Endpoint protection is a security solution that protects devices, also known as endpoints, connected to a network, such as PCs, laptops, smartphones, and servers. With the development of remote work and the rapidly increasing rate of cyber threats, particularly malware, these endpoints have become susceptible entry points for cybercriminals attempting to breach an organization’s network, making their protection vital for overall security.
Modern endpoint security combines tools like antivirus, firewalls, and advanced threat detection to prevent known attacks and mitigate future risks.
 What Is Malware Endpoint Protection?
What Is Malware Endpoint Protection?
Malware endpoint protection takes this a step further, focusing specifically on defending against malicious software. From ransomware that encrypts valuable data to trojans that create backdoors for attackers, malware presents challenges that require specialized protection. This protection includes a range of techniques to prevent, detect, and respond to malware threats, ensuring that endpoints remain secure from these evolving cyber risks.
In essence, malware endpoint protection ensures that every device connected to a network is secure from potential threats, providing real-time monitoring, prevention, and incident response capabilities.
 Why is Malware Endpoint Protection Essential?
Why is Malware Endpoint Protection Essential?
Malware endpoint protection is crucial because endpoints, like computers and mobile devices, are primary targets for cyberattacks. These devices often hold sensitive data and serve as gateways to larger networks. Without proper security, malware can infiltrate these endpoints, leading to data breaches, financial loss, and disruption of operations.
Effective protection helps prevent malware from spreading across networks, defends against various threats, and ensures the integrity of systems. By safeguarding endpoints, organizations can maintain data security and minimize risks.
Understanding Malware
To effectively protect your endpoints against malware, it is essential to understand exactly what you are up against and the various types of threats.
Malware or malicious software is a program or software that is designed to disrupt, damage, or gain unauthorized access to a computer system. It can take many forms and serve various purposes, from stealing sensitive information to disrupting operations.
Types of Malware
- Virus: A virus is a self-replicating program that attaches itself to other files or programs, often causing damage when executed. It remains dormant until the infected file or program is opened or executed by the user when the virus becomes active. Once activated, it can corrupt files, steal information, or disable systems.
- Worm: Worms are also self-replicating malware that spreads without any user interaction or the need to be executed. Worms automatically exploit vulnerabilities in networks or systems. Once inside a system, worms replicate themselves across other devices.
- Trojan: A trojan is a malware that disguises itself as legitimate software to trick users into installing it. It requires human interaction to activate, and when this happens, it grants attackers unauthorized access to the system, often creating a backdoor for further attacks.
- Ransomware: A type of malware that encrypts a victim’s files or locks them out of their system entirely, demanding a ransom to restore access. Once activated, the malware spreads rapidly through a network, often encrypting entire systems or data repositories.
- Spyware: Malware designed to monitor user activity and collect sensitive information. Spyware operates in the background without the user’s knowledge, targeting data like passwords and browsing habits.
- Adware: Adware is software that automatically delivers unwanted advertisements to users, typically in the form of pop-ups or banners. While not always malicious, adware can slow down systems, collect browsing data, and open the door to more harmful malware.
Common Attack Vectors
Some of the common ways users unintentionally introduce malware into their systems include:
- Phishing emails with malicious attachments or links
- Drive-by downloads from compromised or malicious websites
- Infected USB drives or external storage devices
- Malicious software bundled with legitimate applications
- Downloading pirated software, media, or files from untrustworthy sources
How Malware Endpoint Protection Works?
Malware endpoint protection uses a multi-layered approach to secure devices connected to a network. Here is a breakdown of how it works:
- Continuous Monitoring: The first step involves constantly monitoring all endpoints. This process checks for any unusual or suspicious activity on the network. Monitoring tools continuously scan for signs of malware or abnormal behavior, ensuring that threats are caught as early as possible.
- Threat Detection: After monitoring, the system analyzes any detected anomalies using behavioral analysis, AI, and machine learning. These technologies look for patterns or behaviors that suggest malware is present. This layer is crucial for detecting known threats and newer, more sophisticated attacks that traditional methods might miss.
- Incident Response: Automated incident response services kicks in once a threat is detected. The endpoint protection system isolates the infected device to prevent the spread of malware and uses automated malware removal tools to neutralize the threat. This fast and efficient response minimizes the impact of the attack.
- Remediation: After the incident is resolved, the final step is to return the system to its pre-attack state. Automated remediation tools help restore affected files and systems, ensuring that any damage done by the malware is repaired and the endpoint is secure once again.
