The cloud-shared responsibility model is a critical concept in cloud security. Our guide provides a comprehensive overview of this model, explaining the roles and responsibilities of cloud providers and customers in ensuring the security of cloud-based resources.
Learn about the different layers of the shared responsibility model, including physical infrastructure, network controls, and application-level security.

Top Security Risks Customers Must Tackle in the Cloud Shared Responsibility Model
As organizations evaluate cloud security for their business, senior leadership and technical leads should consider the risks that they and their customers face within the Cloud Shared Responsibility Model. These risks can be categorized into the following topics:
- Unauthorized access – Organizations need to ensure that they have strong authentication and access controls to prevent unauthorized access to sensitive data and applications. This includes managing user identities, enforcing strong passwords and multifactor authentication, and limiting access to sensitive data and applications based on user roles and permissions.
- Data breaches – Ensuring proper encryption and data protection mechanisms helps organizations protect their data at rest and in transit. This includes using robust encryption algorithms, implementing secure data transfer protocols, and monitoring for unusual data access patterns and activities.
- Malware and viruses – Malware and viruses can infect cloud environments through various means, such as email attachments, software downloads, or compromised endpoints. Organizations must invest in proper antivirus and malware protection and perform regular software updates and patches to prevent vulnerabilities.
- Insider threats – Insider threats, such as employees or contractors with authorized access to cloud resources, can pose a significant security risk. Proper access controls and monitoring mechanisms can be put in place to detect and prevent insider threats. This includes monitoring user activities, implementing data loss prevention measures, and conducting regular security audits and assessments.
- Compliance violations – Cloud customers also need to be aware of compliance regulations and ensure they follow them. This includes regulations such as HIPAA, PCI-DSS, and GDPR. Under these regulatory frameworks, organizations are legally required to ensure that their cloud environment meets security and privacy standards and has proper data management and retention policies.
By addressing these security risks, customers can help ensure their cloud environment’s security and reliability while complying with regulatory requirements and protecting their sensitive data and applications.
Defining the Importance of the Cloud Shared Responsibility Model
The Cloud Shared Responsibility Model is a vital concept in cloud security that lays out the responsibilities of both cloud service providers and their customers. This model ensures both parties understand their roles in securing cloud assets and prevents confusion and misunderstandings.
