Summary
A new version of the CryptXXX family of ransomware has been discovered which is spreading through spam and perhaps other means. This latest iteration fixes flaws in its file encryption methods which prevents use of free decryption tools and makes it impossible to decrypt files without paying the ransom.
CryptXXX is an actively developed ransomware family. At the time of writing, this particular variant has led to the ransom payment of about $50,000 worth of Bitcoin. With this kind of success, it’s likely we’ll continue to see this family and other ransomware families continue to grow and evolve. Some factors which may contribute to this are the increasing reliance on computers to store and process valuable information and the increasing popularity of Bitcoin which is semi-anonymous, works globally, and is difficult to regulate because it’s completely decentralized.
Packed Sample
- Filename: F0F3.tmp.dll
- File size: 310,272 bytes
- MD5: a89f7c458d358615f2d3f0642141febb
- SHA-1: 30fcabddf49cc4d8f153f25dcf30e8aec1ac7161
- SHA-256: fdbeed00cacca229607aa70ee3538c92d57bab7b29cbce0f1c05c1f84c68aa20
Unpacked Sample
- File size: 165,867 bytes
- MD5: 995e646c3422407227da96ca888ea324
- SHA-1: 41706d9153eef3a2f5795e58a334b00fa3f40e8d
- SHA-256: d9888e38a2f813139331dbac1f07fede19c784a4c2212cff8c17c83a40a2f84d
Similar CryptXXX Sample SHA-1 Hashes
- 1b7fb5c5b9a7e2994110945c85c955c8829183ee
- 1ed8fc897d2fa7dcd4402b2646fb041f881fed1b
- 2ffbc8fc585c7de745bb7cda981abc905aa37304
- 30fcabddf49cc4d8f153f25dcf30e8aec1ac7161
- 3c3fc89bb266a79b24c5346fbab879694d2b125e
- 4c505c31a34b4292875d8590e90c9f09bd76ab04
- 509a607e614472dbe1f549c45fd63b0b8c5cd905
- 6514f4e8d9cdc36ba0f944c8ae066208e9bf7c38
- bbd87b53472c990e9e41e4fcfd3a1b3162f14b6a
- df31afdc271d968bf001dfdada2ffb87f00ed59a
- e2b49178abfb1f1c731f74c884d30c60769de696
- e40f9fabac42822304066725bf0710c2854f91f1
- fac67e02f3929d9c0dd230aed19192143bededea
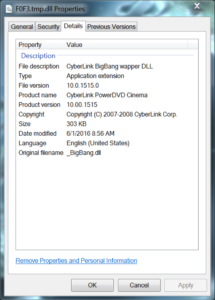
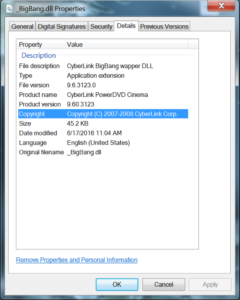
A quick check of the malicious DLL’s properties reveals it’s using what appears to be the details of a legitimate DLL named _BigBang.dll from a product called CyberLink PowerDVD Cinema. After hunting down a legitimate copy of _BigBang.dll, though of a slightly older version, it’s clear that the details have been copied exactly.
  |
  |
|---|
_BigBang.dll
- MD5: ea6586e9ba709a18901ae0434d59c3f4
- SHA-1: f914db2bb213d7bb5af9bc3a4c10d868e9a32075
- SHA-256: 275ebe2a72951737a3502d00f967c87d4f2fba03c4828d27270ab0f88a4d8f65
We’ve shown in another CryptXXX blog post that a previous sample of CryptXXX copied the details from a legitimate Microsoft DLL. The perfect fidelity of the reproduction of these details seems to suggest that the process is performed programmatically, perhaps as part of the build or distribution process.
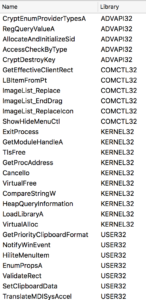
The unpacker’s imports looked mostly benign, with only a few crypto-related functions to raise an eyebrow.
  |
  |
|---|
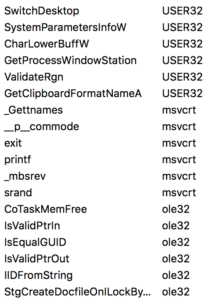
The list of exports is unusually large for a program with seemingly no actual legitimate functionality:

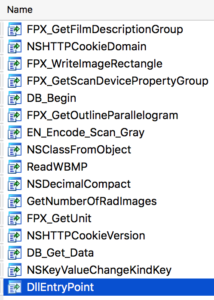
In both imports and exports there are many functions related to image processing which do not seem to serve any real purpose. Further, the imports and exports are completely different from those of the legitimate _BigBang.dll. It may be safely assumed these functions are present to thwart analysis.
Unpacker Behavior
The unpacking happens by allocating memory for the encrypted payload with VirtualAlloc and then copying over the encrypted bytes.


