In our recent article Exploring an NTLM Brute Force Attack with Bloodhound, we explored how attackers are still abusing the NTLM authentication protocol. In this post, we will elaborate more generally about basic attacks against SAM, LSA secrets, SYSKEY and LSASS. We will explain how attackers use these to get credentials from a Windows machine in order to highlight the importance of having these methods monitored by security teams. Although these are well-known and relatively simple credential stealing attacks, they are still used in the wild, which suggests that there are security teams overlooking these tried-and-trusted techniques.
Seeking clear text credentials via LSASS or acquiring the SAM for the NTLM or LSA keys for its secrets has great value to attackers. Just having access to a machine won’t satisfy an attacker when they can do far more with valid credentials at their disposal across multiple steps of the ‘Kill Chain‘.
Consequently, credential dumping is frequently used by attackers during lateral movement. Having obtained account login names and passwords, attackers can spread further through an organization’s network, access restricted data, and execute commands and programs with higher privileges.

Overview of Credentials Exfiltration
At a high level, a potential attacker will want to do the following:
1. Obtain the NTLM hash(s) for offline cracking and manipulation.
- HKLMSAM: contains the NTLMv2 hashes of users passwords
- HKLMsecurity: contains cached domain records LSA secrets/LSA keys
- HKLMsystem – aka SYSKEY: contains keys that could be used to encrypt the LSA secret and SAM database
2. Dump LSASS, either to get the clear text password, or just the NTLM hashes (depending on the version of Windows being targeted).
Note: the functionality and the information stored may vary. For example, there are differences between machines that are in an Active Directory domain versus those that are not.
Now let’s dig into the details of the different components mentioned above.
1. SAM: HKLMSAM
The Security Account Manager (SAM) database is where Windows stores information about user accounts. It stores usernames and hashes of user passwords, and it is used to authenticate users when they try to log in and provide their password.
Hash length and complexity vary according to the algorithm used to encrypt the password. This may be a simple DES-based LM (Lan Manager) encryption algorithm or one of the two versions of the NTHash algorithm: NTLMv1 or NTLMv2, both of which output 32 hexadecimal digits and are derived from the MD4 digest.
One of the most common methods of gaining user passwords is to dump the SAM database either with a tool that can extract the password hashes or by directly copying the registry to a file [reg.exe save hklmSAM] and working on it offline with a software utility to extract the stored user account password hashes.
Once the LM or NTLM hash has been gained, an offline brute force on the password hash can be performed, as explained in more detail later in this post.
2. LSA secrets: HKLMSecurity
LSA secrets is a storage used by the Local Security Authority (LSA) in Windows.
The purpose of the Local Security Authority is to manage a system’s local security policy, so by definition it means it will store private data regarding user logins, authentication of users and their LSA secrets, among other things. Access to the LSA secret storage is only granted to SYSTEM account processes.
LSA secrets stores system sensitive data, such as:
- Users passwords
- Internet Explorer passwords
- Service account passwords (Services on the machine that require authentication with secret)
- Cached domain password encryption key
- SQL passwords
- SYSTEM account passwords
- Account passwords for configured scheduled tasks
- Time left until the expiration of an unactivated copy of Windows
and much more. Early implementations of LSA secrets were quickly cracked and tools like Mimikatz can also dump LSA secrets from memory and registry hives on some versions of Windows.
3. SYSKEY: HKLMSystem
Syskey, also known as the SAM Lock Tool, existed in older Windows versions. This feature’s purpose is to encrypt the Security Account Manager database (SAM) and thus afford an extra layer of protection to the SAM during machine boot up.
Syskey only protects the security data when the operating system isn’t running. When the OS is up, the Syskey value is loaded into memory so it can later decrypt the SAM. HKLMSAM is linked to the SECURITY subkey under HKLMSECURITYSAM.
The Syskey feature has been discontinued since 2017, but it can be found under hklmsystem on relevant versions of Windows where it is turned on and configured.
4. Dumping Credentials with LSASS
Until the release of Windows 8, using Mimikatz on Windows could get the credentials in clear text from the Local Security Authority Subsystem Service (LSASS).
Several fixes were suggested over time, each of which hardens LSASS usage making it harder to get even the hashed password. In Windows 10 Enterprise, Credential Guard is also available to isloate the LSASS process even from users with SYSTEM privileges.