In the model, responsibilities regarding securing and managing cloud environments are clearly outlined:
- Cloud service providers are generally responsible for securing the cloud infrastructure, including the physical data centers, networking, and server hardware.
- Customers are responsible for securing their applications, data, and operating systems that run on the cloud infrastructure.
The Cloud Shared Responsibility Model is crucial in cloud security because it clarifies who is responsible for what, ensuring comprehensive and effective cloud security. Without this model in place, it is very difficult for parties to determine who is responsible for cloud security, resulting in gaps in security coverage or duplication of efforts.
 CNAPP Market Guide
CNAPP Market Guide
Get key insights on the state of the CNAPP market in this Gartner Market Guide for Cloud-Native Application Protection Platforms.
Read GuideIdentifying the Difference Between Cloud Service Models
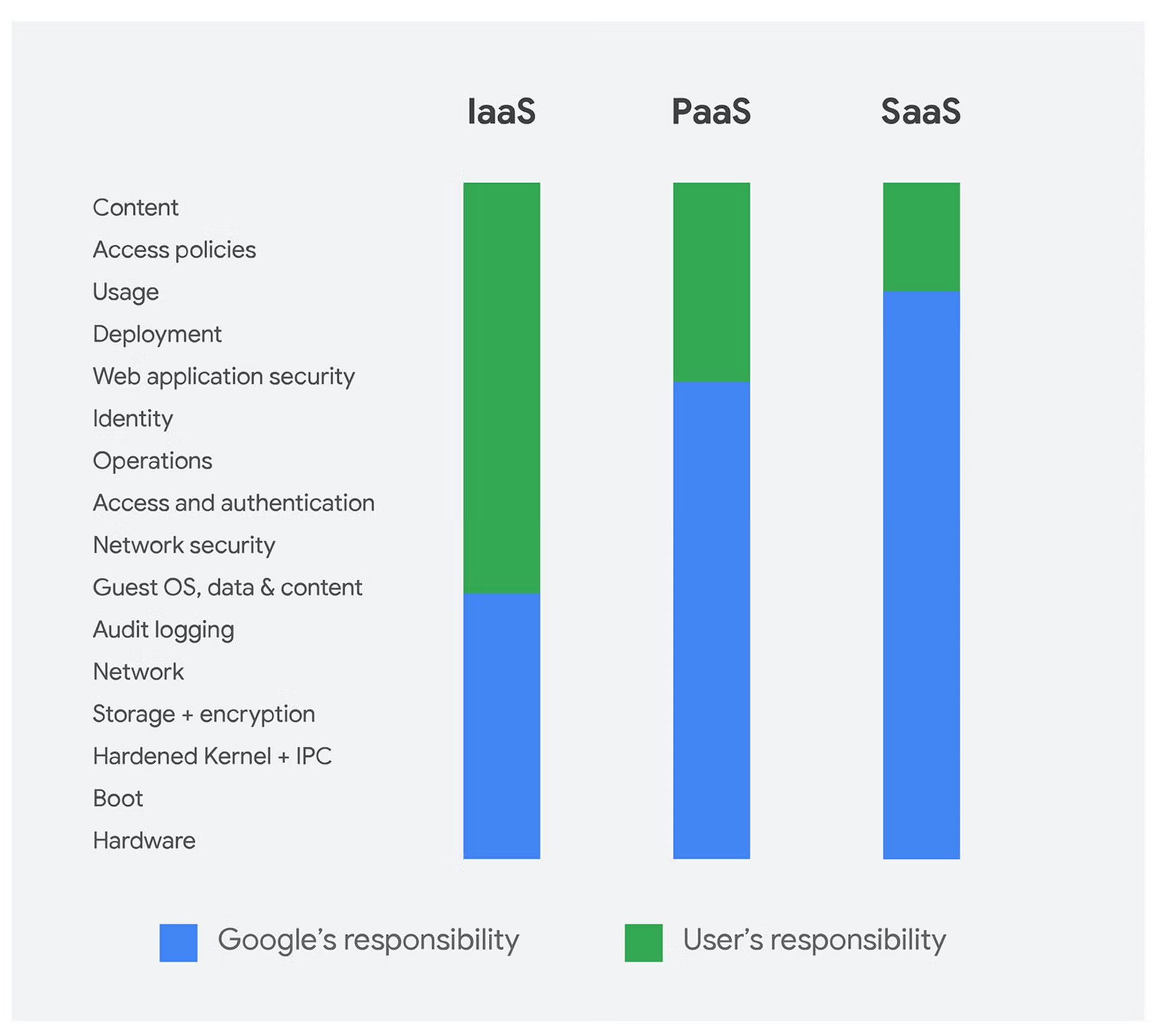
Infrastructure-as-a-Service (IaaS), Platform-as-a-Service (PaaS), and Software-as-a-Service (SaaS) are the three main cloud service models used commonly by cloud-based organizations today. They differ in their level of control and amount of responsibility the customer has over the cloud resources.
Infrastructure as a Service (IaaS)
In an IaaS model, the cloud provider offers a virtualized infrastructure that can be used as a substitute for physical hardware. Customers can rent computing resources, such as virtual machines, storage, and network components, and use them to run their applications or services. The customer has complete control over the operating system, middleware, and applications that run on this infrastructure and is responsible for managing them.
However, in an IaaS model, the customer is responsible for securing their applications and data and managing backups, disaster recovery, and other tasks related to the operating system and applications. This can require significant expertise and resources and may be challenging for some organizations.
Platform as a Service (PaaS)
In a PaaS model, the cloud provider offers a platform for building, deploying, and managing applications. The platform includes a runtime environment, development tools, and pre-built components that can be used to develop and deploy applications. As a result, the customer can focus on developing and deploying their applications if they manage the underlying infrastructure. The provider takes care of the infrastructure, such as servers, storage, and networking, as well as the operating system and middleware. The customer manages their applications and data without worrying about the infrastructure.
PaaS provides a balance between flexibility and convenience. It allows customers to focus on developing and deploying their applications while the provider manages the underlying infrastructure. It also provides a standardized development environment, which can help reduce development time and increase productivity. However, PaaS may have some limitations regarding customization and integration with other systems.
