Security professionals visibility gaps arising out of the usage of multiple tools, the second most pressing matter in cybersecurity. Both log management and SIEM tools can help – albeit their different capabilities.
Before we get into the nitty gritty of SIEM vs log management, here’s a metaphor that can simplify the whole comparison. Think of log management as the father and SIEM as the child, who has picked up new tricks. Meaning, that log management forms the foundational aspect of SIEM solutions. The latter, however, does more than just storage and management of log data, providing comprehensive visibility and analysis of security events, and enabling organizations to detect anomalies and respond to threats in real-time.
However, grasping the differences between SIEM and log management will help you pick the right solution, avoid overspending, and better plan resources to use either of these tools. For example, while log management requires less computational and human effort to use, configuring and managing data from SIEM solutions would require skilled professionals.
This article will shed light on SIEM vs log management concepts and tools necessary for effective threat detection and security monitoring. Let’s begin.
 What Is A SIEM?
What Is A SIEM?
Security information and event management (SIEM) solutions combine security information management (SIM) and security event management (SEM) to help companies identify, analyze, and respond to security threats. This is done via capabilities like ingestion automation, AI/ML-driven event correlations, and alerts.
Both SIM and SEM enable real-time analysis of security alerts generated by applications and network hardware.
SIEM as a tool is useful for the following:
- Comprehensive network overview
- Integrated functions
- Real-time threat detection
- Proactive incident response
SIEM solutions use various integration tactics such as deploying agents and connecting with APIs to collect logs and events from endpoints, security tools, intrusion detection and prevention systems, firewalls, web filtering solutions, application servers, IAMs and so on.
After integrating the data from these varied components, the SIEM system standardizes data to deliver crucial insights into potential security vulnerabilities.
For example, consider a situation where firewall logs show several failed login attempts from a certain IP address, the intrusion detection system raises an alert about suspicious activity from the same IP address, and active directory logs reveal that a privileged user’s account was accessed subsequent to many failed attempts.
Separately, these events do not raise concerns. But SIEMs correlate these seemingly unrelated events and alert security teams that it could be a brute force attack.
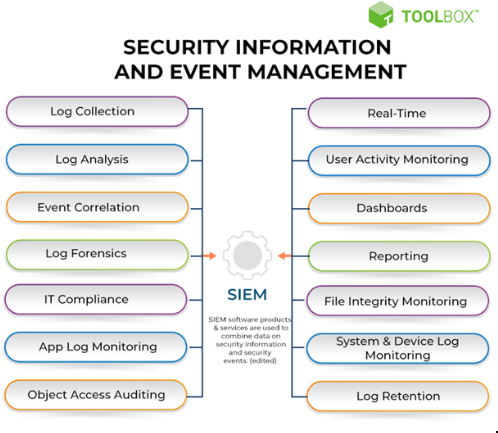
What is SIEM logging?
SIEM logging involves gathering, analyzing, and correlating log data from a company’s IT infrastructure to identify security threats and improve the company’s security posture. Security analysts source log data from several sources, such as systems, firewalls, applications, intrusion detection systems, endpoints, and network devices. This allows them to review large amounts of data and respond to potential threats effectively.
What are the key components of SIEM logging?
Logs in SIEM software have the following key components:
- Timestamps
- Source and destination information
- User information
- Event type
- Action taken
Timestamps
Timestamps pinpoint the exact moment an event happens. They allow security analysts to piece together the sequence of events leading up to a security incident accurately. If the timing is not precise, it is challenging to correlate and analyze events correctly.
In addition, timestamps are important for spotting anomalies. If there are several failed login attempts in a short period of time, it could be a brute-force attack. Security teams can promptly look into suspicious activities by monitoring events with specified timeframes.
Source and Destination Information
Source and destination information in SIEM logs, like IP addresses, hostnames, or device identifiers, determines the origin and target of specific events. This data is important to grasp the context of events and detect compromised systems.
Accurate source and destination details help track the lateral movement of threats across the network. They enable security teams to identify the attack’s entry point and gauge its potential impact on other systems within the infrastructure.
