Apple’s WorldWide Developer Conference (WWDC) 2021 kicked off this week in its second outing as a virtual event in light of the ongoing concerns over COVID-19 transmission. Will this be the last isolation-enforced WWDC? We certainly hope so. On the positive side, it’s fair to say that the sessions have become remarkably more effective as Apple has embraced the advantages that pre-recording offers. It’s also fair to say that the notion of people missing out on shared experiences has played a central role in the new features that Apple has on offer this year.
In this post, we’ll be covering what’s new from a security angle in macOS 12, and much of that will revolve around how people share both data and experiences with each other and with the businesses they interact with in their digital lives. There’s a lot of features to discuss, so let’s jump straight in and see what’s new in security with macOS Monterey.

1. System Requirements – A Little More Complex This Time Around
The first rule of security is keep your systems patched, but if your system won’t support the latest software then you’re already off to a bad start. Only models in the following list are officially supported for macOS 12:
- Mac Pro (Late 2013 and later)
- Mac mini (Late 2014 and later)
- MacBook Air (Early 2015 and later)
- MacBook Pro (Early 2015 and later)
- iMac (Late 2015 and later)
- MacBook (Early 2016 and later)
- iMac Pro (2017 and later)
In general, if you’re running hardware that’s hit the 6 year mark you know you’re living on the edge with Apple. Even so, there’s some surprises about what’s not in the list of supported devices for macOS Monterey. In particular, while the 2014 Mac mini remains supported, the beefier and more expensive late 2014 iMac is dropped, as is everything else from 2014 or earlier aside from the late 2013 Mac Pro. 2015 MacBooks are also left behind to chug out the rest of their days on Big Sur or earlier.
macOS 12 also introduces a more complex mix of device dependency for its range of new features. For example, 2017 MacBook Pros can take advantage of the new Universal Control features but not AirPlay to Mac (for which, aside from the 2017 iMac Pro, you’ll need a Mac that’s at least a 2018 model or later). Also, unsurprisingly, there are features that will only work on M1 Macs, such as Live Text. Others, like Erase All Contents, require either an M1 Mac or an Intel Mac with a T2 chip. More on both of these below.
Suffice to say, if you’re looking to upgrade your current Mac or Macs to take advantage of some specific feature or features in Monterey, be sure to check the system requirements first. Don’t be that person who innocently dives into the upgrade and then spams IT with complaints that ‘it doesn’t just work’!
2. Private Relay – Neither Tor Nor VPN
According to Apple’s WWDC, Private Relay hides your IP address and browsing activity from websites and ISPs. No one, not even Apple, is supposed to be able to see both your IP address and what you are accessing.
Private Relay is both a buy-in and an opt-in service. To buy-in, you need to subscribe to iCloud+, the new name for Apple’s paid iCloud storage offerings. If you’re not using iCloud at all or only using the free 5GB iCloud storage, Private Relay won’t be available to you. Those on any paid iCloud storage option can choose to opt-in to Private Relay via System Preferences.

Apple made a lot of noise about privacy and Private Relay this week; however, there’s some pretty big caveats to take into account here. First and foremost, if you’re looking to avoid censorship based on your geolocation, Private Relay is not for you. Apple has specifically stated that users can’t use Private Relay to pretend to be from a different region. Private Relay still tags your browsing activity with an approximate location (e.g., your city), it’s just much less fine-grained than your true IP address.
Secondly, an organization or network can block the hostname of the iCloud Private Relay proxy server, essentially preventing you from accessing that network unless you turn Private Relay off. Organizations that require visibility into network traffic aren’t going to be blind-sided by the Private Relay feature.
For those with maximum need for anonymity, it’s also not clear exactly how robust Apple’s anonymizing is. Apple says it’s working with a 3rd party vendor (widely rumoured to be Cloudflare) in a way such that only Apple knows your true IP and only the vendor knows your activity. Lacking further details than we have already, it’s not immediately clear why Apple and the vendor couldn’t collaborate to put the two together, perhaps at the behest of law enforcement agencies.
In short, Private Relay looks useful for stopping advertising tracking and other public scraping data collection methods, but it’s no substitute for Tor, nor is it a substitute for a VPN if your main use for the latter is to escape geolocation restrictions.
3. Mail Offers A Mixed Bag of Privacy Protections
With macOS 12, Apple has also chosen to beef up Mail’s privacy protections with two key features: preventing remote content from leaking your IP or tracking your viewing behaviour and providing anonymous email addresses.
