A guest post by John Ayers, Chief Strategy Product Officer at Nuspire, on the importance of aligning your business priorities to your endpoint protection platform.
Long remediation cycles are top of mind for many organizations. Decreasing detection time is an improvement; however, it doesn’t translate to shortening remediation cycles once the threat is identified. There continues to be a disconnect between how fast IT teams are detecting threats and how fast they can eradicate them.
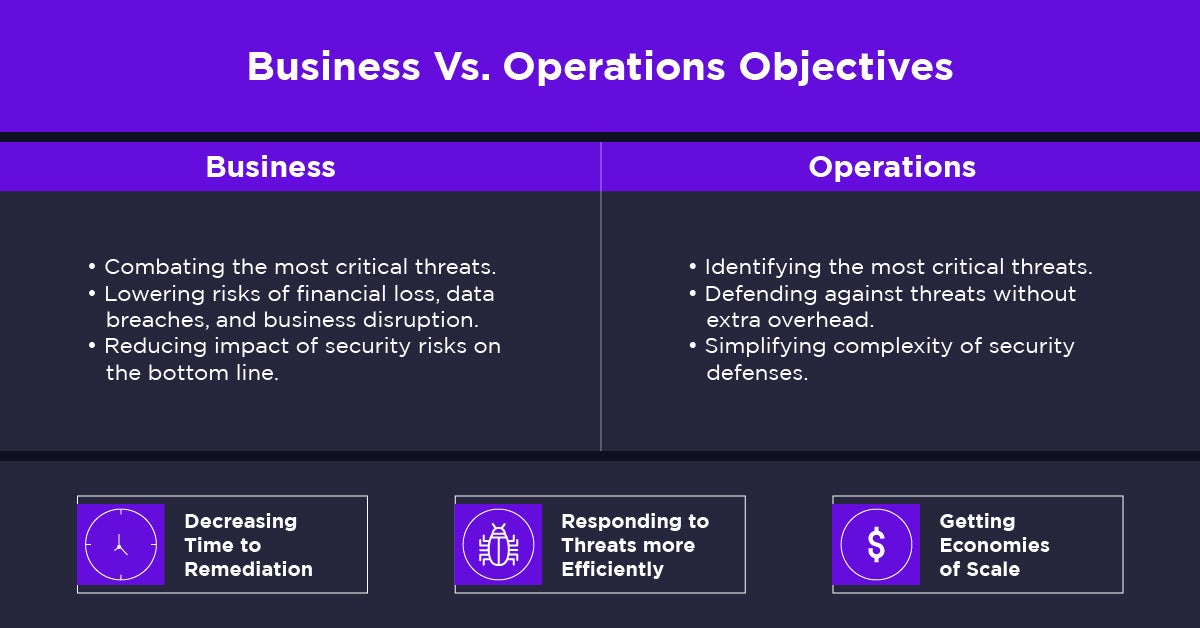
As IT teams are tasked to do more with less, the question becomes: How can they optimize existing tools to meet both security and business operation goals?
The answer is aligning priorities to your endpoint protection platform (EPP). Utilizing the right endpoint protection and response (EDR) solution expands visibility into your environment so as to:
- Further decrease time to detection and remediation
- Improve your SecOps efficiencies and effectiveness
- Achieve proactive security that manages the highest-risk cybersecurity threats
Containing a breach in fewer than 30 days could save you millions. Even for a large enterprise, that’s a sizable amount.

Integrated Managed Detection and Response (MDR)
When doing more with less is both the business and operations mandate, how can you achieve economies of scale? With MDR, you only have to see a threat once in your environment, and it’s blocked everywhere. This saves you a tremendous amount of time, shortening your remediation timeline and shrinking costs. EDR integrates with various MDR components on the back end, while its integration with security information and event management (SIEM) provides a user interface (UI) for the front end.
Endpoint isolation enables you to quickly block incoming and outgoing network activity, eliminating the risk of an infection spreading across your network. During isolation, which can be triggered manually or automatically, you can maintain complete visibility into the endpoint through the cloud. Once we mitigate the threat, we can quickly enable the healthy endpoint to rejoin the network.