User Information
User information, such as usernames, IDs, or roles, identifies the user involved in an event. This information distinguishes between legitimate and unauthorized activities and identifies compromised user accounts.
By analyzing user-related data, security teams can spot unusual behavior patterns that might indicate potential insider threats or account takeovers. Additionally, monitoring user activity aids compliance efforts by ensuring that user actions adhere to established security policies.
Event Type
Event type describes the kind of activity recorded in the SIEM log, such as login attempts, file access, or policy violations. By categorizing these events, security analysts can filter and prioritize incidents based on their severity and relevance.
Recognizing the event type allows security analysts to quickly assess the nature of an event and decide on the appropriate actions, whether that means escalating a security alert or initiating an investigation.
Action Taken
The “action taken” field documents the response executed for a specific event, such as blocking an IP address or isolating a compromised device. This record provides a trail of actions performed by automated systems or security personnel.
Documenting actions taken is vital for auditing and review processes, enabling organizations to assess the effectiveness of their incident responses. It also ensures accountability and assists in refining security policies and procedures over time.
What are the 10 Primary Features of SIEM?
Legacy SIEM solutions require expert data analysis and a skilled team to filter out noisy alert sources and identify real security threats. Since the process is labor-intensive and log sources are not always complete, security analysts could miss meaningful but innocuous events. It also required weeks or months to reveal and investigate events, and therefore, that much longer to mitigate any breaches.
The 10 features of modern SIEM systems are:
Gather and Manage Data from all Available Sources
Modern threats often span multiple data sources. To effectively analyze and correlate this data, your modern SIEM must have access to every data source. This includes data from cloud services, on-premises logs (like identity, databases, and application logs), and network data (such as intrusion detection, endpoints, flows, packets, etc.).
Your SIEM should also include centralized, remote security data management. Once you’ve configured and activated all log collectors, managing them (start, stop, update, reconfigure) from any location should be straightforward.
2. Well-vetted, Big Data Architecture
Many legacy SIEMs, developed in the early 2000s, utilized proprietary technology that is now outdated. Modern platforms like Hadoop, Mongo, Elasticsearch, BigQuery, and Spark offer capabilities not available back then.
With the vast amount of security data now available, a big data architecture that allows for scalable data management, quick pivoting, and the use of advanced data science algorithms for speedy queries and visualization is essential.
3. Predictable Pricing for Log Ingestion
Setting specific log retention times helps optimize spending by automatically eliminating unnecessary logs. By specifying how long to keep logs by type and source, organizations can free up storage, ensure predictable spending, and avoid accumulating excessive data and its associated costs.
For instance, upgrading your firewall might increase logging tenfold. With consumption-based pricing, your SIEM license fees would increase accordingly. However, a flat-rate pricing model allows you to ingest data from all sources and stay within your budget without having to cherry-pick data sources.
4. Enrichment of User and Asset Context
Select an SIEM solution that provides a high level of enrichment, giving actionable insights from the data you collect. Thanks to advances in data science, many insights can now be automatically correlated by the SIEM system, such as:
- Free threat intelligence integration and correlation
- Dynamic peer grouping
- Linking IP addresses with user credentials, devices, and timelines
- Tracking asset ownership
- Associating user and machine types with activities
- Identifying service accounts
- Correlating personal email addresses with employees
- Linking badging station log activity with user accounts and timelines
5. User and Behavior Entity Analysis (UEBA)
A modern SIEM should automatically establish behavioral baselines through machine learning, statistical analysis, and behavioral modeling called user and entity behavior analytics (UEBA). Once normal behavior is assessed, UEBA can assign risk scores to unusual activities, highlighting actions and behaviors that exceed specified thresholds.
For example, if a user typically logs in from the US and suddenly logs in from China, this could indicate a potential security threat.
In a modern SIEM system, dynamic grouping automatically sorts entities like users, IP addresses, and devices into categories based on their behavior and traits. This feature adjusts as your network changes, helping you keep your security posture sharp by recognizing similar entities that show similar patterns. Security analysts use it to spot unusual activities and understand what could be a security risk in the ever-changing network.
