Antivirus software protects individual devices from malware by scanning files and blocking known threats. As attacks became more advanced, endpoint detection and response (EDR) tools emerged as a next-generation defense, offering deeper visibility by monitoring endpoints like laptops and servers for suspicious activity. However, EDR only focuses on devices and lacks a broader view of the network, emails, or cloud services. To fill this gap, security information and event management (SIEM) systems were developed to gather and analyze data from various sources across an organization.
SIEM provides a more comprehensive view but can overwhelm teams with alerts and lacks context for prioritizing them effectively. This led to the rise of extended detection and response (XDR), which combines data from endpoints, networks, and other sources for a unified threat detection approach. Azure XDR, built on Microsoft’s security tools, provides this integrated protection, allowing teams to quickly respond to threats across their entire environment.
 What Is Azure XDR?
What Is Azure XDR?
Azure XDR (extended detection and response) is Microsoft’s solution for unifying security across an organization. Traditional tools like antivirus, EDR, and SIEM often work separately, each focusing on only part of a threat. However, Azure XDR integrates data from many sources—like endpoints, networks, emails, and cloud applications—using Azure Sentinel, Azure Defender, and Microsoft Threat Intelligence. As a result, security teams get a real-time, complete view, which allows them to detect and respond to threats faster.
Imagine a user opens a malicious email with hidden malware. The malware spreads quickly, moving through the network, escalating privileges, and stealing data. In a traditional setup, each security tool might catch part of the attack but not share information. This lack of coordination delays detection and slows response. Meanwhile, the team must manually check logs from different tools, wasting time. But with Azure XDR, everything comes together in one platform. It connects the dots, triggers automatic actions to contain the threat, and alerts the team immediately, reducing response time and limiting damage.
Core Components of Azure XDR
Azure XDR (extended detection and response) relies on three essential components: Azure Sentinel, Microsoft Defender for Cloud, and Microsoft Threat Intelligence. Each plays a unique role, and together, they create a powerful, unified security solution that detects, investigates, and responds to threats effectively.
 Azure Sentinel
Azure Sentinel
Azure Sentinel acts as the command center for Azure XDR. It’s a cloud-native SIEM (security information and event management) and SOAR (security orchestration automated response) solution. Sentinel gathers security data from multiple sources, like endpoints, networks, and cloud applications. It uses AI and machine learning to analyze this data and identify threats in real-time. Sentinel connects alerts from different sources into a single, unified incident, giving security teams a comprehensive view of an attack. It also supports automated responses using playbooks, which trigger actions like isolating compromised systems or blocking malicious IPs. With Azure Sentinel, you get a clear, consolidated view of security across your entire environment, enabling faster detection and response.
Microsoft Defender for Cloud
Microsoft Defender for Cloud focuses on protecting cloud and on-premises resources. It continuously monitors your workloads—such as virtual machines, databases, and containers—for suspicious activity, vulnerabilities, and misconfigurations. When Defender for Cloud detects a threat, it generates an alert and sends it to Azure Sentinel. Sentinel then correlates this alert with other data sources, helping to identify the full scope of the attack. Defender for Cloud plays a crucial role in Azure XDR by ensuring that all workloads are protected and no threat is missed. It also provides security recommendations to strengthen defenses, helping you stay ahead of potential attacks.
Microsoft Threat Intelligence
Microsoft Threat Intelligence provides Azure XDR with the latest information about emerging threats. It continuously gathers data from Microsoft’s vast global network of sensors and external sources, identifying new attack techniques, malicious IP addresses, domains, and other indicators of compromise. This threat intelligence feeds directly into both Azure Sentinel and Microsoft Defender for Cloud.
In Azure Sentinel, this intelligence enhances detection rules and fine-tunes the system to recognize new and evolving threats. It helps reduce false positives by adding context, so security teams can focus on real threats. In Microsoft Defender for Cloud, it enriches alerts with detailed threat information, making it easier for security teams to understand the nature and impact of each threat. By keeping the entire Azure XDR system up-to-date with the latest threat data, Microsoft Threat Intelligence ensures quicker, more accurate responses and helps organizations stay one step ahead of attackers.