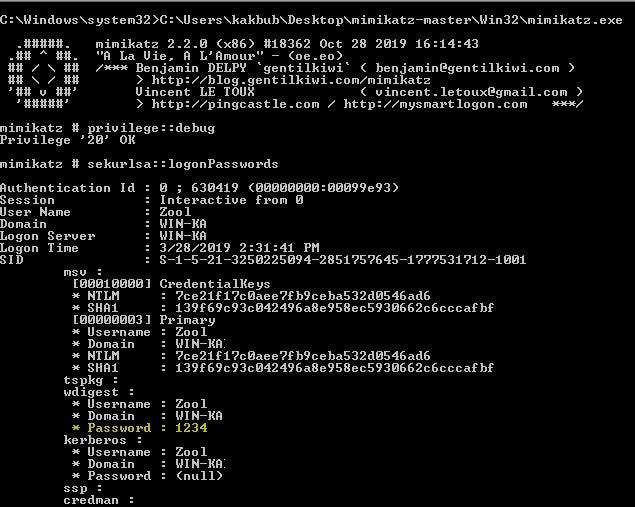
Mimikatz password extraction on Windows 7:
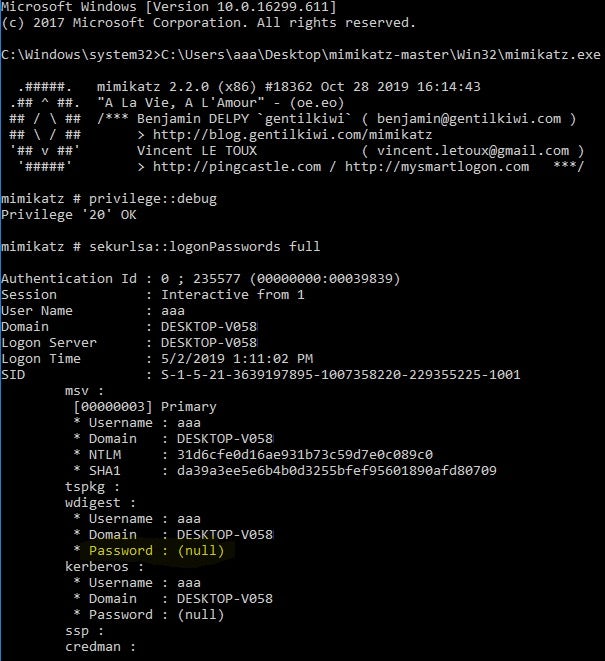
We can see the changes when running the tool against Windows 10. We don’t see the clear text password, but we do acquire the NTLMv1 hash.
Password Extraction from NTLMv2 Hash
There are many ways to get the NTLM hash if you do not have local access to the target machine.
The Responder tool is one of the more popular tools used for this task.
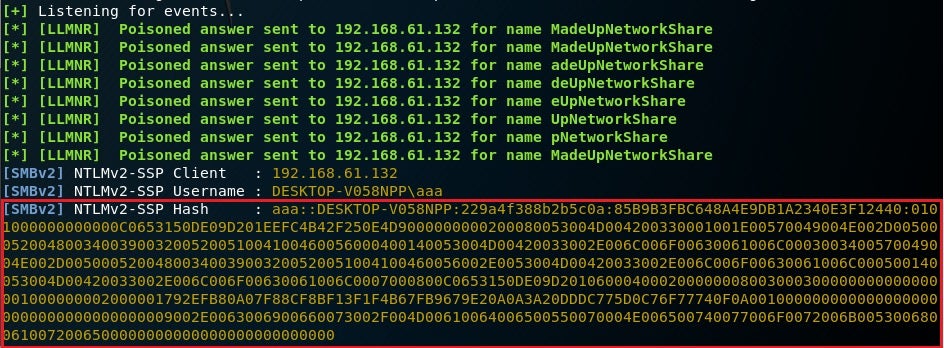
Example of the NTLMv2 hash that we can output with the Responder tool :
admin::M57oDBrlht:08ca45b7d6da58ee:88dcbe4346168966a153a0064958dae6:5b6740315c7830310000000000000b45c67103d07d7b95acd12dea11230e0000000052920b85f78d013c31cdb3b92f5d765c783030
This tool has many capabilities, but one that is relevant here is the ability to prompt users for credentials when certain network services are requested. This can result in clear text passwords or password hashes.
For this attack the tool usage is for capturing LLMNR packets and extracting the hash from the challenge/response. We set up the tool to listen for the right packets on the network, and then we try from the victim machine to get to a network resource that isn’t actually there. This way we would be able to capture the traffic and from there we would get the NTLM hash.