After that, the payload is decrypted, but it is still compressed.

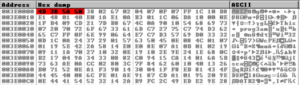
I was looking for an “MZ” header but instead found “M8ZP8” and a partially readable “This ? progr3am …” string common to all Windows executables. The “M8ZP8” header is consistent with aPLib compressed PE file. This Python script contains an implementation of the algorithm and a technical description of how it works. I dumped the memory segment containing the compressed payload, trimmed all but the last null byte and successfully decompressed it using the aforementioned Python script. The resulting file could be analyzed in IDA but was not complete and did not contain a valid import table.
Once the payload is decrypted, the unpacker creates a file at the path C:\PROGRA~2\Z (c:\ProgramData\Z). Then, the file is checked using kernel32.GetFileType to determine if it’s a FILE_TYPE_CHAR. If it is, the code eventually terminates without executing the malicious payload. After that, the current time, file name, and \r\n are combined into a string and written to the Z file. For example:

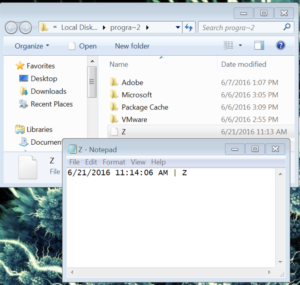
The file is deleted shortly after the string is written to the file. It’s not clear what the purpose of this is. It could be to create noise in the API calls to deter analysis.
Next, the unpacker determines the location of the Startup by querying the registry key: SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders\Startup. By default, on Windows 7, this path is C:\Users\<username>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup. This path is used by the unpacked code to place an HTML ransom note which is opened whenever the computer is started to ensure the victim knows how to recover their files.
The analyzed sample was originally executed from a Windows shortcut (.lnk file). The shortcut points to rundll32.exe F0F3.tmp.dll,MSX3. Arguments for rundll32.exe can be delimited by commas or spaces, and this particular command will load F0F3.tmp.dll and then execute the MSX3 function. The MSX3 function is not present in the unpacker, so it must be part of the unpacked payload. Knowing this, it was possible to dump a fully-unpacked payload by first watching calls to VirtualProtect since it’s needed to change the permissions on memory segments containing the newly unpacked code. Once there are calls to VirtualProtect on the packer’s memory segments, I created a breakpoint at GetProcAddress since it is needed to determine the address of the MSX3 function.

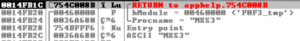
Shortly after the MSX3 address is retrieved, execution jumps to that address and the file encryption and ransom behavior begins.
Payload Behavior
The payload appears to have been compiled using Delphi because of the existence of a CODE section (rather than .text). It also contains several imports which seem to be used for DNS, POP3 and SMTP. However, these functions are called through a different entry point than MSX3.

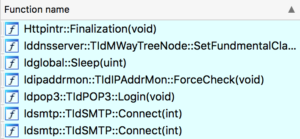
The victim’s files are encrypted using a combination of RSA and RC4. The encrypted versions of the files have a file extension of .cryp1. The previous version of CryptXXX used .crypz and the version before that used .crypt. Also, previous versions had a flaw in how they implemented the encryption which allowed certain tools to decrypt the files without having to pay the ransom. However, this version does not have this flaw.
Ransom notes are created in each folder where a file is encrypted. One is in text and the other is in HTML. The text ransom note contains the following:
"""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""
All your files are encrypted.
"""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""
ID: RANDOM-ID-123
"""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""
http://hn5fbbc4pyz77xfa.onion.to
http://hn5fbbc4pyz77xfa.onion.cab
http://hn5fbbc4pyz77xfa.onion.city
"""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""
Download and install tor-browser https://torproject.org/projects/torbrowser.html.en
"""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""
TorURL: http://hn5fbbc4pyz77xfa.onion
"""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""
Write down the information to notebook (exercise book) and reboot the computer.
"""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""""When file encryption is complete, all shadow volume copies are deleted which prevents restoring from backups.

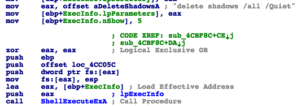
It also displays this ransom screen:


To further warn the user, two files are created in
C:\Users\<username>\AppData\Roaming\MICROS~1\Windows\STARTM~1\Programs\Startup\ with the names <RANSOM ID>.html and <RANSOM ID>.bmp. This causes a slightly different version of the ransom note to appear when the machine is rebooted. It appears as:

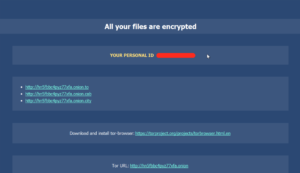
Navigating to the directed payment page gives us this login prompt which boasts and impressive number of locales:

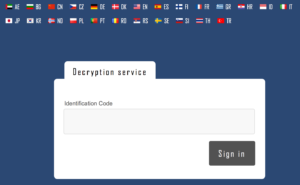
After logging in with the assigned ransom ID, this page is displayed.

