The Good
Eight members of a SIM-swapping gang that targeted thousands of U.S. individuals during 2020, including hundreds of social media celebs, musicians and sport stars, have been arrested in the U.K. The gang is thought to have stolen over $100 million by using social engineering lures or malicious insiders to hijack American cell phone accounts.
Having successfully persuaded a carrier to swap the victim’s real SIM number for one controlled by the attackers, the criminals were then able to access a victim’s incoming calls, text and voice messages, personal information, contacts and one-time passwords (OTPs) for sensitive software such as banking apps. The gang also stole Bitcoin from victims as well as hijacking social media accounts to commit further fraud.

The U.S. Secret Service, the Department of Homeland Security and the FBI were all involved in assisting Britain’s National Crime Agency in the operation. The eight arrested are males aged 18-26 and will face charges under the Computer Misuse Act. They are also expected to be prosecuted for fraud and money laundering, and U.S. prosecutors will be seeking extradition of the accused to the USA.
The Bad
It’s been a week for patching zero days, with both Windows Defender and Google Chrome hitting the headlines for serious vulnerabilities affecting millions of users, both at the Enterprise and Home user levels.
CVE-2021-21148 is a high-severity flaw in Chrome’s JavaScript engine, V8. Although few details have emerged, Google have said that it “is aware of reports that an exploit…exists in the wild”.
Browser zero-days are among the most highly prized by attackers given that for the majority of people browsers are their gateway to the internet, in constant use, and, if a vulnerability includes or can be chained with a sandbox escape, provide a powerful opportunity to take over the entire device. Some reports have speculated that CVE-2021-21148 may be the same vulnerability that Microsoft suggested was being used by the ZINC actors targeting security researchers. Google, however, have not confirmed that at the time of writing.
Speaking of Microsoft, Patch Tuesday came and went this week with the Redwood outfit patching no less than 56 bugs in its software, nine of which are said to be critical and at least one is believed to be actively exploited in the wild. Among the bug fixes was CVE-2021-24092, an elevation of privilege vulnerability in Windows Defender – the AntiVirus protection that comes installed by default on Windows devices – that had remained undiscovered since 2009.
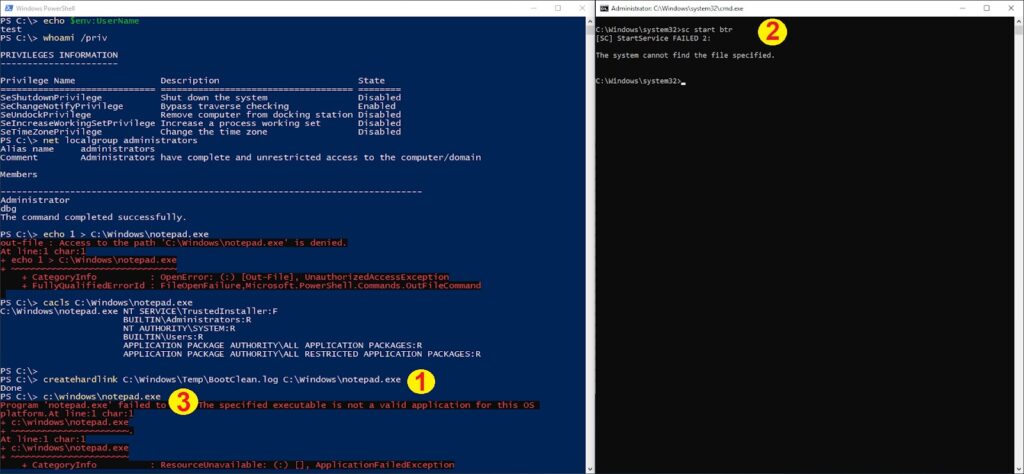
Eagle-eyed researcher Kasif Dekel discovered the vulnerability after noticing that a little-known internal driver, the Boot Time Removal Tool (BTR.sys), doesn’t normally reside on the system but is briefly dropped, activated, and then purged during Defender’s remediation process. Exploring the driver’s internal logic led Dekel to the bug, which potentially affects up to 1 billion devices. That’s the second Windows Defender zero-day discovered in a month.
The Ugly
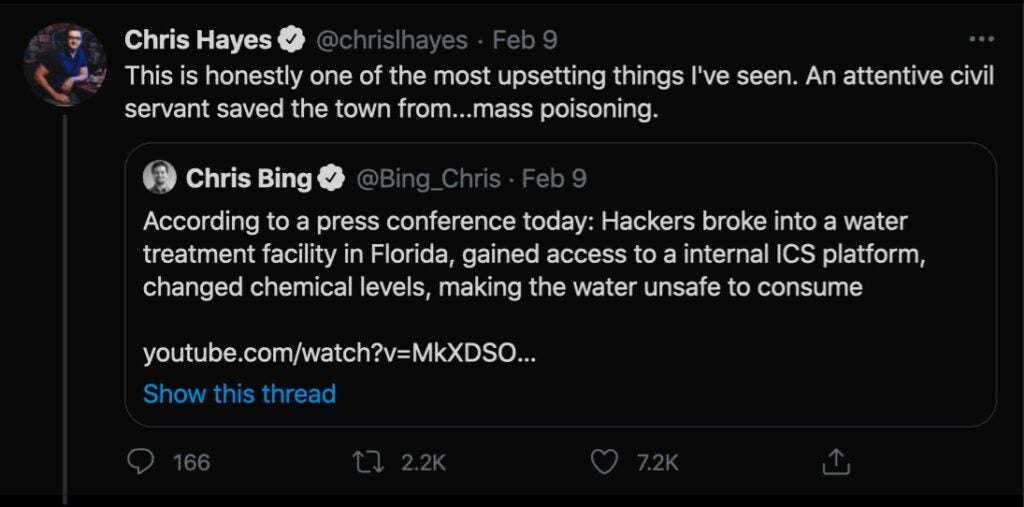
While Microsoft and their users can be thankful for the hard work of security researchers, there’s little that can be done to protect those who refuse to protect themselves (and the rest of us) by ignoring basic security procedures, like: keep your OS up to date, don’t expose sensitive services directly to the internet (aka use a firewall!) and don’t use and share a common password. While many of us have tried to knock these simple cyber sins out of our nearest and dearest, it goes beyond the unthinkable when those responsible for our critical infrastructure are commiting such potentially deadly errors.
And so it turned out this week that a malicious hacker attempted to poison the drinking water supply of 15,000 residents in Oldsmar, Florida, by increasing the quantity of lye (sodium hydroxide) from the miniscule 100 ppm to a massively dangerous level of 11,100 ppm. The water treatment plant serving Oldmar was being controlled by a SCADA system still running the now-unsupported Windows 7 OS on multiple devices. To make matters worse, according to a State advisory for public water suppliers, the breached system was connected directly to the internet, leaving it exposed to anyone who happened to know or learn its IP address. To top it all, all the SCADA devices had a single password that had been shared among multiple users to facilitate remote logging in via TeamViewer.
The incident is being investigated by the County Sheriff’s office, the FBI and the Secret Service. At this time, it is not known whether the cyber attack was conducted by a foreign or domestic intruder, but with over 150,000 public water systems in the U.S, most of which are said to be underfunded, the need for each and every one to get up to speed with basic cybersecurity practices cannot be overstated.