From a Windows machine I was trying to access a non existent share with the name “MadeUpNetworkShare”, and the tool ran on a machine on the same network and recorded the challenge/response, which disclosed the NTLM hashes.
How Can We Use Password Hashes?
Now that we have the hash, we have a couple of options to try and extract the clear text password.
Dictionary attack/Brute force attack – This method involves the use of a wordlist to compare against the passwords. We can use publicly available tools for this kind of work such as John the Ripper, hashcat, Cain & Abel, and Ophcrack, among others.
Rainbow table attack – This is more suitable when trying to crack a hash, but it relies on having an existing database of possible passwords and their pre-computed hashes.
Example of cracking NTLMv1 password with rainbow table (taken from https://crackstation.net/):
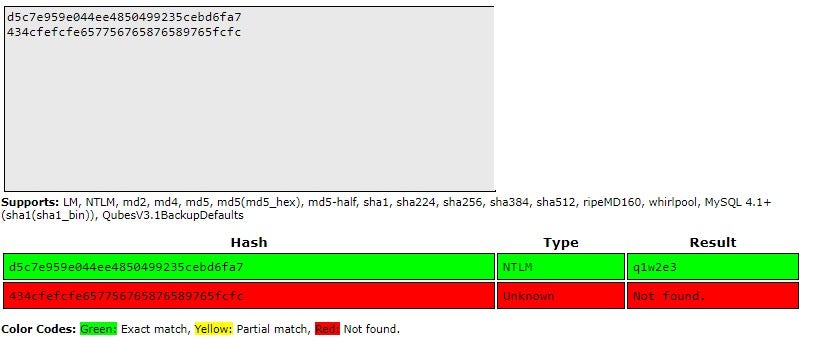
Note that only known, unsalted hashes could be reverted back from hash to password in this way.
If the password is too hard to crack, we have other options such as a pass the hash attack. This involves leveraging any services on the network that authenticate by using a hash of the password rather than the password itself. A good example of this is psexec and other services that communicate over SMB.
Recommendations to Prevent Credentials Exfiltration
In order to prevent credential dumping and exfiltration, it is recommended that organizations ensure that any older systems on the network do not still have LM encrypted passwords in the SAM database, and that LM (disabled by default) has not been enabled on newer systems. LM passwords use only a limited character set and are trivial to crack.