Modern SIEMs are also great at keeping tabs on service accounts, which run your internal applications but can be targeted for attacks or misuse. By closely monitoring how these accounts are used, SIEMs can spot odd behaviors that might suggest someone is tampering with them. This vigilance helps tighten security around these powerful accounts, making sure they behave as expected and adhere to your security policies.
6. Automated Tracking of Lateral Movement
By analyzing past incidents and the MITRE ATT&CK framework, we know that over 80% of attacks involve lateral movement. This involves attackers attempting to evade detection or gain access to more significant privileges by changing credentials and moving to high-value IP addresses and assets. Your SIEM must be capable of tracking such movements from start to finish by linking related events from different log sources.
7. Better Security Information Model
Legacy SIEMs often rely on a security model based on discrete events. Manually turning a series of events into a structured behavior timeline can be incredibly time-consuming. For more advanced analysis, security data should be stored in a practical format, like a timeline that encompasses the complete scope of each monitored user and entity.
8. Prebuilt Incident Timelines
Investigating with a legacy SIEM typically involves complex queries and a lot of manual data consolidation using basic tools like text editors. This process requires extensive time, deep security knowledge, mastery of query languages, and the ability to interpret the data. With a wealth of enriched data in a suitable information model, a modern SIEM can display all relevant contexts in a user-friendly interface.
9. Incident Prioritization
The volume of data that security operations centers must analyze is overwhelming. It’s not uncommon for large organizations to generate hundreds of millions of log entries daily.
A modern SIEM is designed to sift through this data and reduce the signal-to-noise ratio effectively, allowing your team to focus only on events that demonstrate abnormal behavior. This is crucial for robust security, efficient staff performance, and cost control.
10. Automation of the Threat Detection, Investigation, and Response workflow
SIEM vendors might use different terms for this capability, which includes two key areas:
- Automation: Codify the best responses to specific threat types using response playbooks, provide workflow automation atop your orchestration infrastructure, and enable threat response automation to reduce personnel fatigue.
- Orchestration: Deploy prebuilt connectors to your IT and security infrastructure without needing to script them yourself, and easily manage data flow into and out of your systems, such as access management systems, firewalls, email servers, network access controllers, and other management tools.
An advanced security automation, orchestration, and response solution can liberate your highly skilled analysts to create playbooks while enabling junior analysts to run them. This results in a faster mean-time-to-resolution and fewer full-time employees needed.
The Industry’s Leading AI SIEM
Target threats in real time and streamline day-to-day operations with the world’s most advanced AI SIEM from SentinelOne.
Get a DemoWhat Is A Log Management System?
A log management system (LMS) gathers, sorts, and stores log data and event logs from various sources in one centralized location. Log management systems allow IT teams, DevOps, and SecOps professionals to establish a single point to access all relevant network and application data.
The data should immediately be searchable, which means the IT team can easily access the data they need to make decisions about:
- Network Health
- Resource allocation
- Security management tools
Log Management help determine:
- The data and information IT needs to log
- The format in which IT should log it
- The time period for which IT should save the log data
- How data should be disposed of or destroyed when it is no longer needed
Log management involves several key steps:
- The process starts with gathering log data from various sources in the organization.
- Collected logs are then centralized into a single location, making managing and reviewing the data easier.
- Logs sometimes need to be restructured or reformatted to align with organizational standards or simplify analysis. This step ensures the data is consistent and more accessible to interpret.
- Once transformed, the logs can be analyzed and visualized. This transformation helps identify patterns, detect anomalies, and gain insights from the data.
- Logs are retained for a specified period to support ongoing analysis and then archived for compliance and historical reference.
What are the 5 primary features of a log management solution?
The five primary features of a log management solution are:
1. Data collection
Log management solutions are adept at aggregating log data from various sources. This process seamlessly integrates logs from multiple endpoints and other critical infrastructure components, culminating in a centralized data repository.
The capability to collect data from multiple sources ensures a comprehensive and unified view of system activities, facilitating the identification of potential security events and operational anomalies.
2. Data Normalization
This feature is pivotal within log management, involving the meticulous transformation of raw log data into a standardized format. This feature involves:
- Intricate parsing
- Structuring
- Encoding of the logs
This process ensures uniformity across diverse log types and sources. By converting disparate log formats into a cohesive schema, normalization significantly boosts the efficiency of subsequent analysis and correlation, empowering the system to recognize patterns, anomalies, and indicators of compromise effectively.