How They Work Together in Azure XDR
These components connect seamlessly to provide a complete security solution
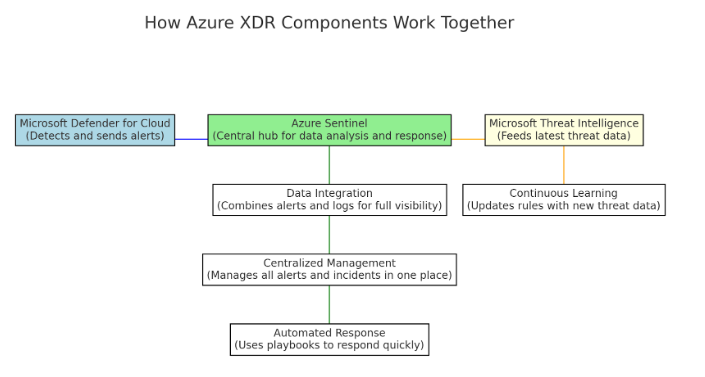
- Data Integration and Correlation: Defender for Cloud sends alerts to Sentinel, which combines these with other data sources to offer a complete view of threats.
- Centralized Management: Sentinel acts as the control center, where all alerts and incidents are managed in one place. This reduces complexity and improves visibility.
- Automated Response: Sentinel uses playbooks to automate responses to detected threats, speeding up containment and reducing manual work.
- Continuous Learning: Microsoft Threat Intelligence continuously updates Sentinel and Defender for Cloud with the latest threat data, keeping detection rules sharp and responses effective.
Leading the Way in Endpoint Security
See why SentinelOne has been named a Leader four years in a row in the Gartner® Magic Quadrant™ for Endpoint Protection Platforms.
Read Report
Key Features of Azure XDR
Azure XDR offers several key features that make it a powerful security solution, detailed below.
1. Automated Threat Detection
Azure XDR uses AI and machine learning to analyze data from various sources, such as endpoints, networks, and cloud services, in real-time. It continuously learns from this data, identifying patterns that indicate potential threats, such as unusual login attempts or abnormal network traffic. By using behavioral analytics, it understands what’s normal for a user or system and detects deviations that could signal an attack. This automated detection reduces the need for manual investigation, quickly identifies threats, and prioritizes them based on severity, enabling faster and more efficient responses to incidents.
2. Deep Integration with Microsoft Ecosystem
Azure XDR seamlessly integrates with a wide range of Microsoft services and products, including Microsoft 365, Microsoft Defender for Identity, Microsoft Defender for Endpoint, Azure Active Directory, and more. This deep integration allows for comprehensive visibility across the entire digital estate, from cloud to on-premises environments. Other XDR solutions might not offer the same level of integration with such a broad suite of productivity, identity, and security tools.
3. Machine Learning and AI Capabilities
Azure XDR leverages Microsoft’s advanced AI and machine learning models to enhance threat detection and response. These capabilities help identify anomalies, detect unknown threats, and reduce false positives by learning from vast amounts of data across Microsoft’s global network. The depth and sophistication of these AI models are unique to Microsoft, as they benefit from Microsoft’s significant investments in AI research and development.
4. Unified Security Management Across Multi-Cloud and Hybrid Environments
Azure XDR is built to support multi-cloud and hybrid environments, providing advanced threat detection and response capabilities across Azure, AWS, Google Cloud, and on-premises resources. This cross-platform support ensures consistent security management regardless of where the resources reside, which many other XDR solutions may lack, especially those that are more focused on a single cloud provider.
5. Advanced Automation and Orchestration With Playbooks
Azure Sentinel, a core component of Azure XDR, offers robust automation and orchestration capabilities through playbooks. These playbooks are powered by Azure Logic Apps and can automate complex workflows, such as threat mitigation actions, notifying security teams, or integrating with third-party tools. This level of automation helps reduce response times and human error, which is more advanced than the automation features in some other XDR platforms.