It is also recommended that NTLMv1 be disabled. It is relatively easy to extract the password from an NTLMv1 hash, and as long as it wasn’t configured otherwise, most services that will work with NTLMv1 should also work with NTLMv2.
One way to ensure that both LM and NTLMv1 are disabled is from the GPO page:
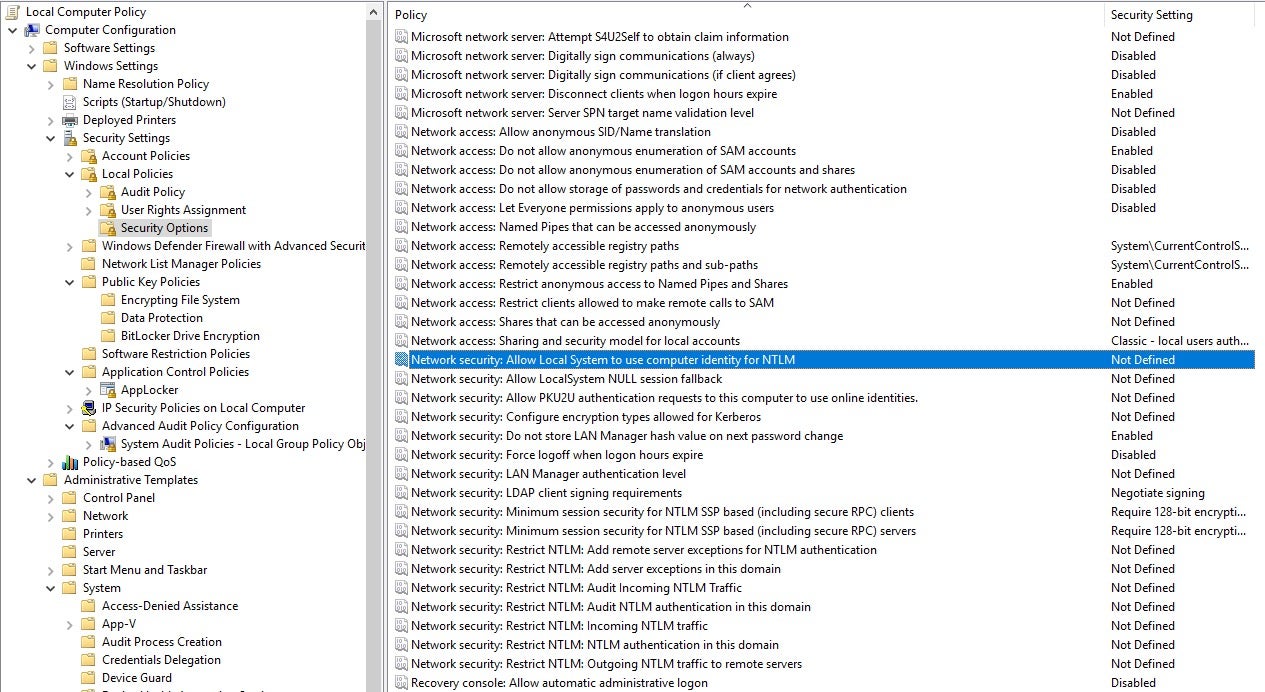
Make the following configuration changes in the GPO to prevent usage of NTLMv1:
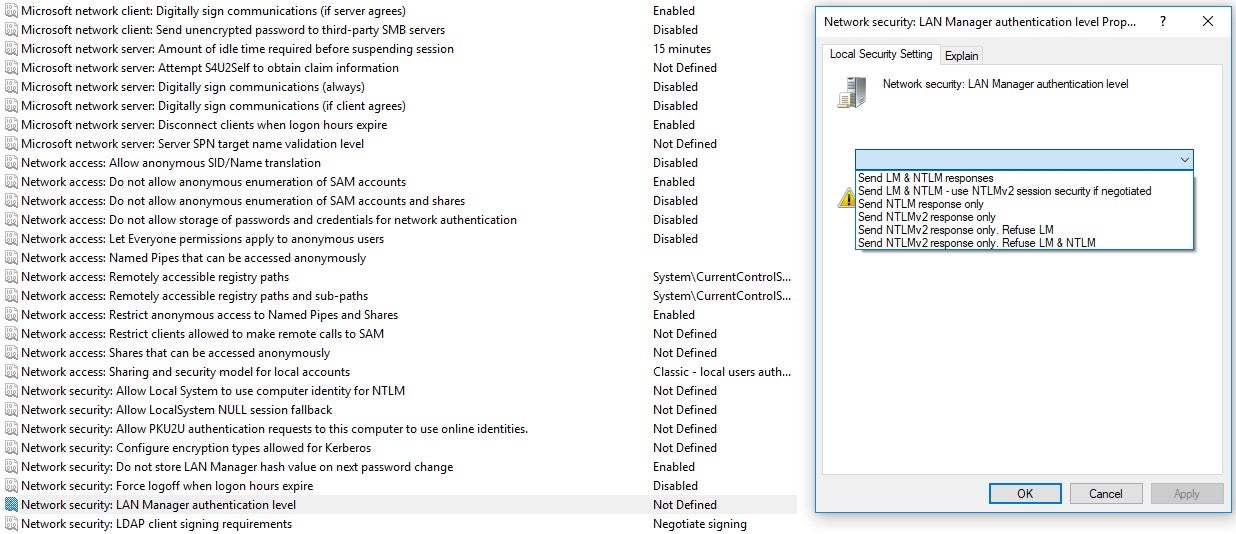
It’s not trivial to crack the NTLMv2 hash if the password is long and unique. Also, having the hash won’t necessarily give an attacker an advantage if there are no services that authenticate with NTLM hashes.
It is also recommended that Credential Guard be enabled on Windows 10 machines that support it for extra protection for NTLM and Kerberos credentials.
The most effective way for an organization to reduce its attack surface and protect against credential exfiltration is by deploying a next-gen security solution like SentinelOne that uses machine learning and Active EDR.
Final Thoughts
These basic attacks can be prevented by paying attention to your network architecture and the services being used in your environment. In particular, these kinds of attacks are most effective against Windows 7 (and below) targets, which despite their EOL status are still prevalent across many enterprise networks. These days, many organizations are rightly using more secure implementations like Kerberos in a group domain to avoid exactly the kind of vulnerabilities discussed here, as well as deploying a trusted, next-gen endpoint security platform to protect their devices and network
MITRE ATT&CK References
Credential Dumping – T1003
Pass the Hash – T1075
Brute Force – T1110