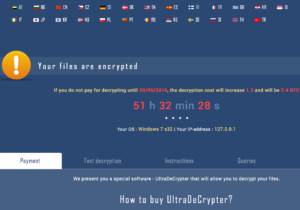
This page contains all of the necessary information and instructions for someone unfamiliar with Bitcoin to be able to purchase them and pay the ransom.


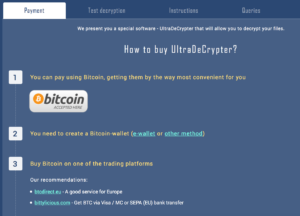
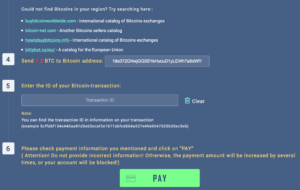
The page also sports a limited test decryption service:

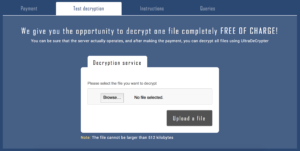
This is a good idea from a psychological standpoint since the malware authors know that people are more likely to pay for something if they know that it will work. This tool allows their victims to confirm decryption is possible, but doesn’t allow them to decrypt any sizable file since there’s a limit of 512 KB.
C&C Server Analysis
The two C&C servers are:
- 85.25.194.116
- 188.0.236.7
Reverse DNS shows that these hostnames at one point pointed at 85.25.194.116:
| Date Seen | Host |
|---|---|
| 2016-06-02 | carspot.co.in |
| 2016-05-27 | astra1767.startdedicated.net |
| 2016-01-25 | www.capitalsend.info |
| 2016-01-24 | bikespot.in |
| 2016-01-23 | ns1.capitalsend.info |
| 2016-01-23 | ns1.investmentreply.info |
| 2015-12-20 | capitalsend.info |
| 2015-11-24 | investmentreply.info |
| 2015-10-29 | www.investmentreply.info |
| 2015-07-09 | pure-send.com |
The three main top level domains which seem to be associated are:
- capitalsend.info
- investmentreply.info
- pure-send.com
The others do not appear related, at least on a first pass.
The following domains were registered by “[email protected]” which is the same email address as the one for capitalsend.info.
- anlegersmart.com
- communicationsdigest.com
- fininvest.info
- finreply.info
- finstock.info
- sharefinance.info
- sharefinancial.info
- sharehold.info
- smartanleger.net
- spamerlist.com
- yourspamshield.com
Interestingly these domains also share a similar theme as those associated with the C&C IP address: investment, finance, and spam.
A file named unsubscribe.php is known to have been downloaded from the 85.25.194.116 IP address. Given the name and the comments on VirusTotal, it seems likely it’s associated with a spam campaign. This suggests that one distribution method of this new CryptXXX version may be through spam.
Ransom Payment Analysis
The ransom Bitcoin address is 18e372GNwjGG5SYeHucuD1yLEWh7a6dWf1.
This address has received over 70Ƀ (Bitcoin) from 6/4/2016 to 6/21/2016 over 61 transactions and all received transactions are either for 1.2Ƀ, 2.4Ƀ. This would indicate that this address is used purely for ransom payments and has affected 61 individuals or organizations in those 17 days.
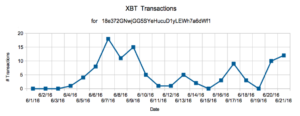

The total amount in USD paid can be calculated by averaging the Bitcoin price over the the past two weeks to be around $500 USD (most transactions happened before rally of Bitcoin to >$700). The total ransom paid comes out to be about $35,000 (500 * 70). At current Bitcoin prices, the ransom paid thus far is worth ~$49,700 at $710 USD per 1 XBT.
While the consistent transaction amounts would suggest that all transactions to this address are for CryptXXX malware, it’s impossible to be certain. Also, multiple addresses may be used for this shortcut malware family. Since this address didn’t have any activity until 6/4/2016, it’s likely that one new address is being used per version or campaign.
Funds at that address are regularly swept to a new, unique address which suggests they may be using a Bitcoin tumbler to mask where the coins are flowing.
Want to know what to do about Ransomware? Read this short paper on steps you can take today. Or watch our webinar on the fundamentals of Ransomware with Jeremiah Grossman, Chief of Security Strategy.


