Your organization is adopting cloud-native architectures, and the stakes have never been higher: by 2029, 60% of enterprises without a unified Cloud-Native Application Protection Platform (CNAPP) will struggle with cloud visibility. This highlights a critical truth: without robust security measures, your organization is at risk of sophisticated cyber threats.
In 2024, a cloud-native security platform is a lifeline: implementing a CNAPP can reduce security incidents by up to 50% through enhanced automation and integrated visibility. Benefits include:
- Real-time insights for proactive threat detection
- Automated compliance to meet regulations effortlessly
- Scalable security to grow with your organization
To confidently set about on your cloud-native security journey and shield your data from breaches and vulnerabilities, this article examines the top 10 cloud-native security platforms that can strengthen your defenses and drive your organization to success.
 What is Cloud-Native Security?
What is Cloud-Native Security?
Cloud-native security focuses on embedding security at every phase of the cloud lifecycle, ensuring that protection is integrated from development through deployment. Cloud-native security is designed to keep up, providing solid protection across all your cloud platforms, no matter how they shift and grow.
Without a Cloud-Native Security Platform, organizations face limited visibility into their cloud environments, inconsistent security policies, and higher risk of breaches. Traditional security measures often miss threats, making detection and response difficult. Managing security across different cloud providers is challenging due to their unique tools and policies, leading to security gaps and vulnerabilities.
But with a CNSP, you get:
- Better visibility and control means you can see everything that’s happening in your cloud environment.
- Automated threat responses, that is, you quickly address threats without manual intervention.
- Uniform security to implement the same security measures across all your cloud platforms.
- Enhanced compliance simplifies the process of meeting regulatory standards.
By doing this, you not only bolster your security posture but also gain the assurance to expand and innovate in the cloud, free from the fear of potential threats.
Suggested read: What is Cloud Native Security?
Need for Cloud Native Security Platforms
Right now, over a third of companies (44%) have faced a data breach in 2023 alone, a rate that keeps going up. Despite the constant rise in cyberattacks, a surprising 17% of businesses still don’t encrypt up to half of their sensitive data stored in the cloud.
This is troubling as data vulnerabilities not only persist but are worsened by the rapid switch to multi-cloud setups and the lack of consistent encryption.
On the business side, these issues can be devastating beyond just data loss. The average data breach worldwide in 2024 now costs companies $4.88 million, and in the U.S., it hits as high as $9.36 million.
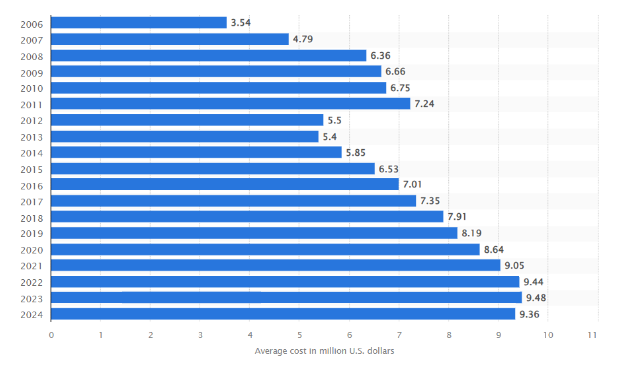
But there is more at stake than just the numbers. Can a business truly scale and innovate if its cloud environment is a potential weak spot? And with cloud environments getting more complex, can organizations even defend their investments if crucial resources are misconfigured or left vulnerable? And what trade-offs are being made that could backfire as compliance demands grow?
These questions demand answers, and CNSPs provide these answers and actionable solutions as well.
These are key reasons why Cloud-Native Security Platforms (CNSPs) are vital in modern organizations:
- Unified compliance tracking: CNSPs keep reporting standardized across cloud providers, reducing compliance issues as regulations increase.
- Flexible security scaling: As cloud assets grow, CNSPs adapt so new resources don’t open up new risks.
- Data sovereignty support: CNSPs help manage local data privacy needs, which is crucial for companies operating across borders.
- Better post-incident insights: They make it easier to analyze incidents, enabling quicker and clearer fixes.
- Efficiency through automation: With automated tools, CNSPs cut down on human error and free up IT teams to focus on high-priority work.