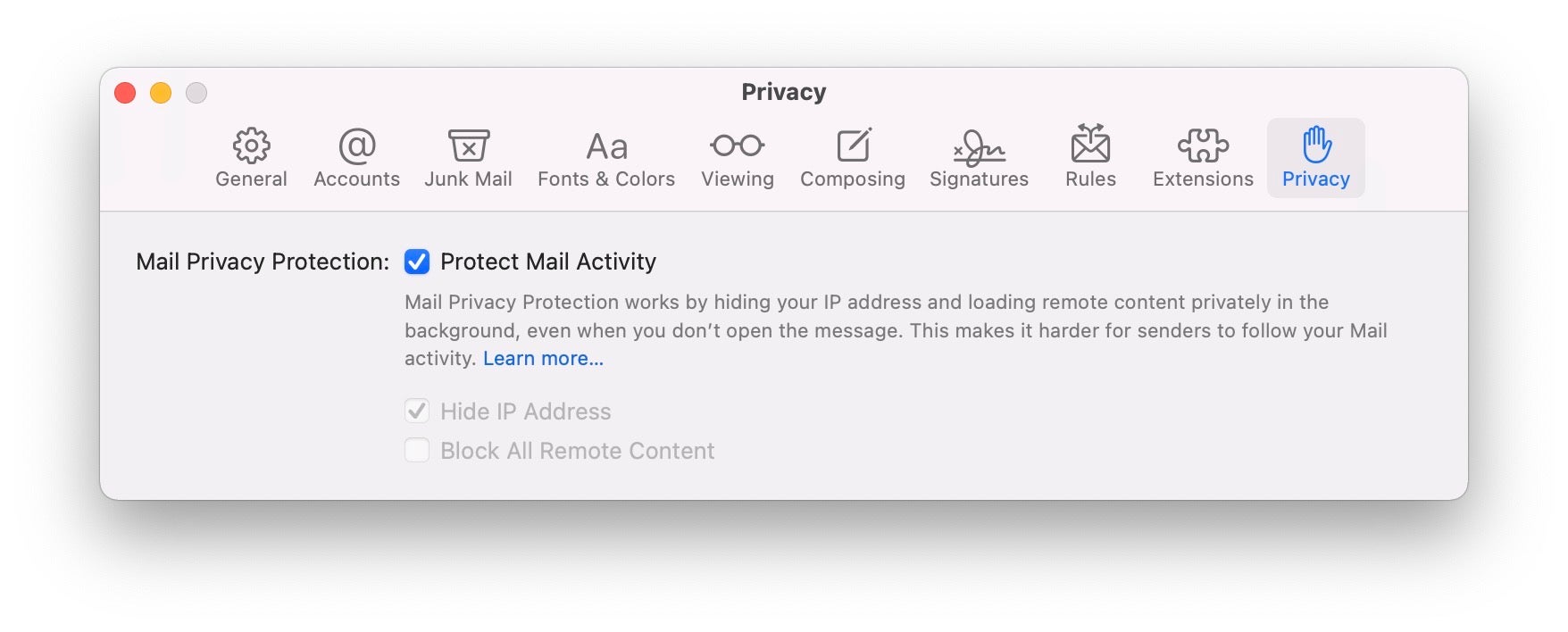
Mail on macOS 11 Big Sur and earlier already allows you to block messages from loading remote content via a Preferences setting, but the drawback with that is that you’re left with text-only messages that lose a lot of rich content. With macOS 12 Monterey, Mail will allow you to enjoy remote content without leaking your IP. Moreover, the sender won’t be able to determine when or even if you read the email. This effectively stops spammers and unscrupulous marketeers from trying to track your behaviour with things like invisible pixels. Apple says that:
iCloud subscribers (aka iCloud+ users) will also be able to take advantage of an unlimited number of random email addresses for use in things like web forms when you are forced to supply an email address to access some service.
While this is a great idea, it’s not likely to thwart businesses that insist on knowing your real email address. Apple’s anonymized email addresses use @privaterelay.appleid.com as the domain name. It’s inevitable that many businesses will simply refuse to accept that domain name in their forms, just as they do with many existing email anonymizer services. So while we applaud the idea, it’s likely that in reality many businesses will easily circumvent this privacy initiative.
