Threat actors are constantly evolving, consistently developing the tools, tactics, and procedures (TTPs) they use in attacks. In today’s threat landscape, enterprises of all sizes and industries find themselves pitted against professional cybercriminal gangs, advanced persistent threat (APT) groups, and even nation-state actors – all of whom are leveraging faster attack methods than ever before.
In addition to sophisticated TTPs and how organized many cybercrime-as-a-service models have become, enterprises also face the reality of how quickly active threats can become full-blown incidents. Speed, in both cybersecurity and cyberattacks, is the key metric to pay attention to as it defines the success of either the attacker or the defender.
This blog discusses the metric of speed in context of modern threat actors, their methods, and how enterprise security teams can shave off critical seconds and minutes in their own detection and response processes.

Threat Actors Are Picking Up Their Speed
Technology has changed dramatically in the last few years alone, becoming smarter, faster, and more advanced. While enterprises use the latest software and tools to further their businesses, threat actors have done the same to level up their attack methods.
Ransomware Attacks
Consider one of the most significant takeaways from Mandiant’s latest M-Trends report: The global median dwell time – the time marking the beginning of an intrusion and the moment it is identified – is dropping year over year. At a mere 16 days of average dwell time for 2022, this may seem like a positive development as threat actors are spending less time inside a system post-entry. However, skyrocketing counts of ransomware attacks on global businesses give a good indication as to why average dwell times are on the decline.
Though some of the reduction in dwell time is attributed to improved detection and response capabilities, ransomware has become a digital pandemic, targeting victims in all industry verticals. Given its high earning potential for a relatively short attack time frame, ransomware attacks are highly lucrative for threat actors and are protected by security experts to continue rising in both frequency and severity.
Drive-By Download Attacks
As their name suggests, drive-by downloads are stealthy, fast, and often happen before the victim even knows what’s happening. This type of cyberattack is employed by cybercriminals to infect a victim’s device with malware without their knowledge or consent. It typically occurs when they visit a compromised website or click on a malicious link embedded in an email or advertisement.
The attack then takes advantage of vulnerabilities in web browsers, plugins, or operating systems, allowing the malware to be automatically downloaded and executed on the victim’s device. Drive-by downloads require only the bare minimum of a victim’s interaction, making them a potent tool for spreading malware, stealing sensitive information, and gaining unauthorized access to systems.
Mass Scanning For Vulnerabilities
Based on new research, security defenders have a real race against the clock to patch new vulnerabilities. Researchers have found that threat actors start to perform mass, internet-wide scans for vulnerable endpoints within just 15 minutes after a new CVE is disclosed. Threat actors consistently monitor vendor bulletins and software update channels for the latest announcements on vulnerabilities and proof of concepts that they can leverage in their next attack. Oftentimes, these fresh vulnerabilities provide them with the capability to perform remote code execution (RCE) and gain access to corporate networks.
Patch management is a continuous and, for many organizations, arduous task that requires security teams to try to keep up with all the latest security threats and issues in various operating systems. Since performing these internet-wide scans do not require a deep skill set, even low-level criminals are able to take advantage, sometimes even selling their scan results to more experienced actors.
Zero-Day Exploits
Threat actors are gaining momentum on how quickly they can exploit zero-days. In a recent Vulnerability Intelligence Report, researchers cited time-to-exploit as being the critical metric for security practitioners. Over the past three years, the time measured between disclosure and known exploitation has decreased steadily, going from 30% of vulnerabilities exploited in the wild within one week in 2020 to 56% found exploited within one day in 2022. Zero-days are most often exploited to provide initial access for ransomware gangs.
Growing Availability of Off-The-Shelf-Tools
Apart from APT groups, full-fledged ransomware gangs, and nation-backed threat actors, low-level cybercriminals are taking their shot on enterprises due to the widening availability of ready-to-use hacking tools. These tools, including exploit kits, infostealers, scanners, password crackers, and attack simulation tools, are commonly available on forums and darknet markets and significantly lower the barrier to launching serious cyberattacks.
As the market for selling pre-made tools continues to expand, cybercriminals with little to no technical expertise are now able to quickly find and purchase pre-existing scripts to launch attacks on computer systems and networks.