Software as a Service (SaaS)
In a SaaS model, the cloud provider offers software applications over the internet, which customers can access and use through a web browser or a client application. The provider takes care of the underlying infrastructure, operating system, and application software while the customer is responsible for configuring and using the software according to their needs. As a result, the customer does not have to worry about managing the infrastructure or software updates.
SaaS provides the highest level of convenience, as the provider takes care of everything related to the software application. The customer can focus on using the software and customizing it to their needs. However, SaaS may have limited customization options, and the customer may rely on the provider for support and updates.
Overall, the choice of cloud service model depends on the specific needs and requirements of the organization. IaaS provides the highest level of flexibility and control but requires more expertise and resources. PaaS balances flexibility and convenience, while SaaS delivers the highest comfort level but may have limited customization options.
Understanding the Different Layers of the Cloud Shared Responsibility Model
The Cloud Shared Responsibility Model comprises three layers: infrastructure, platform, and application. Each layer represents a different level of responsibility and requires a unique level of involvement from cloud service providers and their customers.
Infrastructure Layer
The infrastructure layer is the foundation of the Cloud Shared Responsibility Model. It includes the physical and virtual components of the cloud infrastructure, such as servers, storage, and network devices. In addition, cloud service providers are responsible for the security of the infrastructure layer, including physical security, network security, and access controls.
Customers are responsible for securing their data and applications on the infrastructure layer. They must ensure they use secure protocols and implement proper access controls. They are also responsible for ensuring that their applications and data are stored securely and using encryption where necessary.
Platform Layer
The platform layer is where the cloud service provider provides a platform for customers to build and deploy their applications. The platform layer includes operating systems, runtime environments, and databases. Cloud service providers are responsible for securing the platform layer, patching and updating the software, ensuring it is configured securely, and providing access controls.
Customers are responsible for securing their applications and data on the platform layer. They must ensure that their applications are secure, that they are using secure protocols, and that they are using encryption where necessary. They are also responsible for configuring their applications correctly and implementing proper access controls.
Application Layer
The application layer is where customers deploy their applications on the cloud service provider’s platform. Cloud service providers are not responsible for securing the application layer; it is the customer’s responsibility. However, customers must ensure that their applications are secure and that they are using secure protocols. They are also responsible for implementing proper access controls and securing their data.
Responsibilities of Cloud Service Providers and Customers
Cloud service providers and their customers have different responsibilities depending on the layer of the Cloud Shared Responsibility Model. Referencing the three layers in the last section of this blog, here is a breakdown of responsibilities by layer.
Infrastructure Layer Responsibilities
Cloud service providers are responsible for the following in the infrastructure layer:
- Physical security of the data center where the infrastructure is housed
- Network security, including firewalls and intrusion detection systems
- Patching and updating the infrastructure components
- Providing access controls and monitoring for unusual activity
Customers are responsible for the following in the infrastructure layer:
- Securing their data and applications
- Ensuring that they are using secure protocols, such as SSL/TLS
- Implementing proper access controls for their applications and data
- Using encryption where necessary
Platform Layer Responsibilities
Cloud service providers are responsible for the following in the platform layer:
- Patching and updating the operating system and software components
- Configuring the platform securely, such as disabling unnecessary services and implementing access controls
- Providing access controls for the platform
Customers are responsible for the following in the platform layer:
- Securing their applications and data
- Ensuring that they are using secure protocols, such as SSH
- Configuring their applications correctly and securely
- Implementing proper access controls for their applications and data
Application Layer Responsibilities
Customers are responsible for the following in the application layer:
- Securing their applications and data
- Ensuring that they are using secure protocols, such as HTTPS
- Implementing proper access controls for their applications and data
- Securing their data by encrypting sensitive information
An Alternative Way To Understanding Cloud Responsibilities
There is another model to outline the different layers of the Cloud Shared Responsibility Model. Rather than using the three layers, infrastructure, platform, and application, this model groups responsibilities into broader topics of interest.
- Physical Security – The cloud service provider is responsible for securing the physical data centers and hardware that run the cloud infrastructure. This includes providing physical security measures such as access controls, video surveillance, and intrusion detection systems.
- Network Security – The cloud service provider is responsible for securing the cloud network infrastructure, including firewalls, routers, and switches. They must ensure that the network infrastructure is protected from unauthorized access and cyber-attacks.