4. Safari Gets Some More Security Smarts
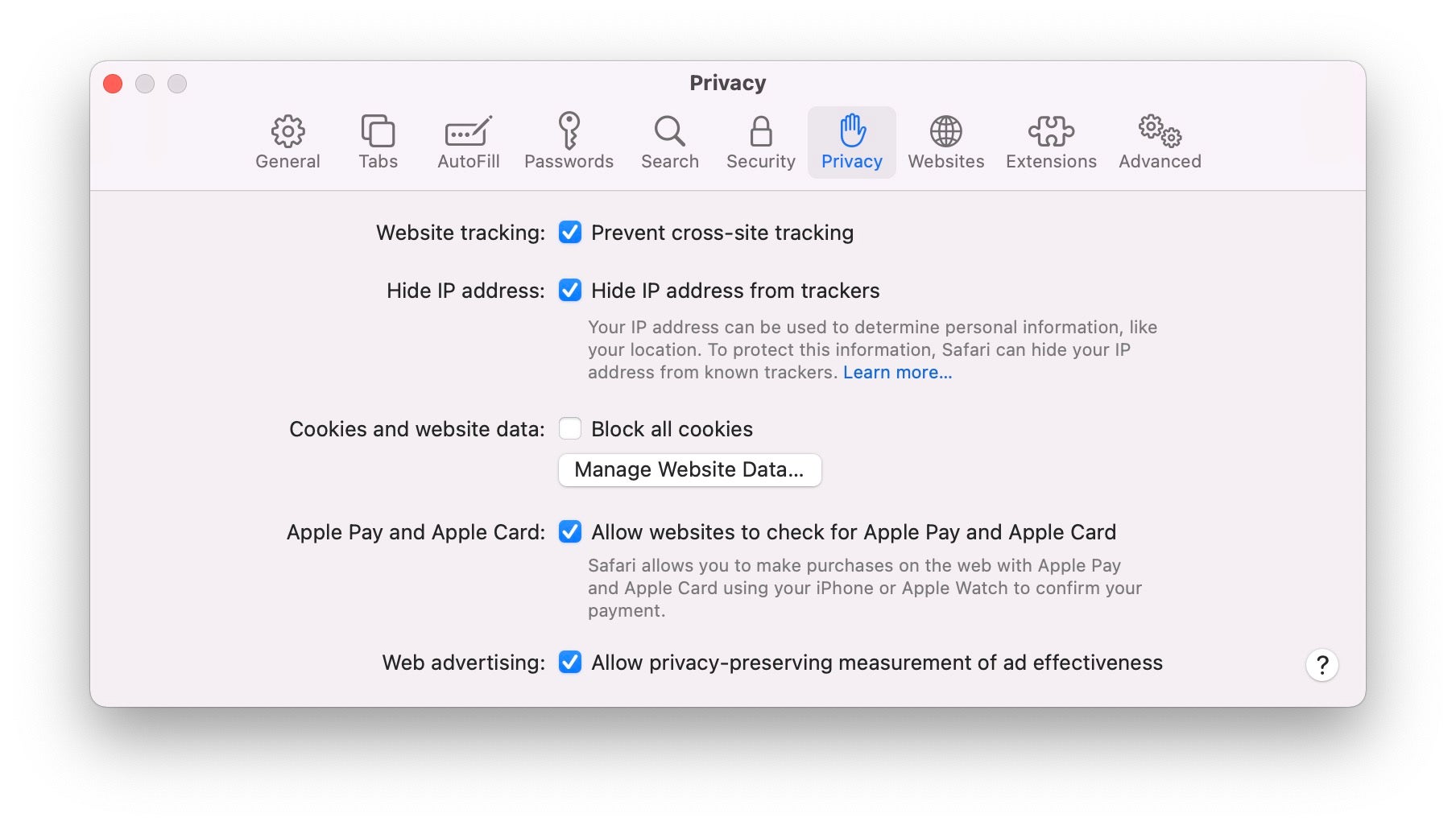
Apple has added some extra security protections to Safari in macOS 12. Among those are the ability to automatically upgrade an HTTP address to its HTTPS equivalent (where available). By ensuring that Safari loads the HTTPS version of websites, you gain the advantages of encrypted communications with that site. HTTPS is pretty much everywhere now, and some browsers like Chrome automatically warn you when you’re not viewing an HTTPS site, but having Safari automatically switch to the encrypted version without user interaction is a nice added feature.