 6. Built-in Compliance and Governance Tools
6. Built-in Compliance and Governance Tools
Azure XDR includes built-in compliance tools that help organizations meet regulatory requirements. Features like Azure Policy, Azure Blueprints, and Azure Security Center’s regulatory compliance dashboard allow for continuous monitoring and assessment against industry standards. This built-in compliance capability is more comprehensive compared to many other XDR solutions, which may require additional tools or integrations to achieve the same level of regulatory adherence.
7. Customizable Analytics and Dashboards
Azure XDR offers highly customizable analytics and dashboards, allowing security teams to create tailored views that meet their specific needs. Sentinel’s custom workbooks and hunting queries enable organizations to visualize data in various ways, which can be more flexible than the standard dashboards provided by other XDR solutions.
8. Cost-Effectiveness and Scalability
Azure XDR can be more cost-effective for organizations already using Microsoft services, as it leverages existing licenses and infrastructure. It scales easily with the Azure platform, allowing organizations to grow without incurring significant additional costs. Other XDR solutions may require separate licenses and infrastructure, potentially increasing costs and complexity.
Use Cases for Azure XDR
Azure XDR is suitable for a wide range of security use cases:
- Protecting Enterprise Environments: Large organizations with complex IT environments can use Azure XDR to unify their security posture across cloud and on-premises resources.
- Securing Remote Workforces: With more employees working remotely, Azure XDR provides comprehensive protection for remote devices and cloud applications.
- Compliance and Regulatory Adherence: Azure XDR helps organizations meet compliance requirements by providing advanced threat detection and automated response capabilities.
- Threat Hunting and Investigation: Security teams can use Azure XDR’s advanced analytics and machine learning tools for proactive threat hunting and investigation.
Discover Unparalleled Endpoint Protection
See how AI-powered endpoint security from SentinelOne can help you prevent, detect, and respond to cyber threats in real time.
Get a DemoGetting Started With Azure XDR
To deploy Azure XDR, you need to set up Azure Sentinel, integrate security tools, and follow best practices.
1. Setting up Azure Sentinel
First, open the Azure Portal and search for Azure Sentinel. Click Create to add Azure Sentinel to your subscription. Choose a Log Analytics workspace to store the data. If you don’t have one, create a new workspace by selecting Create a new workspace.
Next, connect the required data sources. Go to Data connectors in Azure Sentinel. Find connectors for sources like Microsoft 365 Defender, Azure Active Directory (Azure AD), and Office 365. Follow the instructions to enable each connector. For example, select Office 365, choose the subscriptions and tenants, and click Connect. For third-party tools, use available connectors or deploy agents like Syslog or Common Event Format (CEF).
2. Integrating Security Tools
Integrate Azure XDR with all your security tools. In Data connectors in Azure Sentinel, connect Microsoft Defender products like Defender for Endpoint, Defender for Identity, and Defender for Cloud. Follow the steps to authorize and link these services. This setup sends alerts and signals directly to Azure Sentinel.
For non-Microsoft tools, use Sentinel’s built-in connectors. Options include SentinelOne, Cisco ASA and Symantec. If a connector is unavailable, use CEF or Syslog to import logs and data.
3. Automating Responses with Playbooks
Automate responses to reduce manual work and speed up threat mitigation. Go to Automation in Azure Sentinel. Create playbooks using Azure Logic Apps. Configure them to isolate endpoints, block IP addresses, or notify the team. Set Automation Rules to trigger playbooks based on specific alerts.
Best Practices for Managing Azure XDR
- Regularly Review and Update Rules: Keep your detection rules and analytics settings updated with the latest threat intelligence.
- Use Machine Learning Models: Enable Azure Sentinel’s User and Entity Behavioral Analytics (UEBA) to detect anomalies and insider threats.
- Continuously Monitor and Refine: Use Hunting Queries in Azure Sentinel to find new threats. Enable Microsoft Threat Intelligence for updates.
