Amazon S3 buckets are used to store any data type for cloud-based applications in IT ecosystems. Amazon S3 is a popular choice in the AWS cloud when it comes to data storage. However, there are many security risks associated with data visibility and data security. Despite the added flexibility offered, an organization is responsible for the data it stores in these buckets.
It is important to learn how to secure S3 buckets and avoid sensitive data exposure. There are different security layers and practices available that can fortify your cloud security defenses. The Amazon S3 bucket connector shares XDR data with your AWS environment and requires setting custom AWS IAM roles. Threat detection for Amazon S3 can offer machine-speed protection to detect and eliminate ransomware and malware from your S3 buckets. Protecting NetApp storage is critical for ensuring business operational stability and integrity.

To help organizations achieve continuous visibility and an enhanced security posture, it is crucial to utilize Managed XDR solutions to ingest S3 data logs and automate S3 bucket data management. You can set predefined rules, reduce storage costs, and improve compliance. This guide will cover everything you need to know about Amazon S3 bucket security, including the best practices for securing S3 buckets. Read on to learn more below.
What is Amazon S3 Bucket Security?
Amazon S3 bucket security is a shared responsibility between the consumer and AWS provider; S3 bucket security defines how users can have access to the S3 resources that they create. Amazon S3 bucket security encompasses configuring permissions for all objects, granting time-limited access privileges, and supporting audit logs for making requests against S3 resources to gain complete visibility.
Users can gain access to AWS guidance reports; they can take advantage of AWS monitoring services to examine existing configurations and resource utilization of AWS services. Other aspects covered by Amazon S3 bucket security are:
- Versioning – S3 allows users to create multiple versions of different objects and save them in S3 buckets. This can especially help for disaster recovery processes and backup, whenever a security incident occurs.
- Auditing – It is important to perform regular auditing of your S3 bucket configurations, access logs, and permissions, to identify potential security issues and vulnerabilities.
- Logging – Amazon S3 provides great logging and tracking capabilities to monitor bucket activity. It includes managing requests, error handling, and reviewing access patterns.
Why is S3 Bucket Security Important?
Poor Amazon S3 bucket security can cause organizations to experience operational failures and lose customer trust. S3 buckets are used to store personally identifiable information (PII), credit card data, financial data, intellectual property rights, and other types of confidential information. Lack of S3 bucket protection can lead to lawsuits, identity theft, and staggering revenue losses due to data breaches.
Many industries like healthcare, e-commerce, finance, and government domains have strict regulations and compliance requirements for data storage and security. Amazon S3 bucket security ensures compliance with these regulations. It also helps to ensure business continuity, minimize downtimes, and protect against unauthorized data modification. Good S3 bucket security can help reduce the total cost of business ownership, prevent unnecessary data storage and transfer expenses, and reduce the need for manual data recovery. It is a part of any holistic cyber security program and S3 buckets must be protected from external threats.
Clients these days want the best S3 bucket security practices to be incorporated before availing any services. It is essential for enhancing the brand’s reputation and protecting data integrity.
Best Practices for Securing S3 Bucket
1. Implement Least Privilege Access on Bucket Policy
Whitelist IP addresses and ARN for accounts that require access to S3 buckets. Enable block public access settings and remove anonymous access to S3 buckets. You can write custom IAM policies for users who need access to specific buckets. These policies can be configured to manage Amazon S3 permissions for multiple users. You can use IAM roles anywhere or use them as temporary credentials and a session token instead.
Ensure that your identity-based policies do not use any wildcard actions. To remove manual intervention, define S3 lifecycle policies to automatically remove objects on schedule, where needed. On GuardDuty, you can enable S3 protection to detect malicious activities and leverage anomaly detection, and threat intelligence. AWS recently launched Macie which is another great tool for scanning sensitive data outside of designated areas.
To implement least privilege access, AWS offers several tools such as permissions boundaries, bucket ACLs (Access Control Lists), service control policies, and more. Maintain a thorough record of all your identities across S3 resources that have authorized access.
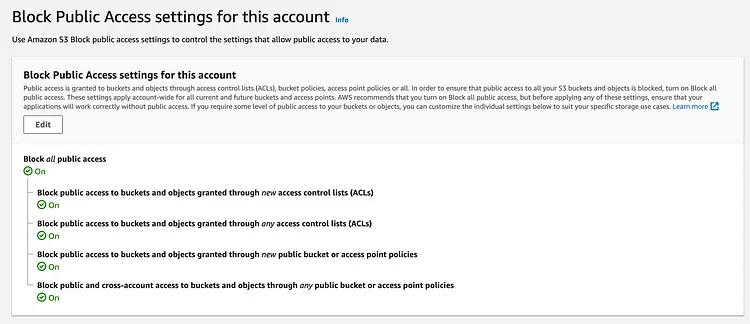
2. Encrypt Data At Rest And Transit
Monitor your AWS ecosystem and find out which buckets have encryption disabled on them. It is important to encrypt on the bucket level and not object level to protect S3 bucket data from unauthorized access and data breaches.