Safari Preferences also gain a new option in the Privacy tab to hide IP addresses from known trackers. Apple calls this “Intelligent Tracking Prevention” and says it prevents trackers from profiling you using your IP address. That’s a freebie quite separate from iCloud+ subscription and Private Relay. In our test, this was turned on by default, but head over to Safari prefs and check if you want to ensure you’re taking advantage of this feature.
5. Passwords Available Here, There and Everywhere
Poor password security has long been a bug bear for individuals and organizations alike, and the standing advice is “use a password manager”. In macOS 12, Apple has taken a stab at stealing some of the market share vendors like 1Password have cornered in recent years with its new Passwords feature in System Preferences.
In the first beta, the new Passwords pane looks pretty much like a replica of the same pane in Safari preferences, and there’s another duplication of password content with the venerable old Keychain Access application. Quite how this is going to develop over time remains to be seen, but about the kindest thing we can say at the moment is you’re spoilt for choice as to how and where you look up saved passwords on macOS Monterey.
The new feature in System Preferences allows you to lookup and manage saved passwords for applications and websites, and to generate verification codes for 2FA in much the same way as apps like Google Authenticator. Interestingly, Apple says that, once setup, the built-in authenticator can autofill verification codes when you sign into a site.
Passwords also offers the ability to import and export passwords to or from other password managers. Perhaps in recognition that many Apple users are also Windows users, the latter can also manage passwords saved to iCloud via a new iCloud Passwords app. There’s even an iCloud Passwords extension for the Edge browser.
Clearly, Apple is making serious inroads into the entire password management space. It will be interesting to see how the existing players in that space respond. Users could be in for a treat with some new 3rd party features if those developers start to feel threatened by Apple’s password grab.
6. Mic Alert – Orange Is the New Green
There’s some interesting developments in macOS Monterey in the way that users interact with AV components and media. We’ll start with the recording indicator. macOS users have long been familiar with the hardware-enabled camera indicator – the green light next to the webcam (aka iSight cam) along the top edge of Mac displays. Similar protections haven’t been available to prevent audio snooping, however. Up until macOS 12, there’s been no obvious way to tell whether the microphone is active or not.
In Monterey, Apple has addressed that with a software-driven recording indicator. Now when any microphone-enabled device is in use, a small orange indicator appears in the menu bar next to the Control Center icon. You can also see which application is accessing your Mac by clicking on the Control Center icon. In addition, as with the current release version of macOS, you can see which applications have Microphone access in the Privacy tab of System Preferences.
7. FaceTime Links – Opening the Door To More ‘Zoom Bombing’?
If there is one software application that will be remembered specifically for its role during the COVID-19 era, odds on favorite to claim that mantle will be Zoom. The video conferencing software has become so ubiquitous that “to zoom” is now a verb much like “to google”. Zoom’s spectacular success has not been without privacy concerns, however, including some high profile cases of “zoom bombing” – unwanted and uninvited guests disrupting what should otherwise be private virtual gatherings.
Apple’s FaceTime app has been around for a lot longer than Zoom and should have a much higher profile, but FaceTime has arguably never really been much use for anything other than contacting a few select friends and relatives that are also Apple device users. In macOS Monterey, Apple has taken steps to bring FaceTime to prime time with new sharing links that allow anyone to join a FaceTime meeting from within their browser – no Apple ID or even Apple device required.