- Train Your Security Team: Make sure your team knows how to use Azure Sentinel for detection, hunting, and response. Use Microsoft’s training resources.
By following these steps, you can set up Azure XDR, integrate it effectively, and maintain a strong security posture.
Challenges and Considerations
While Azure XDR offers strong security capabilities, there are several challenges and considerations to keep in mind. By considering the factors below, you can ensure a smooth Azure XDR deployment that meets your security requirements.
#1. Cost Implications
Azure XDR’s pricing depends on data ingestion, retention, and the number of connected services. Azure Sentinel charges based on the daily amount of ingested data and retention duration. Costs can increase with higher volumes of security data. To manage expenses, estimate data ingestion rates carefully. Use basic logs for less critical data. Consider data archiving and setting retention policies to reduce storage costs while staying compliant.
#2. Organizational Readiness and Training
Deploying Azure XDR requires changes in how your security team operates. Prepare your team by providing training on Azure Sentinel, Microsoft Defender, and related components. Encourage them to use Microsoft’s training resources, documentation, and hands-on labs. Familiarize your team with automated workflows, threat hunting, and incident response using Azure Sentinel’s playbooks. Ensure your current security infrastructure supports Azure XDR integration. Address any gaps in advance.
#3. Integration Complexity
Integrating Azure XDR with existing tools can be challenging, especially with a mix of third-party solutions. Plan for potential issues by identifying available connectors and those needing custom configuration. Allocate time for testing to confirm data sources connect properly and provide accurate information. Consider involving a team or partner experienced with Azure to simplify integration.
#4. Data Privacy and Compliance
Azure XDR processes large amounts of data, which may include sensitive information. Ensure compliance with regulations like GDPR, HIPAA, or CCPA. Regularly audit your configurations for data governance. Use data anonymization and encryption to protect sensitive information while maintaining visibility into threats.
Protect Your Endpoint
See how AI-powered endpoint security from SentinelOne can help you prevent, detect, and respond to cyber threats in real time.
Get a DemoAn All-in-one Solution
Azure XDR provides a comprehensive, integrated approach to security. By combining Azure Sentinel, Azure Defender, and Microsoft Threat Intelligence, it offers an all-in-one solution for detecting and responding to threats. With its automated capabilities, advanced analytics, and seamless integration, Azure XDR helps security teams work more efficiently. Whether you’re protecting an enterprise environment or securing remote workforces, Azure XDR is designed to keep you one step ahead of cyber threats. If you’re looking to strengthen your security posture, Azure XDR is a great place to start.
FAQs
Azure XDR is suitable for a variety of organizations, from small businesses to large enterprises. It is particularly beneficial for organizations with complex IT environments that include multiple cloud platforms and on-premises resources. Additionally, businesses that have remote workforces or are subject to strict compliance regulations can greatly enhance their security posture with Azure XDR.
While traditional SIEM solutions focus primarily on aggregating logs and alerts from different sources, Azure XDR takes a more integrated approach. It combines data from endpoints, networks, and cloud services to provide a holistic view of security events. Azure XDR also emphasizes automated threat detection and response, reducing the burden on security teams to manually analyze and act on alerts.
Yes, Azure XDR can be integrated with a variety of third-party security tools. Azure Sentinel offers built-in connectors for many popular security products, and for those that don’t have native support, logs can be ingested using Common Event Format (CEF) or Syslog. This flexibility allows organizations to create a more cohesive security ecosystem.
Automation plays a crucial role in Azure XDR, especially through features like playbooks in Azure Sentinel. These playbooks enable automated responses to security incidents, such as isolating compromised endpoints or blocking malicious IP addresses. Automation helps speed up the incident response process, reduces human error, and allows security teams to focus on more complex tasks.
Azure XDR includes built-in compliance tools that assist organizations in meeting various regulatory requirements. Features such as Azure Policy, Azure Blueprints, and continuous monitoring against industry standards help ensure that security practices align with compliance frameworks. This built-in capability simplifies the process of maintaining regulatory adherence compared to other XDR solutions that may require additional integrations.