3. Searchability
A sophisticated log management system provides advanced search and filtering capabilities to efficiently handle vast volumes of log data. The searchability feature empowers users to execute complex queries, use Boolean operators, and apply multifaceted filters to extract relevant information swiftly.
Enhanced searchability is paramount for pinpointing specific events, conducting thorough investigations, and performing forensic analysis within extensive datasets, facilitating rapid incident response services and threat detection.
4. Retention and Archiving
Retention and archiving functionalities are crucial in ensuring strict compliance with regulatory mandates and log data storage organizational policies. This process includes:
- Implementation of robust data retention policies that govern the duration of the logs’ preservation
- Mechanisms for archiving data for long-term storage
Effective retention strategies enable organizations to maintain historical records for audit purposes, regulatory compliance, and extended analytical requirements, bolstering overall data governance.
5. Reporting and Dashboards
Reporting and dashboard capabilities generate detailed reports and dynamic visualizations that provide actionable insights into system performance, security events, and compliance status. These tools include:
- Customizable dashboards
- Graphical representations of data trends
- Automated report-generation features
These functionalities support informed decision-making and proactive security management by enabling users to monitor real-time metrics, analyze historical data, and synthesize comprehensive visual and textual summaries of log activities.
Difference Between SIEM Vs Log Management
SIEM systems focus on security, integrating features like SIM, SEM, and security event correlation (SEC). They collect and analyze log data from various sources in real-time, detecting indicators of compromise (IOCs) and potential threats quickly to reduce the mean time to detect (MTTD) and enhance security.
In contrast, log management solutions concentrate on collecting, storing, and indexing log data for extensive historical analysis, which is used for compliance and forensic purposes. Although they lack the advanced analytics of SIEM systems, they are required for regulatory compliance and help security analysts manage and analyze logs.
While SIEM solutions excel in real-time processing and scalability, log management systems can struggle with rapid data retrieval due to the large volumes they handle, which may affect quick access needed for investigations or compliance.
Both systems are required for a robust cybersecurity strategy, serving complementary purposes.
SIEM Vs Log Management: What Are The Key Differences
Here is a comparative table discussing the key differences between SIEM vs Log Management.
| FEATURES | SIEM | Log Management |
|---|---|---|
| Primary Function | Real-time threat detection and incident response | Collection, storage, and indexing of log data |
| Data Collection | Aggregates log data from a wide range of sources | Collects log data from various sources |
| Data Analysis | Advanced real-time analysis, event correlation, and threat detection | Basic log analysis, often without real-time capabilities |
| Real-Time Monitoring | Yes, it includes real-time monitoring and alerting | No real-time monitoring; focuses on historical data |
| Event Correlation | Performs sophisticated event correlation and analysis | Limited or no event correlation capabilities |
| Incident Response | Provides tools for immediate response to detected threats | No direct incident response features |
| Search and Filtering | Advanced search capabilities with real-time alerts | Robust search and filtering for historical logs |
| Data Normalization | Yes, normalizes data for consistency and integration | Basic normalization, if any |
| Retention and Archiving | Supports compliance with long-term data retention | Focuses on storage and archiving for compliance |
| Scalability | Scalable with real-time processing capabilities | May encounter bottlenecks with large volumes of data |
| Use Cases | Proactive threat detection, security incident management | Forensic analysis, regulatory compliance |
| Visualization and Reporting | Offers dashboards and detailed reports for insights | Provides basic reporting and visualization capabilities |
SIEM Vs Log Management: How To Choose Between Them?
When deciding between SIEM and log management solutions, the choice often hinges on the organization’s specific security and operational needs.
When to Choose SIEM?
- Real-time security monitoring and incident response
- Use Case: Organizations in sectors like finance and healthcare that handle sensitive data require immediate threat detection and response capabilities.
- Scenario: SIEM systems detect multiple failed login attempts from a single IP address, triggering an immediate alert for further investigation.