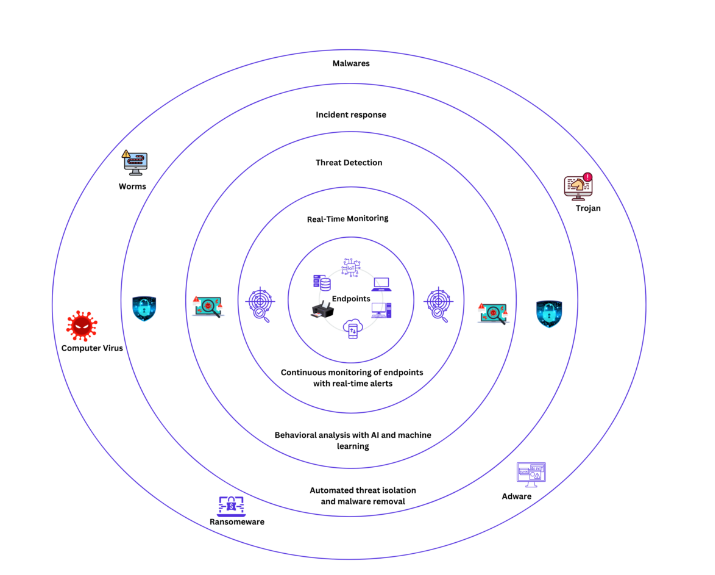
Key Features of Effective Malware Endpoint Protection
An effective malware endpoint protection system is not just about detecting and responding to threats. It must incorporate several key features that allow it to stay ahead of modern malware.
- Real-Time Monitoring: Real-time monitoring involves continuously observing system activities, network traffic, and endpoint behaviors as they happen. It keeps a constant watch for suspicious activity, alerting security teams the moment a potential threat is detected.
- Signature-Based Detection: A “signature” in cybersecurity is a unique pattern or sequence of code that identifies a specific type of malware. Signature-based detection works by scanning files or programs and comparing them to a database of known malware signatures. If the system finds a match, it flags the file as malicious and responds by quarantining or removing it.
- Heuristic Analysis: Heuristic analysis examines a file or program’s underlying structure or code to detect possible threats. Instead of relying on known malware signatures, it uses predefined rules and algorithms to flag suspicious patterns or commands that often indicate malicious intent.
- Behavioral Analysis: Behavioral analysis focuses on how a file or program acts in real-time, observing its behavior as it runs. Instead of analyzing the code itself, it looks for actions that indicate malicious intent. If a program behaves in a way that deviates from normal patterns, it is flagged as potentially harmful. It detects threats based on their actions rather than their code.
- Sandboxing: Sandboxing is like a quarantine area for suspicious programs. When the security software is not sure if a program is safe, it allows the system to run malicious programs in an isolated environment where their behavior can be observed. The sandbox is separate from the rest of the system, so if the program turns out to be malicious, it is flagged without posing a risk to the network.
Endpoint Protection Solutions
- Antivirus Software: Antivirus software is the traditional method of detecting and removing known malware signatures. It works by scanning files on a device and comparing them to known virus signatures in a database. While it may be effective against older, well-documented threats, antivirus software may struggle to contain newer, more sophisticated malware.
- Endpoint Detection and Response (EDR): EDR solutions provide advanced detection and response capabilities. It provides visibility into endpoint activity, detects threats, and responds to incidents by continuously monitoring endpoints and detecting suspicious activity in real-time. EDR tools detect known threats and analyze behavior patterns to identify previously unknown threats. Once an issue is detected, EDR provides tools for incident response, such as isolating infected systems and initiating remediation.
- Unified Endpoint Management (UEM): UEM is a security solution that centralizes the management of all endpoints—computers, mobile devices, IoT devices—under one platform. UEM allows organizations to monitor, manage, and secure all devices using a single tool. This security measure is valuable in remote work environments where various device types connect to the corporate network from different locations.
- Next-Generation Antivirus (NGAV):NGAV is an advanced approach to antivirus software solutions that uses artificial intelligence, machine learning, and behavioral analysis to identify and contain threats rapidly. It is protection that addresses the limitations of traditional antivirus software. NGAV is also a good security solution for spotting unknown or “zero-day” attacks that evade traditional defenses.
- Managed Detection and Response (MDR): MDR is a security service that combines technology and human intelligence to minimize the impact of threats and breaches through rapid detection. These services include continuous threat monitoring, incident response, and forensic analysis. For organizations with limited internal security resources, MDR provides resources to use advanced tools and experienced analysts without building a full in-house team or additional staffing.
Discover Unparalleled Endpoint Protection
See how AI-powered endpoint security from SentinelOne can help you prevent, detect, and respond to cyber threats in real time.
Get a DemoWrapping Up
Malware poses a significant threat to organizations of all sizes. With cyber threats constantly becoming more sophisticated, reliable security solutions are essential. Organizations should invest in robust endpoint protection, as this helps to protect their operations and reputation.
There is a wide range of cybersecurity solutions that organizations can use to protect their endpoints from malware, and SentinelOne offers endpoint protection that combines AI-driven threat detection, real-time monitoring, and automated response capabilities, making it a suitable option for organizations that need thorough endpoint security.
FAQs
Endpoint protection is a more comprehensive security solution that includes antivirus, firewall, threat detection, and response capabilities, whereas antivirus focuses mainly on detecting and removing known malware.
Organizations should look for solutions that can handle a wide range of threats, offer real-time monitoring, provide automated incident response, and integrate with other security tools. Scalability and ease of management across multiple devices are also important factors.
Endpoint security protects devices connected to a network, while network security focuses on securing the overall network infrastructure, including firewalls, intrusion prevention systems, and secure communication between devices.