Deciphering How Actors Move Across The Cyber Attack Lifecycle
Though cyber threat actors are moving swiftly, there are ways for enterprise businesses to stay ahead and safeguard their critical data and systems. Understanding how actors maneuver before and during their attacks allows defenders to put in the right safeguards in place.
- Planning Phase – Before the act of attack, threat actors will select their target and work to identify exploitable aspects of their operations. This refers to any low hanging fruits such as unpatched vulnerabilities, misconfigurations, administrative users on unprotected devices, and more.
- Initial Intrusion – Based on the findings from the planning phase, threat actors tailor their intrusion technique based on the weaknesses of their victims.
- Enumeration Phase – Once inside, threat actors move fast to situate themselves within the system, understand the limits of their current permissions, and establish an estimate on what privileges they require to start moving laterally. Time is of the essence in this phase as actors start to establish their foothold and upgrade their access.
- Lateral Movement – Using their new credentials, the actors are able to spread deep into the affected system. Here, their main goal is to distribute their malware/toolset, exfiltrating and encrypting data as they go.
- Objective Completion – After deleting or corrupting backups and local files, actors prepare to ransom their victim.
Based on the cyberattack lifecycle, the intrusion and enumeration phases open up a critical window for proactive action by cyber defenders. During these initial stages, the attackers have not yet deeply infiltrated the compromised network or blended in with normal network traffic. If a threat actor manages to make it to the lateral movement phase, detection becomes much more challenging. Threat actors use evasion tactics to avoid detection, embedding themselves deeply within the network. Living-off-the-land techniques are most often used in this phase, leveraging legitimate processes and tools already present in the environment to strengthen their foothold.
Since the time span between intrusion and lateral movement is rapidly shrinking as threat actors become more sophisticated and well-equipped, the primary goal for cyber defenders is to focus on detecting the first signs of compromise during the enumeration phase and isolating the threat before it can cause significant damage.
Autonomous Tools Take the Toil Out of Triage
Managing such a challenge, however, is often beyond the resources of a security team tasked with manual triage of a flood of alerts and uncontextualized event data. That’s why autonomous, AI-powered EDR and XDR solutions are the new go-to tools for analysts, threat hunters and incident responders alike.