Why Cutting Remediation Time Is Key to Cutting Costs
Here’s why that fast mitigation matters: the longer your time to remediate, the bigger the hit to your bottom line. Improving the mean time to detect key performance indicators (KPIs) to measure cybersecurity effectiveness is imperative for C-level stakeholders, including both the CISO and business operations. Yet both camps grapple with issues like the cybersecurity talent shortage, a high number of alerts and false positives—according to the CISO Benchmark Report, 41% of organizations get more than 10,000 security alerts daily—along with a lack of insight into what’s happening across their environment. To break this cycle, you don’t need more tools. You need to automate and integrate technologies that give you economies of scale.
EDR allows CISOs to perform in-depth search for information that other tools collect across the environment. This enables them to confirm whether that data directly relates to the attack. These insights improve scoping and significantly reduce remediation time.
EDR also enables you to perform advanced search—by schedule or on-demand—for any data across the entire environment, treating each endpoint as a database to be queried. You can quickly execute a query, based on triggers such as detection of indicators of compromise, with the option of increasing automated actions.
Next, let’s take a look at a couple of additional capabilities of EDR that provide actionable insights.
Continuous Monitoring and Scanning
As new threat information becomes available and a file is identified as malicious, EDR automatically quarantines the file and alerts you. Using the file trajectory feature, you can see the file’s lifespan across all endpoints, including malware movement from the initial infected host to other devices. Another feature, device trajectory, shows how hosts interact with files, including an event timeline that traces the threat.
Integrated Threat Intelligence
EDR is trained by algorithms to learn how to identify malicious files and activity based on the attributes of known malware. Machine learning capabilities in EDR are fed by the comprehensive artificial intelligence dataset from SentinelOne to ensure a better, more accurate model. This combination helps detect malware at the point of entry, even if a particular variant is brand-new, never having been previously encountered.
Machine Learning (ML) with a Little More Magic
EDR automatically receives actionable intelligence from SentinelOne’s Static AI engine, which detects and prevents threats from executing by use of static ML models. Those models are trained to detect threats by looking at various static attributes that can be extracted from executables, making it a signature-less technology that’s superior at detecting file-based threats. Then, SentinelOne’s Dynamic Behavioral Tracking (DBT) tracks all activities on the system, including file/registry changes, service start/stop, inter-process communication and network activity. This information is fed into a dynamic ML model that detects and kills threats that haven’t already been caught by Static AI. Since it models the behavior of all processes, the ML model identifies threats that are hard to catch with static models.
Improved Efficiency and Effectiveness
How do you identify which assets are the most exposed so that you can prioritize remediation of the relevant threats? The challenge is to determine which endpoints may have a piece of legacy software with a specific Common Vulnerabilities and Exposures (CVE) entry. Typical endpoint solutions identify which endpoints had outdated apps when they were launched. However, if the software hasn’t run on an endpoint in some time, determining the CVE entry exposure may be delayed or even missed.
To solve that problem, EDR performs advanced search to continuously query all endpoints through a SaaS-based portal. Regardless of when an application with a CVE last ran, if at all, you can run a report that identifies all endpoints and where they reside. If the vulnerability is critical, you can choose to isolate the affected endpoints from the network and mitigate the weakness before attackers can exploit it.
On top of this, EDR has more capabilities that can make your security operations more efficient such as Automated Workflows and Endpoint Isolation.
Automated Workflows
One example of automated workflows is retrospective analysis, which automatically quarantines a malicious file that originally presented itself as benign. New, unknown threats don’t get blocked when they first enter the environment, but EDR tracks and monitors the file and its behavior. When new threat intelligence indicates the file is malicious, the retrospective feature doesn’t wait for a human to discover it—it quickly blocks the file while triggering an alert so you can review the incident and mitigate it.
Endpoint Isolation
Even with visibility into your environment, removing a threat and remediating a compromised endpoint takes time. This leaves a wider window for a threat to escalate while increasing your remediation time and, consequently, your risk. Endpoint isolation enables you to quickly block incoming and outgoing network activity, eliminating the risk of an infection spreading across your network. During isolation, which can be triggered manually or automatically via APIs, you can maintain complete visibility into the endpoint through the cloud, as well as allow IP address whitelisting. Once you’ve mitigated the threat, you can quickly enable the healthy endpoint to rejoin the network.
Conclusion
EDR enables you to meet both the business and SecOps goals without additional resources. Defending against evolving threats is a complicated responsibility, but you can reduce the complexity and increase efficiency with advanced solutions that are designed to solve today’s complicated security challenges.
Find a provider that has a comprehensive security portfolio that amplifies your IT team’s ability to defend your organization against the riskiest threats. Enable both CISOs and IT teams to do more with less while improving your security posture—and your bottom line.