You can apply server-side encryption with Amazon S3 and protect data from accidental deletion by using S3 versioning and S3 object lock. If you want an additional layer of security, you can add a Multi-Factor Authentication (MFA) delete. Amazon S3 comes with CloudTrial and S3 server access logging capabilities. You can get a comprehensive view of your security state by using CloudWatch logs. Be sure to check your environment’s encryption standards against industry benchmarks.
You can also use the AES 256-bit encryption to encrypt customer data and remove keys from memory after completion of the encryption process. Customer-provided encryption keys work great and are provided by the user. For customer-managed keys, you can create, rotate, disable, audit, and get complete access to encryption controls. You can create customer-managed keys (CMKs) using the AWS KMS console before using it at the S3 level. By default, Amazon S3 already creates AWS Managed CMK in the AWS account for the first time. It uses this CMK for SSE-KMS and Amazon Sigv4 is an authentication mechanism powered by Amazon S3 for signing API requests. To check the encryption status of your objects, you can use the S3 inventory for more information. The four primary encryption management options available for your S3 buckets are SSE-KMS, DSSE-KMS, client-side encryption, and SSE-C.
3. Follow Security Standards That Comply With The Best Practices
Organizations worldwide follow multiple security standards that secure S3 buckets. By complying with some of them, you can keep data in your S3 buckets safe and protect systems. You can safeguard cardholder data, leverage firewalls, and configure password settings as well. Ensure you apply these standards to all AWS public cloud instances.
The most popular standards followed by global organizations to ensure Amazon S3 bucket security are:
- National Institute of Standards and Technology (NIST)
- Monetary Authority of Singapore (MAS)
- General Data Protection Regulation (GDPR)
- Payment Card Industry Data Security Standard (PCI DSS)
- Australian Prudential Regulation Authority (APRA)
4. Use Multi-Region Application
You can use DynamoDB global tables for asynchronous data replication across primary and secondary regions. Use AWS’s multi-region application architecture for managing fault-tolerant applications. You can enhance the disaster recovery capabilities of your S3 buckets by taking advantage of AWS’s S3 cross-region replication feature.
5. Try S3 Pre-Signed URLs
Amazon S3 objects are private by default. Only the object owners have access to them. However, there may be times when an object owner wants to share objects with others. Using pre-signed URLs allows them to set their own security permissions and grant time-limited access to download objects.
You can link objects with a custom lifetime in an S3 bucket by using pre-signed URLs. For example, you can generate a pre-signed URL for a specific bucket and make it valid for 1 week by using the following command:
aws s3 pre sign s3://DOC-EXAMPLE-BUCKET/test2.txt
--expires-in 604800
6. Use S3 Bucket Security Monitoring Tools and Conduct Regular Audits
You can tag S3 resources for performing security audits by using the Amazon Tag Editor. You can create resource groups for S3 resources to manage and audit them effectively.
AWS services like CloudWatch will let you monitor key metrics like 4xxErrors, DeleteRequests, GetRequests, and PutRequests. Monitoring these metrics regularly can ensure the security, performance, and availability of your S3 resources.
You can also use AI-powered tools like SentinelOne to automate your S3 bucket security monitoring, audit, and generate reports.
How SentinelOne Can Help?
Storing and using unscanned files in S3 buckets can introduce a variety of security risks that organizations want to avoid at all costs. Enterprises use S3 buckets due to them being scalable and secure object storage solutions. The content and security of files uploaded to these buckets can be unknown which is why customers need to scan them and mitigate any application vulnerabilities that may arise.
SentinelOne helps organizations satisfy data sovereignty and compliance requirements rapidly. It detects malware and zero-days in milliseconds and protects cloud environments by preventing such threats from spreading. Users can streamline and automate file threat analysis, easily integrate into existing applications and workflows, and enjoy flexible coverage policies.
The SentinelOne management console allows users to manage workloads, endpoints, and S3 resources. It automates bucket discovery and comes with strong guardrails in place to prevent accidental misconfigurations.