A modern security tool like SentinelOne Singularity not only autonomously deals with known malware threats – from detection right through to mitigation and even rollback in the case of a ransomware attack that gets through – but also provides incident responders with contextualized data to tackle targeted attacks.
With automated contextual enrichment from tools such as Singularity XDR, IR teams can take advantage of insights from aggregated event information that combines all related data gathered from multiple tools and services into a single ‘incident’, without adding extra tools or more people. Out-of-the-box integrations and pre-tuned detection mechanisms across the security stack help improve productivity, threat detection, and forensics.
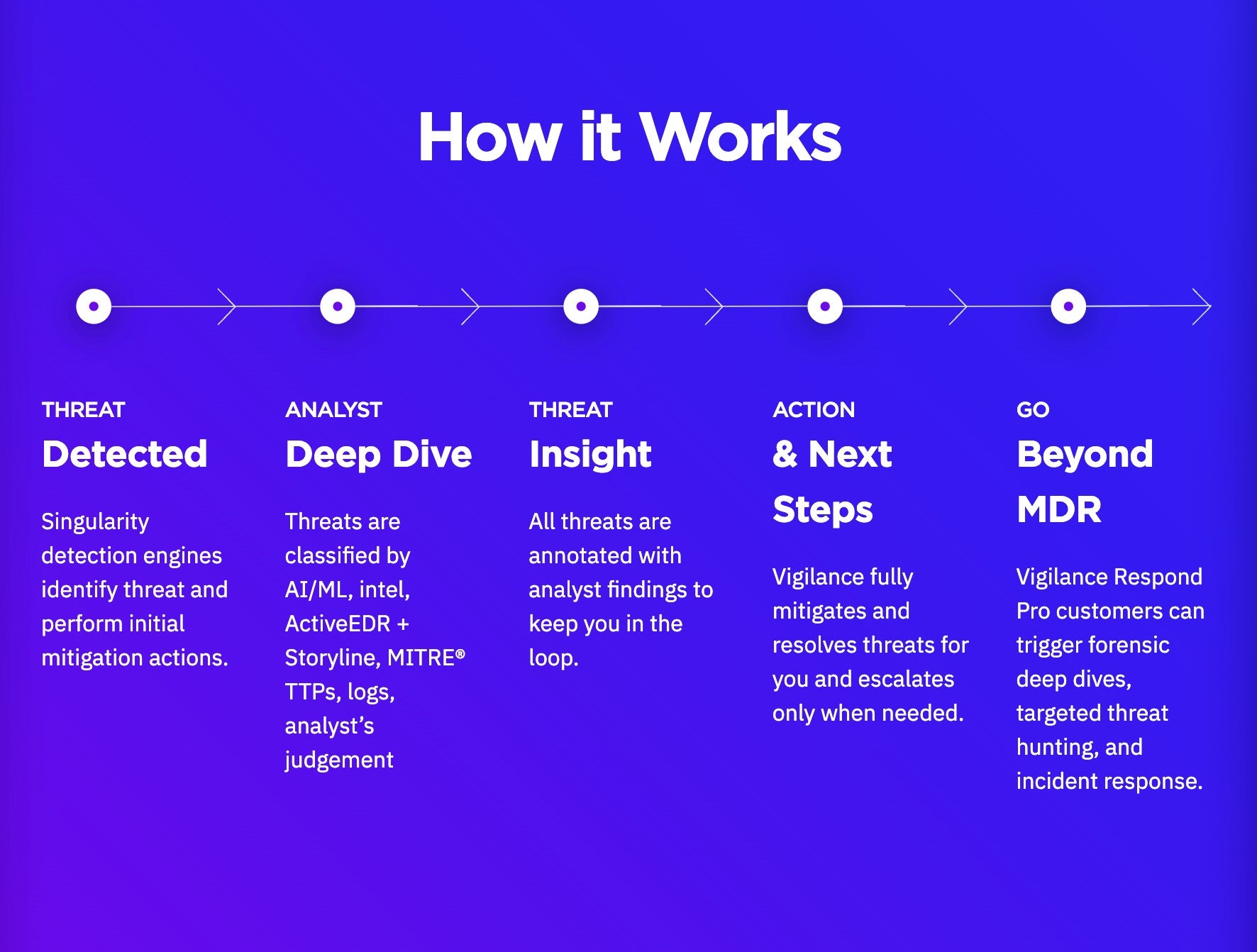
SentinelOne Vigilance Respond | Our Approach to Managed Detection & Response (MDR)
While powerful, such tools can be supplemented by Managed Detection and Response services for an even higher level of security. Organizations across the globe rely on SentinelOne’s Managed Detection and Response (MDR) service, Vigilance Respond, to stop threat actors from reaching the lateral movement stage in attacks. Utilizing SentinelOne Singularity, Vigilance Respond defends networks against cyberattacks instantly and monitors customer environments 24/7/365, hunting for advanced threats and providing faster mean-time-to-response (MTTR) rates.
Vigilance Respond works by providing machine-speed detection technology run by dedicated analysts working around-the-clock. It also allows organizations to adapt instantly, and at scale, in today’s ever-shifting threat landscape, closing the gap between intrusion and lateral movement and neutralizing the threat actor before they can begin to spread deep into a target’s systems.
Vigilance Respond offers these services to ensure businesses are safeguarded:
- Active threat campaign hunting for APTs
- Alerting and remediation guidance for emerging threats
- Incident-based triage and hunting
- 24/7/365 monitoring, triage, and response
- Security Assessment (Vigilance Respond Pro)
- Digital Forensics Investigation & Malware Analysis (Vigilance Respond Pro)
Conclusion
In the realm of cybersecurity, speed matters. It can be the deciding factor between successfully thwarting an attack or suffering substantial damage. As technology evolves and threat actors become more adept at exploiting vulnerabilities, enterprise leaders are investing in strategies focused on swift and proactive cybersecurity response measures.
Ultimately, speed in cybersecurity is about staying one step ahead of the adversaries. It requires a proactive approach, continuous monitoring, and real-time threat intelligence. By prioritizing speed, organizations can enhance their ability to detect, respond to, and mitigate cyber threats, ensuring a stronger and more resilient security posture.
Learn more about how SentinelOne Singularity and Vigilance Respond can help safeguard your business by contacting us or requesting a demo.