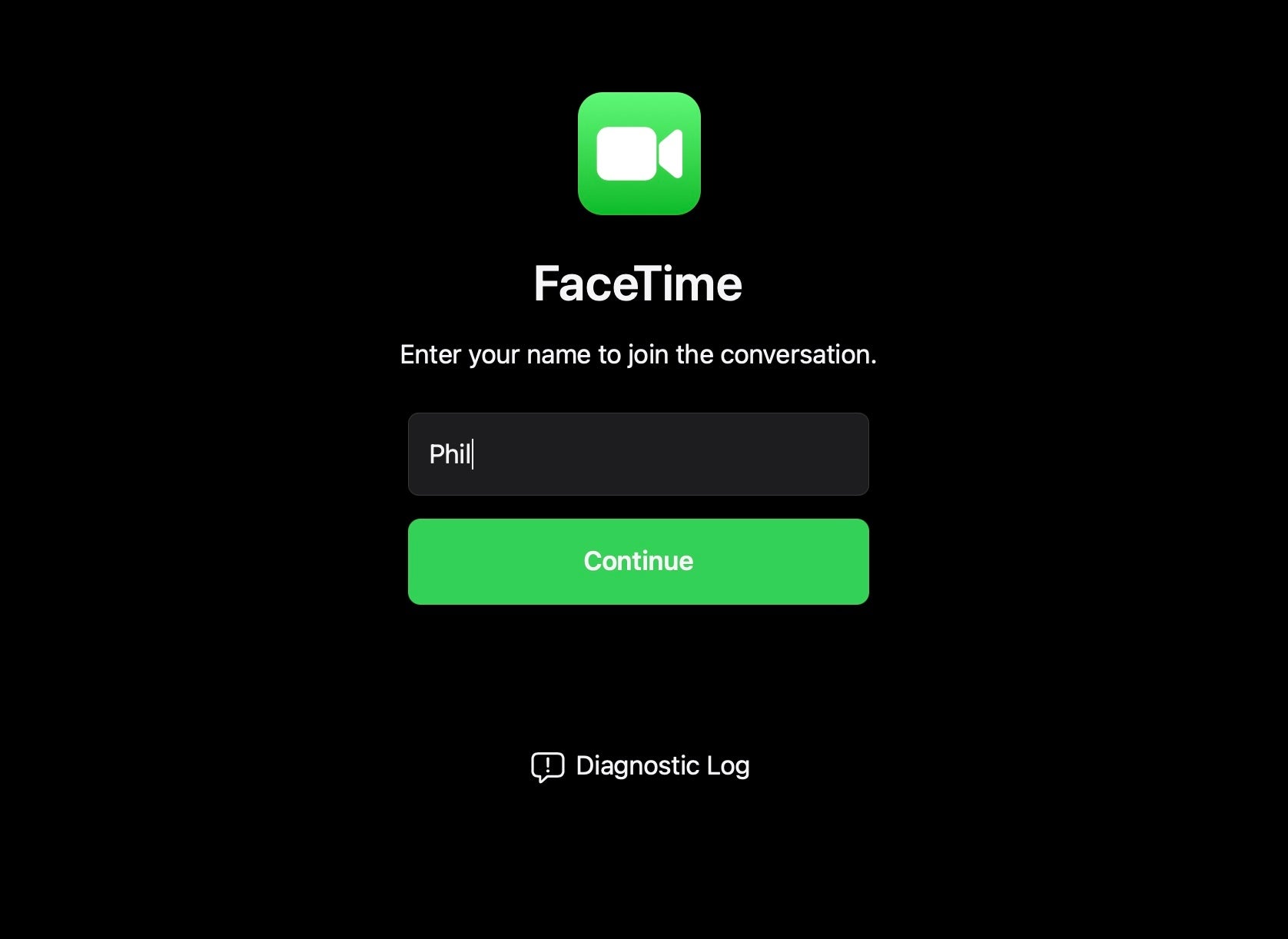
There are, unfortunately, security caveats with such easy access to another person’s virtual world. From unwanted attendees to tech support scammers throwing out links to unsuspecting recipients, we hope that Apple has learned the hard lessons that Zoom and other teleconferencing apps have painfully taken on the chin this past 18 months or so. It’ll be interesting to see what this feature looks like in the public release of macOS Monterey in the fall.
8. Erase All Contents – The Feature We’ve All Been Waiting For?
Selling your Mac or repurposing it within the enterprise from one user to another just got a whole lot easier in macOS Monterey, so long as that’s an M1 or T2-enabled Mac (T2s are those with the touch bar, if you’re losing track of all the Apple designators flying around these days).
Where available, ‘Erase All Contents’ appears in the System Preferences application menu, and thus can be initiated by a user from within their normal login session, no trip to Recovery required.
We can see one really interesting, probably unintended, use for this feature among security researchers. M1 Macs currently lack the ability to virtualize macOS in hypervisor software like Parallels or VM Fusion, and even if you test macOS malware on a dedicated device, there’s currently no easy method to bring that device back to a clean state for the next test, at least not without a tedious trip to Recovery or using third-party software to reinstall the entire system via APFS snapshots. The ‘Erase All Contents’ feature, however, could provide a nice way to do exactly that, a potentially better workaround while we wait, fingers tapping in frustration, for macOS virtualization on the M1.
Meanwhile, Mac admins can rejoice if, as rumored, MDM support for initiating ‘Erase All Contents’ arrives in a later beta.