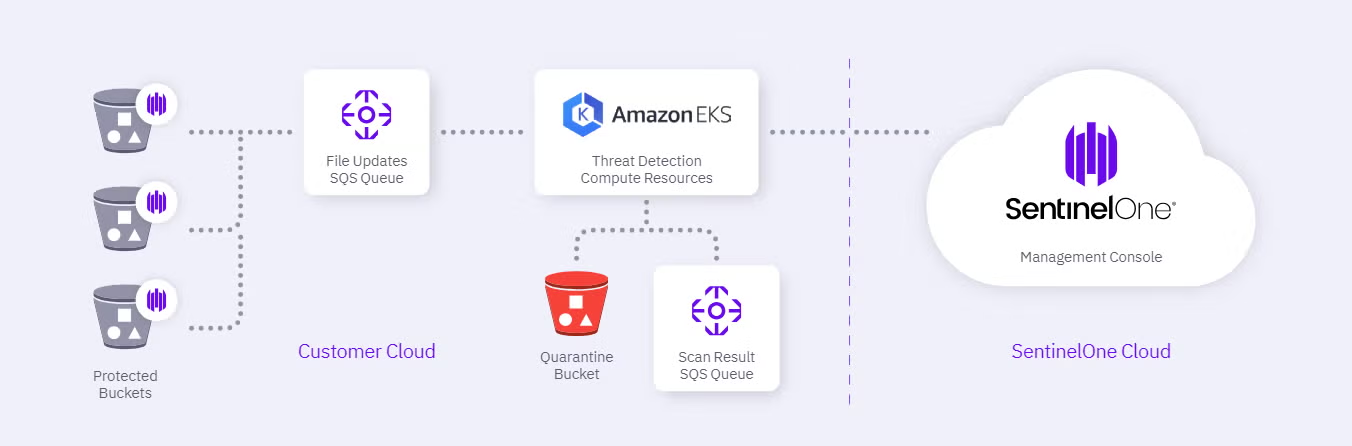
Here is how SentinelOne enhances Amazon S3 bucket security for organizations:
- Advanced threat detection for Amazon S3 buckets – SentinelOne scans every object added to the bucket for malware and can scan existing files easily on demand. Autoscaling, file quarantine, and custom remediation actions allow organizations to remove infected files and prevent the spread of malware
- Configurable Cloud Policies – SentinelOne cloud policies are configurable and can be customized to suit your business requirements; it adds dynamic flexibility for provisioning assets and all scanning is done within the environment. No sensitive data ever leaves the cloud environment and this protection easily deploys and integrates with existing application architectures and workflows
- Inventory Management – SentinelOne protects organizations with powerful cloud threat-hunting capabilities. It delivers telemetry for workloads, applies policy-based protection, and streamlines cloud inventory storage management. It is trusted and recognized by Gartner, MITRE Engenuity, Tevora, and many more. Singularity XDR platform protects and empowers leading global enterprises with real-time visibility into attack surfaces, cross-platform correlation, and AI-powered response actions.
AI-Powered Cybersecurity
Elevate your security posture with real-time detection, machine-speed response, and total visibility of your entire digital environment.
Get a DemoConclusion
Amazon S3 bucket security features are used by consumers worldwide to protect objects stored in S3 buckets. There are monitoring practices and auditing practices and preventive security best practices, both of which we’ve covered in this guide. Identifying and auditing all your assets is a crucial step to take when safeguarding your S3 buckets. When you disable access control lists, data protection is dependent on your custom policy writing and management. You can also take advantage of Virtual Cloud Endpoint (VCE) policies and take full bucket control ownership by resetting bucket ACL settings to default.
Ensure that all your buckets use the correct policies and are not set to publicly accessible. Consider implementing ongoing security monitoring and auditing services like SentinelOne to inspect S3 implementations and manage AWS Config Rules. The good news is that platforms like SentinelOne are easy to use and set up. You can schedule a free live demo with us and test out our various features. We can help you stay protected in today’s competitive landscape.
FAQs
Amazon S3 security encompasses all the security measures taken to protect objects from unauthorized access, manipulation, and data breaches. AWS security has various built-in security features that users can benefit from. S3 security involves writing custom security policies, configuring buckets, and ensuring that the right monitoring, encryption, and logging mechanisms are in place. The goal of S3 security is to make sure that the data saved in buckets is kept secure, private, and accessible to authorized users alone.
You can secure your S3 buckets in a variety of ways. The first method is to use the AWS tools and resources provided by the AWS ecosystem. You can change the default configurations and alter bucket policies to protect sensitive data. The second and best way to secure S3 buckets is to use an AI-driven security automation platform like SentinelOne. SentinelOne delivers cutting-edge threat intelligence, monitoring and analytics, and a whole suite of excellent cyber security features. You can remediate critical vulnerabilities across your entire cloud estate by using its 1-click remediation.