- Host Infrastructure Security – The cloud service provider is responsible for securing the underlying host infrastructure, including the hypervisor, virtual machines, and operating system. This includes ensuring that the host infrastructure is patched and up-to-date, and that any vulnerabilities are addressed promptly.
- Application Security – The customer is responsible for securing the applications that run on the cloud infrastructure. This includes configuring access controls, implementing encryption, and ensuring compliance with regulations.
- Data Security – The customer is responsible for securing the data stored on the cloud infrastructure. This includes implementing encryption, access controls, and data backup and recovery measures.
The Different Approach for Cloud Shared Responsibility Model between Amazon AWS, Google Cloud, and Microsoft Azure
Amazon AWS, Google Cloud, and Microsoft Azure are the leading cloud service providers in the market. Each unique approach to the Cloud Shared Responsibility Model sets them apart.
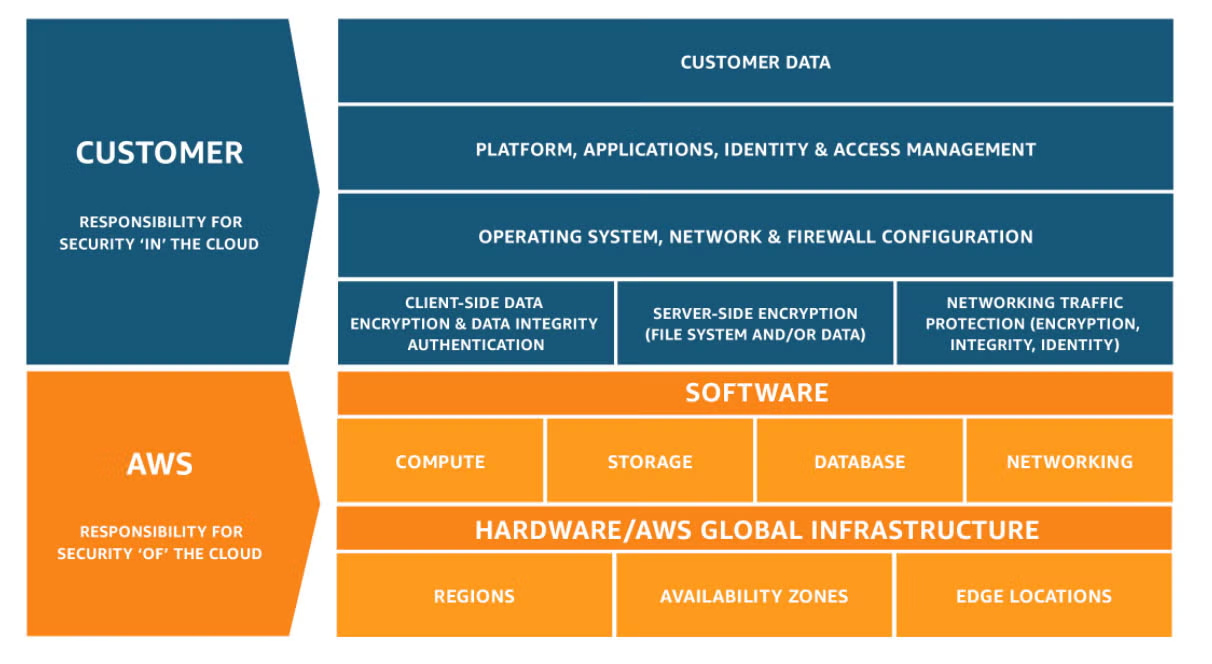
Amazon AWS Shared Responsibility Model
Amazon AWS provides a comprehensive shared responsibility model for its customers. According to AWS, they are responsible for the security of the cloud infrastructure, while customers are responsible for the security of the Cloud. AWS is responsible for securing the underlying infrastructure, such as physical servers, networking, and hypervisors. On the other hand, customers are responsible for securing their applications, data, and operating systems.
Under the AWS Shared Responsibility Model, customers have complete control over their data and applications. They are responsible for configuring their security groups, network access control lists, and firewalls. Additionally, customers can use AWS services such as AWS Identity and Access Management (IAM), AWS CloudTrail, and AWS Config to secure their environment further.
Google Cloud Shared Responsibility Model
Google Cloud takes a different approach to the Shared Responsibility Model. According to Google Cloud, they are responsible for the security of the infrastructure, while customers are responsible for securing their applications and data. This approach puts more responsibility on the customer than the cloud service provider.