If, like us, your first thought on hearing of the ‘Erase All Contents’ capability was that it might be weaponized by threat actors as a kind of macOS ‘wiperware’, the word is that the feature can’t be activated from the command line. We’ll have to wait until we’re further into the beta cycle to fully test that, but we’re pleased to know that the thought had already occurred to Apple, too.
9. Legacy Data – Now Your Secrets Don’t Have To Die With You
Data security isn’t only about preventing unauthorized access. It’s also important to make sure we can maintain access to our data over time, and that includes transferring our data to others when we pass on. To that end, there’s two changes in macOS 12 related to Apple IDs, the “one stop shop” sign-in credential for accessing Apple services across their range of devices, including Macs.
The Account Recovery Contacts feature is a means of designating one or more trusted persons who can help a user to reset their passwords and regain access to their Apple ID account in the event they lose access through forgotten or inaccessible passwords. We’re not all mavens of perfect organization, and many of us support users, family and friends who struggle with the complexities of technology, so this will certainly be a welcome feature for many.
The Digital Legacy program is a seperate feature that allows users to designate other people to “pass their data on to” in the event of death. People designated as “Legacy Contacts” will be able to access all accounts and personal information of the deceased. It’s a great idea and something that many people have been drawing attention to for some time. Just a word of caution: be certain you’re not hoarding any personal or family secrets on your Apple devices that you don’t want discovered after you’re gone.
10. Live Text – A Data Exfiltration Dream Come True?
Those action/spy movies where someone sneaks into an office and quickly photographs lots of confidential files before the ‘victim’ returns always had one gaping flaw: imagine being the poor grunt back at Spy HQ who has to start wading through all those photos and laboriously (and accurately) transcribe them all into text. How long would that even take? Surely a lot longer than the movies would have us believe.
We’ve had expensive and not entirely accurate OCR (Optical Character Recognition) programs for decades, and some 3rd party note-taking apps have been offering more convenient solutions for a while, but in macOS 12, Apple is promising to take OCR to the next level with its new Live Text feature.
According to the blurb, text in photos is now “completely interactive”, so you should be able to use copy and paste just like in a text document. Live Text is available in Photos, Screenshot, Quick Look, and Safari, but…only so long as you have an M1 Mac.
OK, rapid data exfiltration worries aside, that makes life a lot easier for those of us with legitimate use-cases where we need to do things like screenshot slides from video presentations and the like. And the grunt at Spy HQ just breathed a huge sigh of relief.
