Does Singularity Vulnerability Management require additional agents, hardware, or configuration?
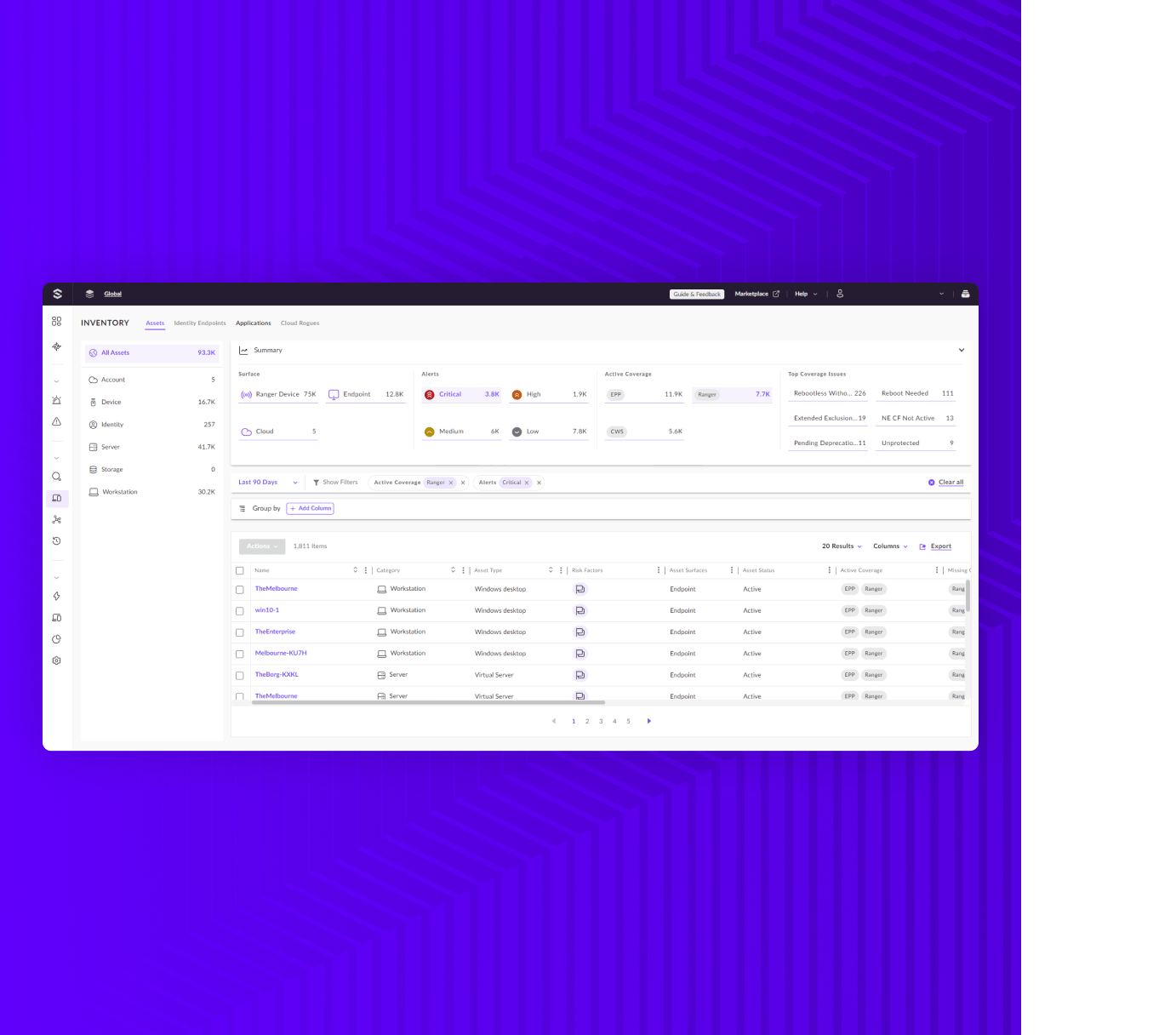
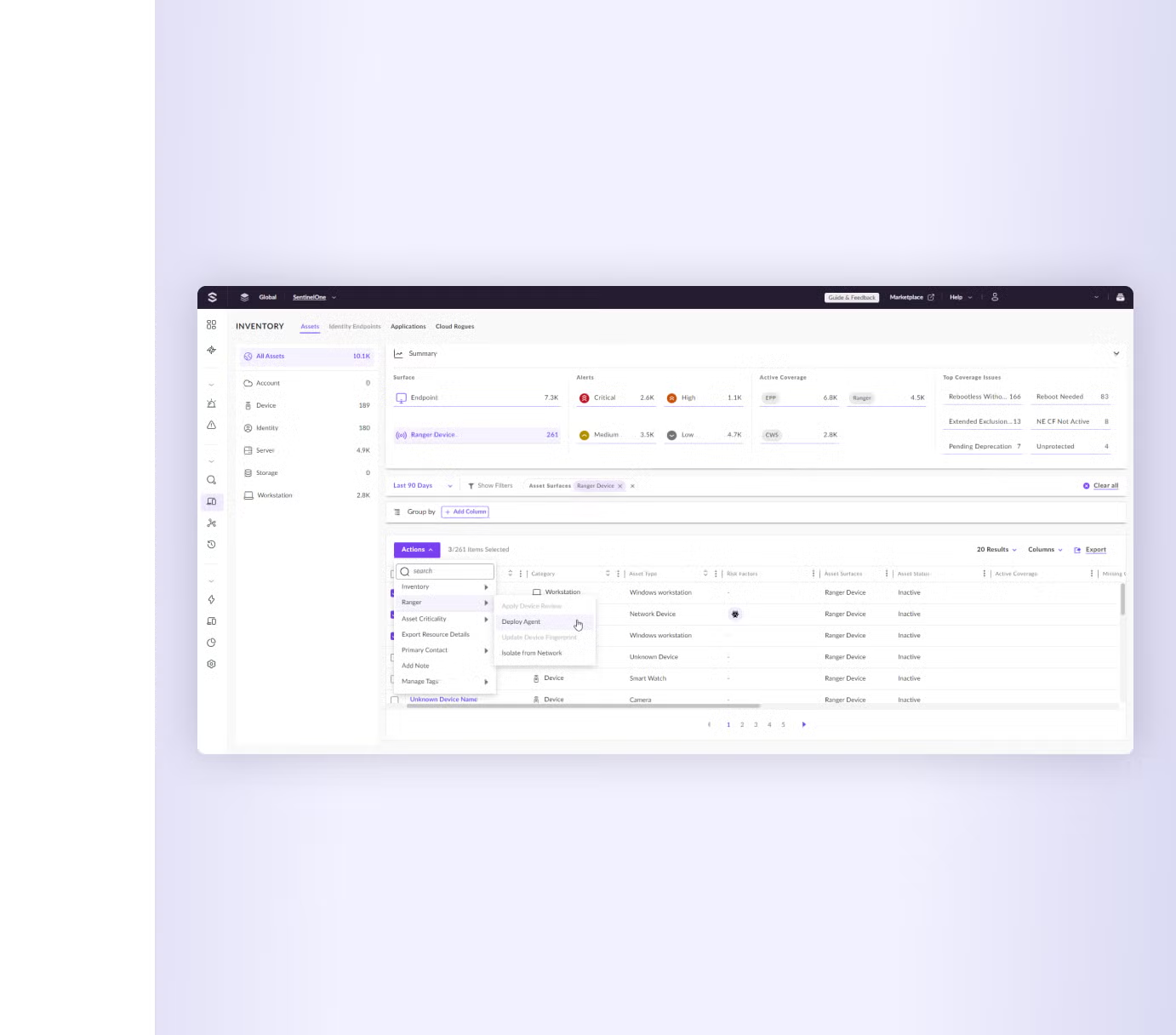
Singularity Vulnerability Management, formerly known as Singularity Ranger Insights, delivers continuous and real-time insights into vulnerabilities across operating systems and applications using the existing agent footprint. With a simple toggle, it adds comprehensive network discovery and vulnerability management capabilities to the SentinelOne agent. Scale your vulnerability management program and reduce complexity and cost—all without the need for additional deployment efforts, network scanners, or hardware.