Under the Google Cloud Shared Responsibility Model, customers are responsible for configuring their firewalls, setting up access controls, and securing their applications and data. In addition, Google Cloud provides several tools to help customers secure their environment, including Google Cloud IAM, Google Cloud Security Command Center, and Google Cloud DLP.
Microsoft Azure Shared Responsibility Model
Microsoft Azure provides a shared responsibility model that is similar to Amazon AWS. According to Microsoft, they are responsible for the security of the cloud infrastructure, while customers are responsible for the security in the Cloud. This approach puts more responsibility on the cloud service provider than the customer.
Under the Microsoft Azure Shared Responsibility Model, customers are responsible for securing their applications, data, and access control. They can use Azure Security Center, Azure Active Directory, and Azure Security and Compliance tools to secure their environment further.
Best Practices for Implementing the Cloud Shared Responsibility Model
Implementing the Cloud Shared Responsibility Model requires collaboration and communication between cloud service providers and their customers. Use these best practices as a starting guideline when implementing the model:
- Understand your responsibilities – Have a clear understanding of any responsibilities regarding the security of all applications, data, and operating systems that run on the cloud infrastructure.
- Follow security best practices – Follow industry-standard best practices, such as using strong passwords, enabling multi-factor authentication, and implementing encryption ensures long-term success while using the cloud.
- Implement access controls – Access to sensitive data and applications should be given based on user roles and permissions.
- Regularly monitor and update security measures – Assign security teams with closely monitoring the threat landscape for cloud-based risks on the rise. Ensure that security measures are updated in a timely manner to address any vulnerabilities or new threats.
- Comply with regulations – Work with legal experts to understand any applicable regulations such as HIPAA, PCI-DSS, and GDPR.
See SentinelOne in Action
Discover how AI-powered cloud security can protect your organization in a one-on-one demo with a SentinelOne product expert.
Get a DemoConclusion
The Cloud Shared Responsibility Model is a critical concept in cloud security. It clarifies the roles and responsibilities of cloud service providers and their customers when securing cloud assets. By understanding the different layers of the model and their respective responsibilities, cloud service providers and customers can work together to ensure that their cloud environments are secure and effective.
Cloud Shared Responsibility Model FAQs
The Cloud Shared Responsibility Model lays out who handles which security duties when you use cloud services. The provider secures the physical data centers, networks, and virtualization layers, while you handle everything you build and store in the cloud—your operating systems, applications, and data. This division helps each side focus on what they control, keeping your cloud environment safe and reliable.
Clear roles keep both sides accountable and stop security gaps. Without it, you might assume the provider covers data encryption or access controls when really it’s your job, or vice versa. Defining boundaries ensures nothing falls through the cracks, reduces duplicate efforts, and makes audits smoother by showing exactly who must act on each security control.
Cloud providers handle the infrastructure stack. They secure the physical data centers—power, cooling, and buildings—manage network defenses like firewalls and intrusion systems, maintain and patch servers and hypervisors, and ensure high availability of the hardware.
They also meet industry certifications (ISO 27001, SOC 2) and prove compliance for the underlying cloud platform.
The level of customer duties changes with IaaS, PaaS, and SaaS. With IaaS, you rent raw compute, so you secure the OS, middleware, apps, and data. PaaS gives you a managed runtime, so you focus on code and configurations, while the provider covers the OS and platform updates.
SaaS shifts most duties to the vendor—you only configure and use the application while they secure everything underneath.
Responsibilities usually break down into three layers:
- Infrastructure Layer: Hardware, virtualization, and network devices secured by the provider; you secure your data on those systems.
- Platform Layer: Operating systems, runtimes, and databases patched and configured by the provider; you lock down your apps and their settings.
- Application Layer: You handle application code, access controls, and data encryption; the provider does not secure your custom logic or business data.
SentinelOne’s Singularity™ Cloud Security enforces shared duties by giving you real-time visibility and automated controls across cloud workloads. It combines CSPM (posture checks), CWPP (workload protection), CIEM (permission management), IaC scanning, and one-click remediation.
Its AI-driven threat detection and policy enforcement cover every layer, so you spot misconfigs, enforce encryption, and quarantine threats before they impact your cloud resources.