Cloud Native Security Platforms Landscape in 2026
Cloud-native security platforms provide various features that take care of all aspects of your cyber security. From IaC scanning, detecting secrets, attack surface management, and more, here is a list of the best ones. We’ve curated it according to the latest reviews and ratings. Let’s explore below:
#1 SentinelOne Singularity Cloud
SentinelOne’s Singularity Cloud is a top Cloud Native Application Protection Platform (CNAPP) that ensures the security and protection of cloud environments throughout the entire build time to runtime process. It provides a single solution with complete control, immediate response, automation, and advanced threat intelligence.
Wondering if it can handle different types of workloads? Be it virtual machines, Docker containers, Kubernetes servers, serverless functions, or databases, SentinelOne’s Singularity Cloud makes it all possible with its capabilities spread across public, private, on-premises, and hybrid environments.
SentinelOne Platform at a Glance
SentinelOne’s Singularity Cloud Native Security gives teams clear and instant insights into their cloud environments without extra hassle. It streamlines security by providing over 2000 incorporated systems for checking misconfigurations and has systems for different compliance levels, assisting in the identification and rectification of issues before they escalate into problems.
The platform’s Offensive Security Engine (OSE) cuts down on irrelevant alerts, so your team only deals with real threats and wastes no time on false positives. With easy access to everything from secret leakage prevention to proactive threat detection, Singularity helps teams stay ahead of attackers and better manage security across popular cloud platforms like AWS, Azure, and Google Cloud.
A single dashboard gives a full view of compliance, threat management, and cloud health, keeping your cloud environment safe and sound in a straightforward, efficient way.
Features:
- AI-Powered Threat Detection uses autonomous AI engines to identify and react to threats in real-time quickly.
- Total Security ensures that every aspect of cloud infrastructure is covered with no limits on protection.
- Cloud Security Posture Management (CSPM) continually evaluates and enhances the security stance across a variety of cloud platforms.
- Cloud Detection & Response (CDR) provides proactive threat detection and remediation capabilities.
- Secret Scanning identifies and prevents leakage of sensitive information across cloud assets.
- Verified Exploit Paths™ prioritizes risks based on assessing possible ways to exploit vulnerabilities in the cloud infrastructure.
Core Problems that SentinelOne Eliminates
- Discovery of Unknown Deployments automatically detects cloud assets that are concealed or unsecured.
- Evaluation of Compliance Simplification simplifies the assessment of adherence to various frameworks.
- Detecting Misconfigurations rapidly identifies and resolves misconfigurations in real-time.
- Threat Response and Remediation quickly respond to incidents with actionable insights and forensic telemetry.
- Stop the Breach of Private Information protects sensitive data from unauthorized access.
What users think about SentinelOne Singularity Cloud
Here are some testimonials from satisfied customers who have experienced the benefits of SentinelOne Singularity Cloud:
“The Singularity Platform maximizes our ability to proactively detect threats and minimize response times, allowing us to focus on critical issues while relying on SentinelOne for effective identity protection and continuous innovation.” – Mihirr Thaker, CISO, Allcargo Logistics.
Gather insights from customer reviews on PeerSpot and Gartner for Singularity Cloud Security.
See SentinelOne in Action
Discover how AI-powered cloud security can protect your organization in a one-on-one demo with a SentinelOne product expert.
Get a Demo#2 Prisma Cloud by Palo Alto Networks
Prisma Cloud from Palo Alto Networks excels at protecting cloud environments. Security is incorporated into every phase of the lifecycle, from creating to running applications. Additionally, extensive monitoring and compliance functionalities simplify the task of overseeing security across multiple cloud services.
Features:
- Comprehensive Visibility tracks every cloud resource and service.
- Monitoring compliance through automated assessments with industry norms.
- Runtime protection secures applications while they are in operation.
- Vulnerability Management helps to identify vulnerabilities in code and configurations.
Assess Prisma Cloud’s credibility by looking at the number of reviews and ratings on PeerSpot and Gartner Peer Insights.
#3 Wiz
Wiz’s agentless design is gaining attention as a comprehensive cloud security solution that makes securing cloud environments easier and provides thorough visibility. Wondering how it can help without the hassle of agents? Wiz offers full visibility over your cloud resources, making compliance simpler.
Features:
- Agentless Scanning offers full visibility without agents.
- Detection of threats with ongoing surveillance for potentially suspicious behavior.
- Vulnerability Management discovers vulnerabilities in workloads.
- Compliance Automation simplifies following regulations.
Explore the feedback and ratings on G2 and PeerSpot to get further insights into Wiz’s capabilities.
#4 Lacework
Lacework is a cloud security platform that uses machine learning to detect threats across multiple cloud environments quickly. It makes security management easier with a user-friendly interface and powerful automation features, giving your team full visibility of risks.