11. New Automation Possibilities with Shortcuts for macOS
The Mac has always been way ahead of any other platform when it comes to automation. AppleScript is the reigning deity in that regard, with Automator playing a useful but largely underutilized secondary role. With macOS Monterey, Apple brings iOS’s Shortcuts to the Mac in what looks like a bid to reinvigorate automation with an eventual successor to Automator.
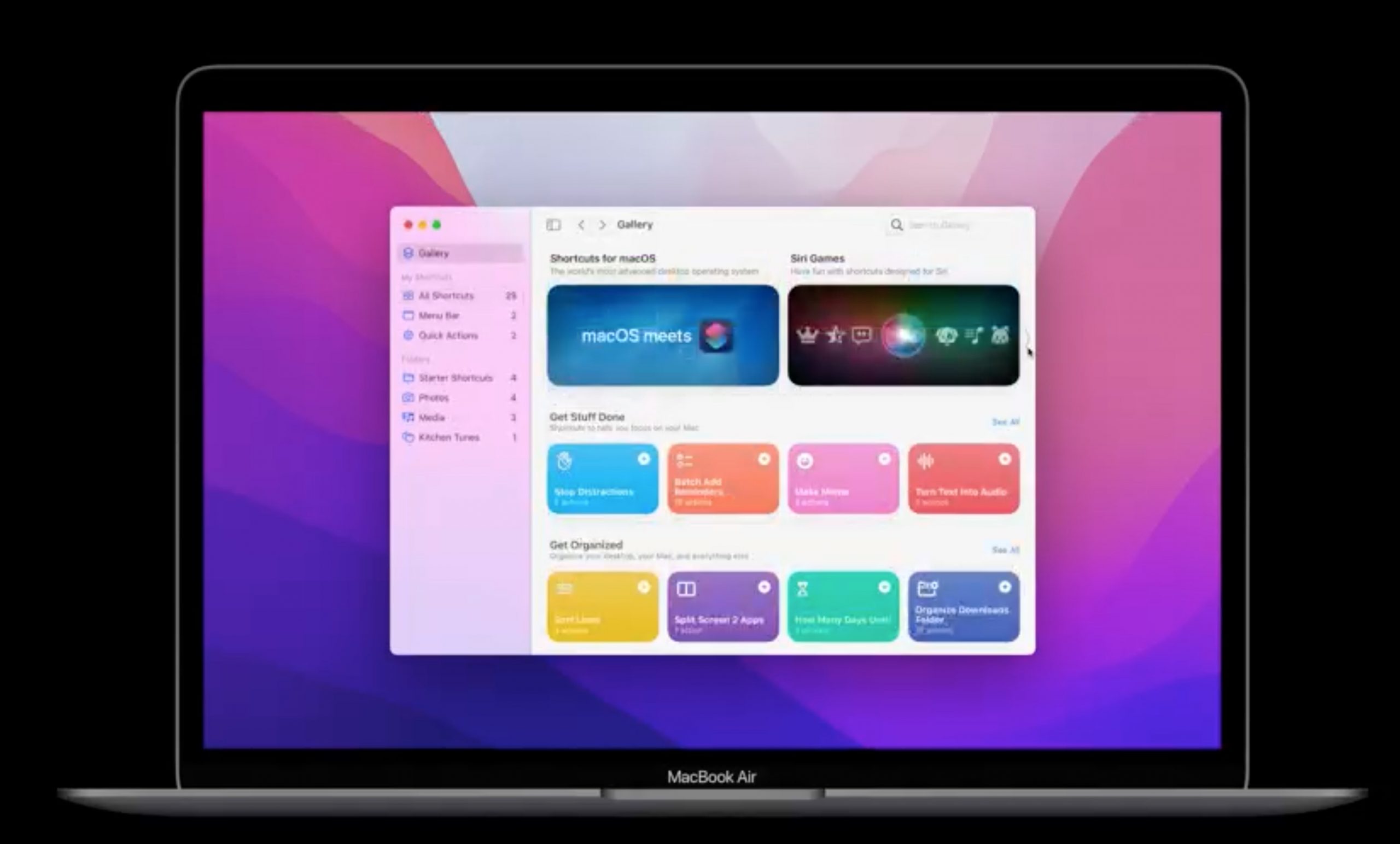
Early indications are that Shortcuts will be just as powerful as Automator. Monterey includes a migration tool to convert most Automator workflows into Shortcuts. Just like Automator, Shortcuts can run Shell Scripts and AppleScripts, manage files, copy content and more.
The downside of automation is, of course, security. Being able to kick off a complex chain of events involving files, folders and user contents leaves open myriad possibilities for abuse, particularly if malicious actors can easily distribute actions that will do such deeds for them.
With Shortcuts, Apple has built in lots of sharing options so that users, organizations and developers can easily distribute Shortcuts to others. To prevent malicious use, Apple notarizes Shortcuts shared either via iCloud or if they are exported as standalone files. Shortcuts files are code signed with the identity of the person who sent them, and there’s a Shortcuts command-line tool if you need to re-sign a Shortcut before sharing it with others.
We are big fans of automation, and we look forward to exploring what can be done with Shortcuts as we get further into testing macOS Monterey.
12. And What About Application Security?
It’s not always true that no news is good news. Just as at this point last year we had to say “nothing to see here”, so with macOS 12 Monterey there are no new announcements regarding Apple’s security technologies to block, detect and remove malware (Gatekeeper, XProtect and MRT.app, respectively).
Given the fallibility of those technologies, recently admitted by Apple itself, that’s perhaps a bigger surprise this time around than it was with macOS 11 Big Sur.
Conclusion
It’s early days for macOS Monterey, and there’s a lot to test to see how these new features fit into our daily routines, but we hope this post has given you a heads up on what to look out for as far as security is concerned.
SentinelOne is, of course, already busy working on support for macOS Monterey. As always, our standard disclaimer applies to beta software. We are working to ensure that the SentinelOne Agent will be released up to 45 days after Apple announces the public release of macOS 12. Depending on the type of changes introduced in this new version, our goal is to shorten this time if possible and to provide early availability releases for testing with Apple Beta releases. Interested customers can find out more through the support portal available from within their Management console.


