Businesses and other organizations are rapidly adopting Microsoft Azure’s cloud computing services to host their data. Azure endpoints, especially database endpoints, are especially juicy targets for hackers trying to get into your network and/or steal valuable company data. As a result of Azure’s widespread adoption among businesses and other organizations, there is an ever-increasing need for solid endpoint protection to ensure that intruders cannot access these often crucial files.
In this post, we will explain what Azure endpoint protection is, why your organization needs it, how to configure your Azure environment, and how to implement Azure endpoint protection.
 What Is Azure Endpoint Protection?
What Is Azure Endpoint Protection?
As you may know, an “endpoint” is another word for a device connected to a network. They are the means through which attackers look to attack your network. These can be mobile devices, virtual machines, or even servers. In Azure, endpoints may also refer to connection points that allow devices to connect to Azure cloud-based services, or services to connect to services. In other words, some Azure endpoints may simply connect other endpoints. But they still need to be protected.
Azure endpoint protection refers to the security tools designed to protect these endpoints from threats and vulnerabilities. They include Microsoft Defender for Endpoint, Azure Security Center, Network Security Groups (NSGs), SentinelOne’s Singularity App, and more.
 These cloud-based tools allow you to monitor the state of your devices and virtual machines. Azure Security Center allows you to continuously monitor your endpoints and scan for malware, and Microsoft Defender for Endpoint helps organizations scan their networks for threats. While Azure Security Center is the most popular, Microsoft Defender for Endpoint uses a combination of advanced features, one of which includes Microsoft’s cloud security analytics, where, “leveraging big-data, device learning, and unique Microsoft optics across the Windows ecosystem, enterprise cloud products (such as Office 365), and online assets, behavioral signals are translated into insights, detections, and recommended responses to advanced threats.”
These cloud-based tools allow you to monitor the state of your devices and virtual machines. Azure Security Center allows you to continuously monitor your endpoints and scan for malware, and Microsoft Defender for Endpoint helps organizations scan their networks for threats. While Azure Security Center is the most popular, Microsoft Defender for Endpoint uses a combination of advanced features, one of which includes Microsoft’s cloud security analytics, where, “leveraging big-data, device learning, and unique Microsoft optics across the Windows ecosystem, enterprise cloud products (such as Office 365), and online assets, behavioral signals are translated into insights, detections, and recommended responses to advanced threats.”
How Does Azure Endpoint Protection Work?
The Azure Security Center is the most popular tool for securing your Azure endpoints. It provides a centralized hub through which you can enable security features for your environment.
In the Security Center, you can configure security policies for specific resource groups (more on those later) or services. The tool also provides monitoring and data collection, giving users information about virtual machines and providing alerts when security threats, such as malware, are discovered. With the information the tool gives you, you can review the issues and implement additional security measures as you deem fit.
Why Is Azure Endpoint Protection Important?
Azure endpoints can be a gateway to your larger cloud environment. That is why hackers will relentlessly attack those endpoints in order to compromise your network. Endpoint protection minimizes these risks by providing malware detection and continuous system monitoring. Microsoft Defender for Endpoint also provides automated threat detection and security alerts along with detailed security analysis. This reduces workloads for IT teams.
However, there is a plethora of lesser-known benefits that Azure’s endpoint protection tools provide. Microsoft Defender for Endpoint, for example, can be used as a centralized monitoring platform. It can automate investigations and remediation of security issues, reducing the manual workload for IT teams. It can also be integrated with Microsoft 365 Defender, which gathers data from multiple security services, including Microsoft Defender for Office 365 and Microsoft Cloud App Security. This centralized view helps security teams gain a holistic understanding of their security.
 Endpoint protection may also be a regulatory necessity. Since several industries have strict laws on data privacy and stipulations around how customer data needs to be protected, organizations usually need to have some form of endpoint protection against cloud-based vulnerabilities. Failure to do so may lead to harsh fines or legal actions, making securing your Azure-based assets even more critical.
Endpoint protection may also be a regulatory necessity. Since several industries have strict laws on data privacy and stipulations around how customer data needs to be protected, organizations usually need to have some form of endpoint protection against cloud-based vulnerabilities. Failure to do so may lead to harsh fines or legal actions, making securing your Azure-based assets even more critical.
Sentinel One’s Singularity App: Unified Protection for Your Azure Environment
Our Singularity platform is a unique tool useful for monitoring Azure environments. As our data sheet says,
SentinelOne and Microsoft customers benefit from a first-of-its-kind integration between SentinelOne’s Singularity XDR platform and Azure Active Directory. Through the integration, organizations benefit from autonomous response capabilities that help security professionals respond to cyber threats faster. By using SentinelOne App for Azure Active Directory, organizations interconnect endpoint security and their identity service provider. As a result, when an endpoint is compromised, the impacted user identity information is transmitted in real-time to Azure Active Directory, and Conditional Access can quickly enforce multi-factor authentication (MFA), restrict access, or limit access.
