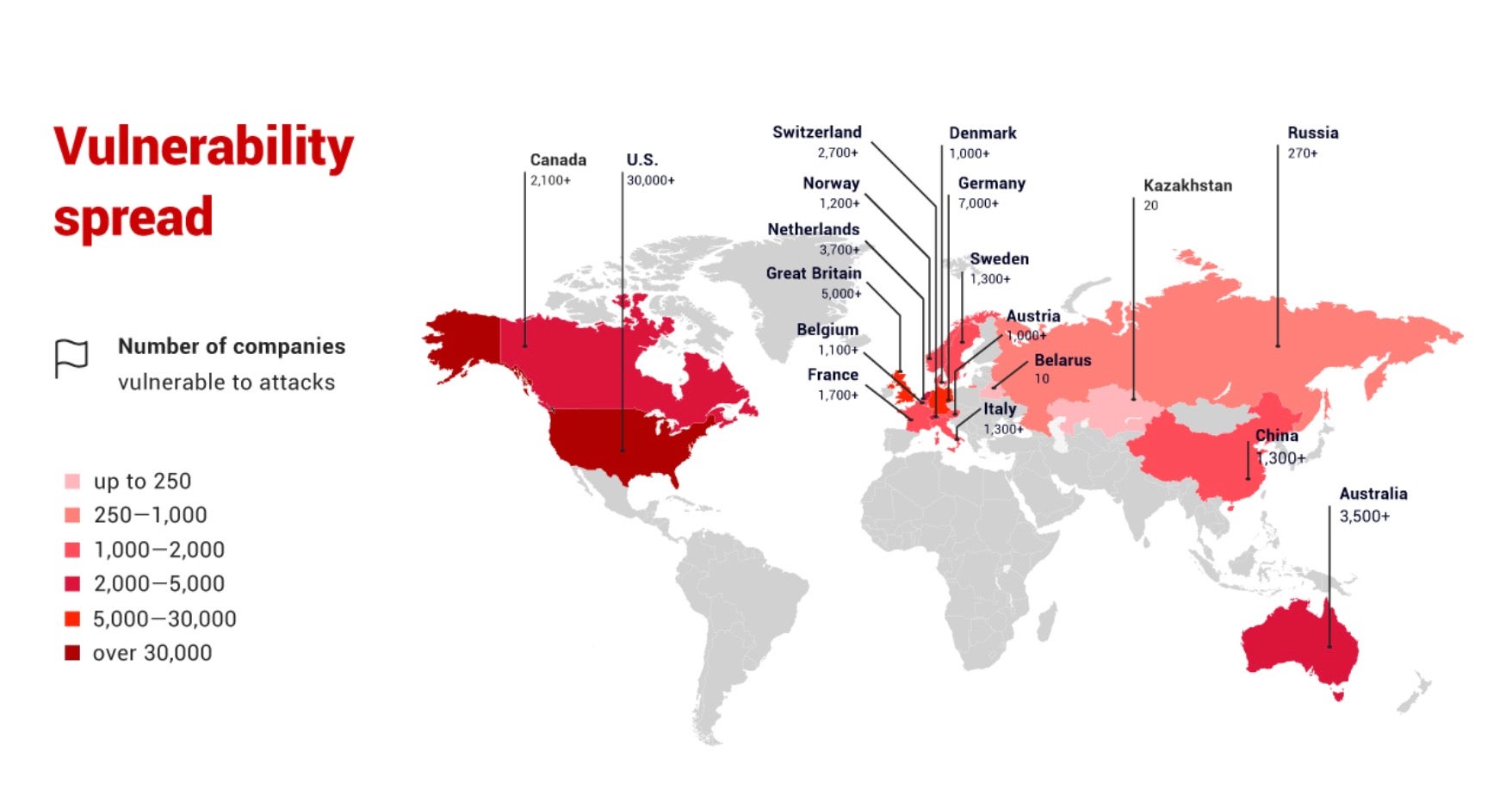
Researchers at Positive Technologies recently disclosed details around a critical security bypass vulnerability affecting multiple Citrix products and technologies. The flaw allows for any unauthenticated attacker to remotely access internal network resources by way of the affected Citrix components. Once inside a network, attackers can continue to move laterally or attack and establish a presence on nodes deeper in the target network. According to Positive Technologies, this issue stands to affect 80,000+ companies, spread across the world. The flaw has been assigned CVE-2019-19781, and Citrix has released a fix, coupled with notice to consider application of the fix a high/critical priority.
The Ugly
Advanced Persistent Threat group APT20 (aka Violin Panda) has been shifting focus onto themselves as a result of recent campaigns in which they successfully defeat 2FA. Choosing to target mainly MSPs (managed service providers) and government entities, the group has been locating vulnerable implementations of the Java application server platform JBoss. Once they have a foothold on the exposed web servers, they proceed to install web shells and further infiltrate the victim’s network. Part of this process included gaining access to RSA SecurID software tokens, allowing the attackers to successfully proceed though 2FA challenges. This method was used also to authenticate to 2FA-protected VPN accounts.
It is reported that the attackers were able to make small modifications to the software token mechanisms so as to allow them to generate valid tokens without validation of the specific systems. These tactics were said to be a small component of the broader Operation Wocao.