Picture this: your endpoint protection system has identified a virus, either by detecting its signature or identifying its behavior. It has mitigated the virus and stopped the bleeding, either by halting the responsible executable, dropping the infected endpoint off the network, or even shutting it down entirely. This is all fantastic—the infection has been successfully confined to a single asset, and as a piece de resistance, your endpoint security software has already removed the remnants of the attack and rolled that asset back to a pristine state.
The process outlined above, in which an endpoint security program catches and confines a breach to a single asset, is literally the best-case scenario. Remediation—the process of repairing and recovering data from compromised IT assets—is consistently reported as one of the most high-cost elements of a data breach. Only by using the correct next generation endpoint protection platform can administrators guarantee that remediation will be fast, automatic, and inexpensive.
Even For Smaller Organizations, Remediation Can Be Expensive
According to the 2015 Ponemon Institute report on data breaches, the average cost of a data breach for organizations within the United States was $6.53 million. The weight of that average is probably pulled up a bit due serious mega-breaches that occurred during the year prior—2014 gave us both the JP Morgan breach, and the Sony Pictures hack. With these entities, the cost of remediation included damage to the brand’s reputation, settling lawsuits, setting up a phone bank to contact breach victims, and more.
The good news for SMBs and smaller enterprises is that media attention—widely considered to increase the chance of lawsuits and reputational damage—isn’t likely to be a factor if you’re not a globally or nationally known brand. Lost or damaged data, and damaged or inoperable equipment, are only two factors that generate remediation costs for smaller organizations. You also have to factor in the disruption to peoples’ ability to work—and also any fines that are generated because of failures in compliance.
Here’s the bad news for SMBs—even though the costs of remediation might be smaller, they’ll take up a greater portion of your operating revenue. Large brands can quickly shake off the costs of breaches. For example, the Home Depot breach in 2014 cost the company $232 million. Their revenue from that year, however, was about $79 billion. Even the most expensive breaches disappear quickly into a kind of war chest. Smaller organizations, however, might get wiped out.
How Endpoint Security Can Prevent Expensive Remediation
Return to the first paragraph of this article. The goal of next generation endpoint protection is to elide the part of remediation that includes fines and lawsuits and PR wrangling. With the right next generation endpoint protection, all administrators have to focus on is repairing and restoring damaged data and equipment.
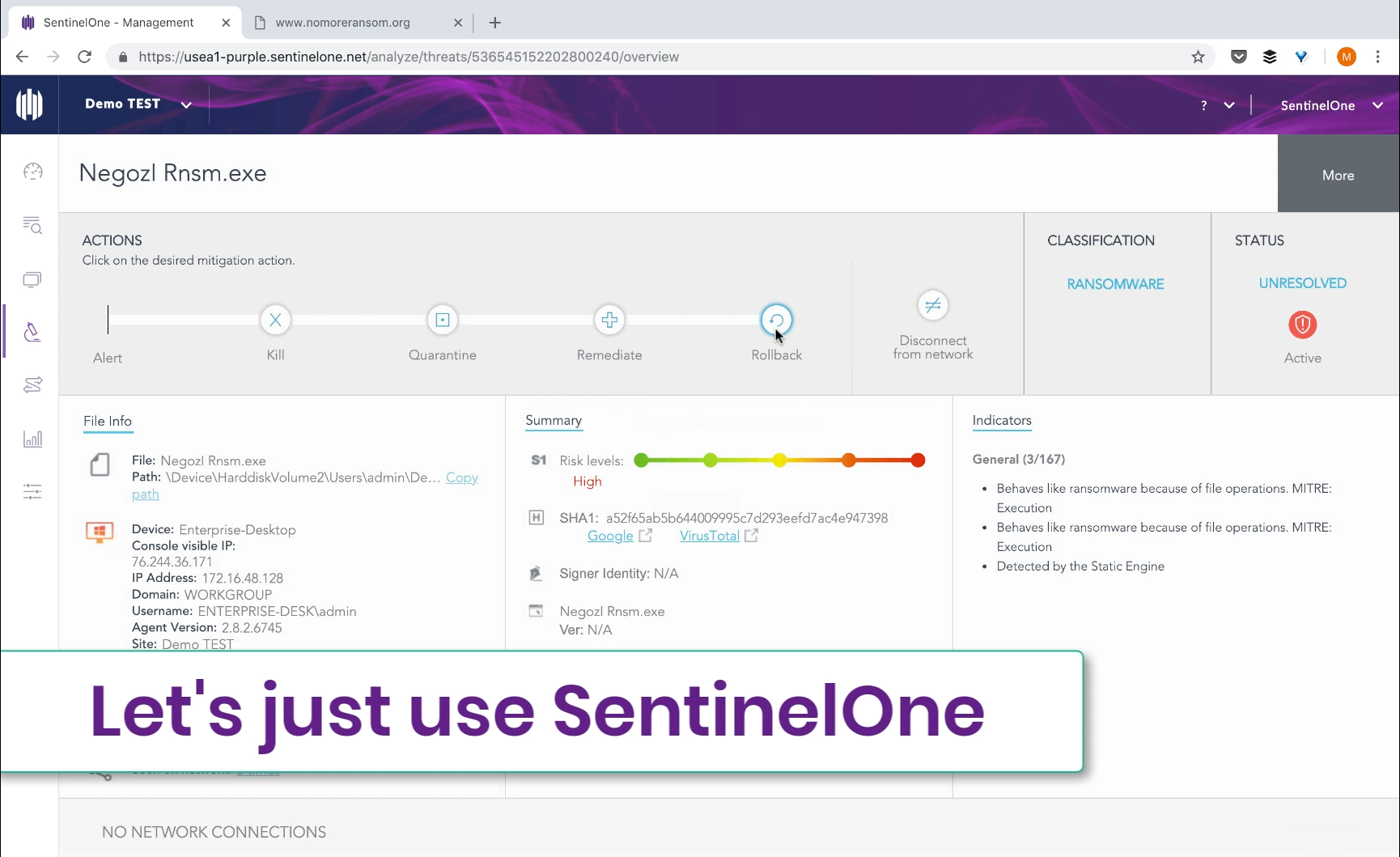
SentinelOne users actually have the opportunity to automatically remove files or rollback changes – even small ones – made by malicious software. Many malware samples will be blocked automatically, due to our integration with cloud intelligence services. For those that aren’t, the SentinelOne visor will still detect malicious behavior—such as unauthorized file encryption—and take pre-defined actions – alert only, block, isolate, and more. If in alert-only mode, administrators will be able to see the timeline of events, and make the determination of whether the file is actually malicious.
Once the administrator determines that a file has performed malicious actions, they can roll those actions back with a single click. For more details on what this process looks like, check out the tech demo.
With SentinelOne, remediation sheds its seven-figure price tag, and becomes a painless, often automatic process. For more on how SentinelOne can protect your systems and forestall data breaches, read our technical brief, or contact us today.