Features:
- AI is utilized in Automated Threat Detection to identify abnormalities.
- Reporting compliance simplifies adherence to regulations.
- Cloud workload protection secures workloads across diverse environments.
- Integrating with CI/CD Tools improves DevSecOps workflows.
Check out G2 and PeerSpot reviews and ratings to see what users have to say about Lacework.
#5 Trend Micro Cloud One
Trend Micro Cloud One was created to protect cloud environments, offering a wide range of services made for AWS and more. It offers strong security for different levels of cloud infrastructure and applications. Customized security is provided for servers, containers, serverless functions, and other elements to ensure complete protection for your cloud setup.
Features:
- Workload Security safeguards servers, containers, and serverless functions.
- Security of containers detects vulnerabilities in images prior to deployment.
- File storage security monitors data stored in the cloud.
- Network Security Controls defend against network threats.
Find out how effective TrendMicro Trend Vision One is as a cloud-native security platform by browsing its Gartner Peer Insights and TrustRadius reviews and ratings.
#6 Check Point CloudGuard
Check Point CloudGuard provides targeted security for cloud environments, seamlessly integrating with existing procedures to enhance protection without affecting efficiency. It collaborates with DevOps instruments to guarantee security throughout every phase of development, simplifying compliance for rapid deployments.
Features:
- Advanced Threat Prevention shields from known and unknown risks.
- Cloud Compliance guarantees conformity with industry regulations.
- Security Posture Management constantly evaluates configurations.
- Collaboration with DevOps Tools facilitates agile development methods.
Evaluate these PeerSpot and G2 reviews to get an informed opinion about Check Point CloudGuard’s cloud-native security features.
#7 Orca Security
Orca Security’s Cloud-Native Application Protection Platform (CNAPP) makes securing your cloud environments easy and effective. It uses a unique SideScanning technology that doesn’t need agents, giving you complete visibility and risk management for all your cloud assets. This simplifies identifying and prioritizing vulnerabilities, ensuring you don’t compromise on security while streamlining the process.
Features:
- Agentless Coverage shares insight into cloud misconfigurations and vulnerabilities without installing agents.
- Compliance Dashboard provides 60+ prebuilt compliance frameworks.
- Vulnerability Management identifies risks with actionable intelligence.
- SideScanning allows fast access to findings without performance issues.
Learn how well Orca Security meets your cloud-native security needs by visiting G2 and PeerSpot ratings and reviews.
#8 Sysdig
Sysdig is a top cloud-native security platform designed to secure containers and Kubernetes environments. It offers features that boost visibility and compliance across your cloud infrastructure. With deep integration into Kubernetes, Sysdig provides real-time monitoring and threat detection for containerized applications.
Features:
- Runtime Security monitors applications in real-time for threats.
- Compliance Monitoring ensures compliance with industry standards.
- Vulnerability Scanning identifies vulnerabilities in images before deployment.
- Service-Level Monitoring provides insights into service performance and security.
Look at Sysdig’s ratings and reviews on PeerSpot and G2 for more information.
#9 Microsoft Defender for Cloud
Microsoft Defender for Cloud is a strong security solution for Azure and multi-cloud setups. It offers threat protection and compliance management across different platforms. Its integration with Azure services makes monitoring and threat detection easy, perfect for organizations using Microsoft products.
Features:
- Threat Protection detects real-time threats in cloud resources.
- Compliance Management provides integrated compliance evaluations.
- Security Posture Management persistently observes settings and weaknesses.
- Utilizing Azure Services integration enhances security by utilizing Microsoft’s existing tools.
Check out G2 and Peerspot reviews to see what users have to say about Microsoft Defender for Cloud.
#10 Aqua Security
Aqua Security keeps your containerized apps safe from start to finish. It’s designed for modern cloud setups and ensures security at every stage, from development to deployment.
Features:
- Container Security scans images for vulnerabilities before deployment.
- Runtime Protection monitors running containers for threats.
- Compliance Automation ensures adherence to industry standards.
- Serverless Security protects serverless functions from vulnerabilities.
See how Aqua Security performs in cloud-native security by reading its PeerSpot and Gartner Peer Insights ratings and reviews.
How to Choose the Right Cloud-Native Security Platform
Deciding on the right cloud-native security platform can be tricky with the glut of options out there. You must clearly define your requirements and then evaluate which tools meet them. Here’s how:
- Know your security needs. What do you need? Threat detection, compliance, container security? List them out.