- Sophisticated threat detection
- Use Case: Environments where complex attack patterns, such as brute-force attacks or data exfiltration, need to be identified and mitigated.
- Scenario: SIEM correlates logs from network devices, servers, and applications to detect anomalies and sophisticated threats. The system’s advanced algorithms analyze patterns and events to provide actionable insights, enabling proactive threat management.
When to Choose Log Management?
- Comprehensive log data collection and storage
- Use Case: Organizations that need to aggregate and retain logs from various sources for operational insights and compliance.
- Scenario: A cloud service provider uses log management tools to collect logs from different applications and infrastructure components. This choice helps in performance monitoring, troubleshooting application failures, and generating compliance reports.
- Historical data analysis for compliance and troubleshooting:
- Use Case: IT teams require a centralized repository for historical log data to conduct root cause analysis and monitor system performance over time.
- Scenario: Log management tools review historical logs after an application fails to analyze the root cause. Additionally, logs are retained for extended periods to ensure compliance with industry regulations and facilitate audits.
Combining SIEM And Log Management For Stronger Security
Integrating SIEM and log management solutions is crucial for organizations aiming to strengthen security defenses amidst today’s intricate threat environment. Selecting a platform that effectively combines these features, such as SentinelOne’s Singularity™ AI SIEM and Cloud Security offerings, is key.
SentinelOne’s AI-driven SIEM includes:
- Autonomous Security Operations Centers (SOCs) allow organizations to ingest, detect, and respond to threats at machine speed.
- The Singularity™ Data Lake provides extensive visibility across endpoints, cloud, network, and identity, ensuring comprehensive monitoring and analysis of all data sources.
- The platform’s automation of investigation and response processes, a key efficiency factor, decreases the mean time to respond (MTTR) to incidents, enabling security teams to concentrate on strategic tasks rather than manual operations.
Beyond SIEM capabilities, SentinelOne’s cloud security solutions offer a robust framework for managing cloud security posture and compliance. Integrating cloud security posture management (CSPM) with SIEM functionalities allows organizations to efficiently address misconfigurations and assess compliance across their cloud environments. This combined approach delivers real-time analytics and actionable insights, helping organizations maintain a proactive security posture.
By opting for a solution like SentinelOne that merges the advantages of both SIEM and log management, organizations can:
- Enhance threat detection
- Streamline incident response and
- Manage their security posture effectively across various environments.
This all-encompassing approach strengthens defenses against advanced cyber threats and meets the operational needs of modern DevOps and IT teams.
Singularity™ AI SIEM
Target threats in real time and streamline day-to-day operations with the world’s most advanced AI SIEM from SentinelOne.
Get a DemoConclusion
Understanding the differences between log management vs SIEM is essential to choose the right solution for your business. This blog underlined the roles and differences between the solutions, highlighting their equal importance for effective threat detection and security monitoring.
Do remember that working with log management solutions and SIEMs solves different problems. If log management can retain logs and show multiple failed logins, SIEMs alert you of suspicious activity and prevent the breach altogether. Moreover, log management tools can be handled by IT administrators. Setting up a SIEM is also skill-intensive, requiring you to employ cybersecurity specialists to create custom rules, intelligent dashboards, etc.
Integrating both systems is essential for a comprehensive approach to cybersecurity. To understand the nitty-gritty, schedule a demo today to see how SentinelOne can enhance your security strategy with real-time monitoring and robust log management.
FAQs
Log management involves collecting, storing, and analyzing log data to ensure compliance and operational efficiency. SIEM provides real-time threat detection and incident response by collectively analyzing logs and security events.
No, SIEM cannot replace log management, nor can log management replace SIEM. Both serve distinct purposes within an organization’s security framework and are essential for comprehensive cybersecurity management.
SIEM relies on Syslog to send and receive log messages from various sources. Understanding Syslog’s role is key to grasping the full potential of SIEM systems.
The primary advantage of SIEM over a standard log collector is its ability to correlate and analyze log data in real-time for advanced threat detection and incident response rather than just storage and retrieval.
SIEM refers to the technology for threat detection and analysis, while managed SIEM includes those technologies and ongoing management, monitoring, and support provided by a third-party service.