SentinelOne’s Singularity platform monitors ongoing threats and updates them in real-time within the Azure Active Directory, with a detailed list of compromised users or apps within your network. With SentinelOne, you can define security protocols as well as mitigate already detected threats. You can watch the Singularity platform in effect in our Singularity for Azure Active Directory demo.
Setting Up Your Azure Environment
Let’s now talk about how you can set up an Azure environment for your organization.
Configuring and Deploying Your Environment
The first step involves creating an Azure account. Once users create an Azure account, they can then log into the Azure Portal, which is a portal for managing and deploying Azure resources. Once that is done, you must define what apps and services you may need in your Azure environment. This allows you to define the amount of resources that you will be using. To do this, you need to create a resource group in Azure. Resource groups are containers used to manage Azure resources and services. In a resource group, you can group related Azure services together.
With a resource group set up, you can then select the services you require in the group. This can be done through the Create a Resource button in the Azure services subsection. You need to consider the size and performance requirements for each resource, as these affect your environment.
 You then need to set up networking by creating a Virtual Network (VNET) to define your address space and subnets. For added security, you should implement a Network Security Group (NSG) to control the traffic flow from your resources. This is a form of access control. At this point, you can set up a virtual machine with your preferred operating system. Consider using Virtual Machine Scale Sets for automatic scaling. You can then configure storage accounts based on your organization’s requirements. File shares can be used for shared storage across multiple virtual machines, while blob storage can be used for unstructured data.
You then need to set up networking by creating a Virtual Network (VNET) to define your address space and subnets. For added security, you should implement a Network Security Group (NSG) to control the traffic flow from your resources. This is a form of access control. At this point, you can set up a virtual machine with your preferred operating system. Consider using Virtual Machine Scale Sets for automatic scaling. You can then configure storage accounts based on your organization’s requirements. File shares can be used for shared storage across multiple virtual machines, while blob storage can be used for unstructured data.
Azure Active Directory is Azure’s built-in identity and access management system. You can manage user permissions and apply Role-Based Access Control (RBAC) to assign specific roles to users or groups. It is the main access control hub for Azure.
Creating and Configuring a Dev Center in Azure Deployment Environments Using the Azure portal
For your team to effectively deploy Azure Environments, you need to set up a dev center. Your team is responsible for setting up the dev center, creating projects, and providing access to development teams. Microsoft gives a quickstart guide to deploying an Azure environment, which outlines the following steps:
- Sign in to the Azure portal.
- Search for Azure Deployment Environments, and then select the service in the results.
- In Dev centers, select Create.
- In Create a Dev Center, on the Basics tab, select or enter the following information:
- Select Review + Create.
- On the Review tab, wait for deployment validation, and then select Create.
- You can check the progress of the deployment in your Azure portal notifications.
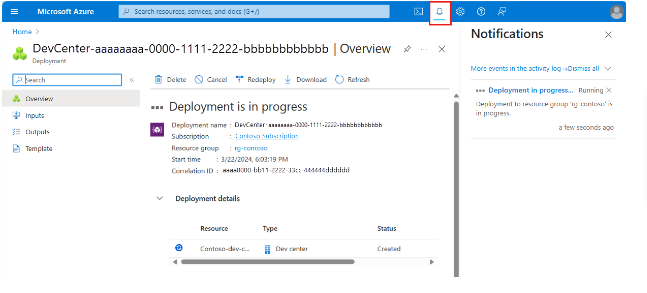
8. When the creation of the dev center is complete, select Go to the resource. Confirm that you see the dev center overview pane.
Protect Your Endpoint
See how AI-powered endpoint security from SentinelOne can help you prevent, detect, and respond to cyber threats in real time.
Get a DemoProtecting Your Azure Environment Is Crucial
As you may now know, your Azure endpoints could be crucial gateways to your larger network. As such, attackers spare no effort in trying to attack them. That is why endpoint protection tools for your Azure environment remain necessary. Setting up your Azure environment is a complex task, and proper endpoint protection involves the use of tools such as Microsoft Defender for Endpoint, Azure Security Center, Network Security Groups (NSGs), and more. SentinelOne’s Singularity is also a useful tool for monitoring and securing your environment.
Azure endpoint protection might be hard, but it is crucial to protect your resources. Hopefully, you should now be able to set up your Azure environment, and whatever your aim is with Azure, make sure to consider adding SentinelOne’s Singularity platform to your protective arsenal.
Leading the Way in Endpoint Security
See why SentinelOne has been named a Leader four years in a row in the Gartner® Magic Quadrant™ for Endpoint Protection Platforms.
Read Report
FAQs
An endpoint is typically defined as a means through which attackers target a network or system. In Azure, endpoints can be virtual machines, applications, or service endpoints used to connect other user devices to cloud-based applications and services.
Azure endpoint protection refers to the tools used and measures that may be taken to protect Azure endpoints. They include Azure Security Center and Microsoft Defender for Endpoint.
The main tool for setting up endpoint protection within Azure is the Azure Security Center. It provides a centralized hub through which you can monitor your environment, configure security policies, and set up additional security measures.