- Check integration. Will the tool work well with what you already have? Seamless integration saves time and hassle.
- Consider your budget. Find tools that give you the best features without breaking the bank.
- Think about scalability. Pick a tool that can grow with your business. It should handle more work as you expand.
- Look for good support. Make sure the tool comes with strong support and clear documentation to help you out when needed.
If you pick the wrong cloud-native security platform, you might face issues like:
- security gaps can leave your apps vulnerable,
- higher costs can strain your budget, and
- complicated workflows can disrupt your operations.
To avoid these problems, ask yourself key questions about your needs, integration, budget, scalability, and support. By focusing on these areas, you can find a tool that fits your current needs and can adapt to future demands. The right cloud-native security platform will make development easier, boost performance, and keep your cloud-native applications secure, ensuring they run smoothly and cost-effectively.
 CNAPP Buyer’s Guide
CNAPP Buyer’s Guide
Learn everything you need to know about finding the right Cloud-Native Application Protection Platform for your organization.
Read GuideConclusion
As technology evolves, so does user interaction. This evolution brings more sophisticated cyber threats and frequently updated compliance requirements, necessitating ongoing adjustments in security practices. Why is this critical even if your organization already has a system in place? Because it calls for a cloud-native security platform that offers real-time protection, comprehensive coverage, and enhanced visibility.
Without such a platform, your organization is prone to issues like data breaches, misconfigurations, and insecure APIs. These aren’t just minor issues; they can cause severe financial and reputational damage if not addressed. Are you convinced to add a tool that helps you? The market is filled with tools, so how do you choose the right one? Your organization needs rapid threat response, compliance management, and automated remediation.
This is where SentinelOne’s Singularity platform excels. With advanced AI, it secures your cloud assets from build time to runtime. It offers unique features like Verified Exploit Paths, agentless onboarding, and comprehensive threat intelligence. SentinelOne stands out for its real-time threat detection and automated responses. Want to ensure your infrastructure remains secure and compliant?
Connect with us today and elevate your organization’s security with SentinelOne’s Singularity Cloud Security, where cutting-edge technology meets strong protection!
FAQs
Cloud-native security is important because it is built to handle the fast-paced and dynamic nature of the cloud. Instead of focusing solely on the network, it gives importance to securing the application itself. This includes supervising app permissions, safeguarding distinct app environments, and consistently monitoring for threats. The goal is to build security into the app from the beginning, not add it later.
Cloud-native security is a security approach that embeds protection directly into each layer of the cloud setup, ensuring threats are managed as services scale and move.
This approach works in real-time, scaling automatically to cover everything from applications to infrastructure across multiple cloud environments, and it shifts to meet evolving threats and compliance needs without slowing anything down. It’s security engineered to be as dynamic as the cloud systems it protects.
The 4 C’s of CNS are:
- Code: Write secure code to prevent vulnerabilities from the start.
- Container: Secure the containers to stop issues from spreading.
- Cluster: Protect the orchestration layer (like Kubernetes) to secure the whole cluster.
- Cloud: Secure the cloud infrastructure to guard against threats and comply with regulations.
Choosing the best tool depends on what you need, but here are some top options:
- SentinelOne: Uses AI to detect threats in real-time, automatically respond, and protect containers and Kubernetes environments through comprehensive security measures.
- Aqua Security: Great for keeping containers safe from vulnerabilities.
- Palo Alto Networks Prisma Cloud: Offers a wide range of features to secure your cloud environment.
- Sysdig: Gives you deep insights into your container environments, helping you monitor and secure them.
- Twistlock: Focuses on protecting containers and cloud-native applications.
Tools created for building, deploying, and managing applications in the cloud are part of cloud-native tooling. These tools maximize the scalability and flexibility of the cloud.
Some cloud-native tools that can streamline development, boost performance, and enhance security:
- Kubernetes is responsible for handling containers.
- Docker generates containers’ instances.
- Prometheus helps to monitor and notify.
- Istio controls the communication between services
SentinelOne’s Singularity Cloud Native Security is designed to make cloud protection simple and effective. It gives you instant visibility across your cloud environment without the hassle of extra agents. With its Offensive Security Engine™, it goes a step further by simulating safe attacks to find real vulnerabilities, so you only get alerts that actually matter.
Plus, it has built-in secret scanning to keep sensitive info from slipping through the cracks and a dashboard that simplifies compliance with more than 2,000 checks across all major cloud providers.

