SentinelOne Disrupts the EDR Paradigm, Making MITRE ATT&CK Framework New Hunting Standard
Eradicating Needle in the Haystack Searches with MITRE ATT&CK Framework in Plain English, Combined with Fully Assembled Threat Context
Mountain View, Calif. – August 1, 2019 – SentinelOne, the autonomous endpoint protection company, today announced new EDR capabilities that take its integration with the MITRE ATT&CKTM framework to the next level. Delivered via SentinelOne’s single agent, single codebase, single console architecture, SentinelOne is the first to allow security teams to use the MITRE ATT&CK framework as the new threat hunting standard. Through integrating the MITRE framework with its ActiveEDR and Ranger IoT capabilities, SentinelOne continues to deliver on its commitment to deliver the cybersecurity platform of the future, empowering security teams with unprecedented actionable threat context and visibility.
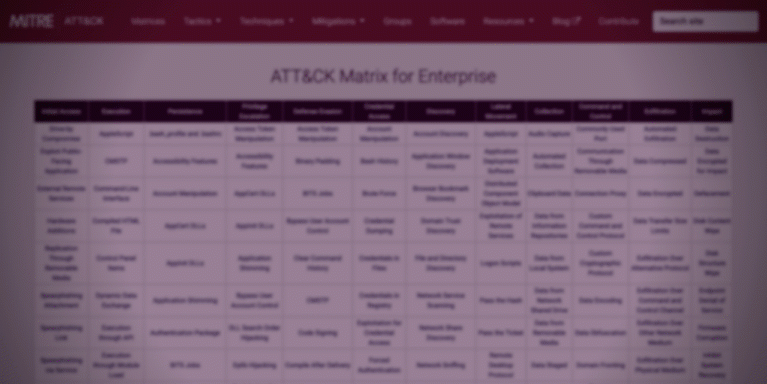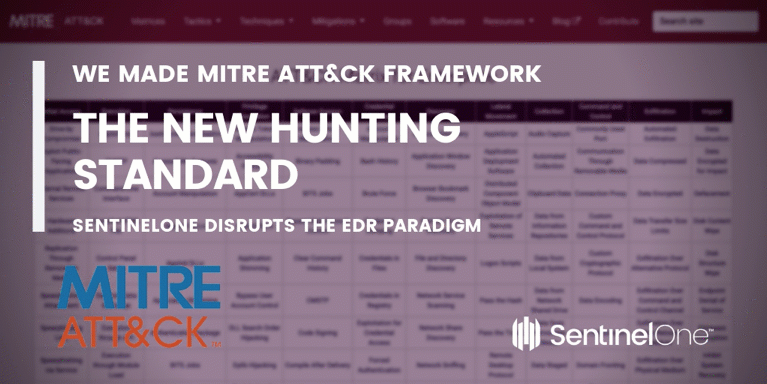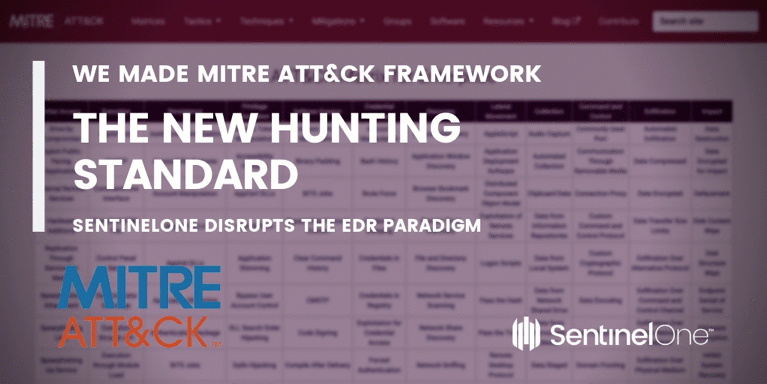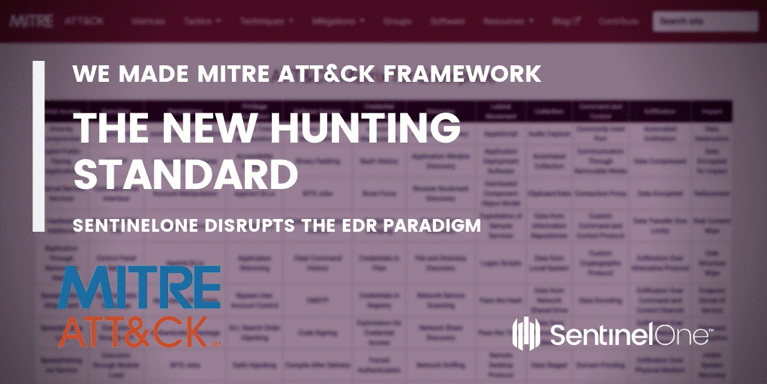
With the increasing noise on enterprise networks, it has become more challenging than ever to hunt for IOCs and understand the storyline behind them. SentinelOne empowers security teams by making the MITRE ATT&CK framework the new language of threat hunting. With the integration of MITRE tactics, techniques and procedures into the threat hunting query workflow, SentinelOne eliminates the traditional and manual work required by analysts to correlate and investigate their findings. In a click, security personnel can discover where the attack is coming from, what the attack is trying to do, what the attack is compromising, and actionable insight into how to fix it.
For example, if a program in an organization’s network tried to masquerade itself as a Windows process, all a security analyst would need to do to rectify the situation is simply search for the MITRE ATT&CK TTP. Once the analyst is notified of such indicators on their environment, in a single click, the analyst can discover the entire context around the TTP: On which devices it was seen? Where did it come from? What else was it trying to do? With SentinelOne, threat hunting is as simple as a single click of a button.
“Frameworks like MITRE ATT&CK exist to help organizations to manage cyber risk, and not enough organizations make effective use of them,” said Les Correia, Director, Global Information Security, Architecture, Engineering and Operations at Estée Lauder. “Through SentinelOne’s new integration, our team is able to quickly identify malicious activities, and quickly take action. Considering that most organizations who get hacked didn’t realize they were vulnerable until the attack eventually hit them, this is incredibly valuable to our team.”
“Security teams are continuously challenged with monitoring and protecting every edge of their network, from the endpoint to the cloud,” said Tomer Weingarten, CEO and Co-Founder, SentinelOne. “The MITRE ATT&CK framework provides a common vocabulary to understand threats. By integrating the framework in our threat hunting experience, enterprises gain unprecedented autonomous visibility across their network and can easily identify hidden threats, cutting the time to detect, contain, eradicate, and recover. We listen and ask faster than any other endpoint company, delivering technology that addresses tomorrow’s threat landscape today.”
As one the first endpoint companies to correlate alerts in product with the MITRE ATT&CK framework, embrace the MITRE ATT&CK Endpoint Protection Product Evaluation, and continuously detect, track, and link the context of all APT attacks with ONE autonomous agent in real-time during MITRE simulations, SentinelOne demonstrates leadership in providing immediate and enriched threat context and visibility within the MITRE framework.
SentinelOne will be demonstrating how it enables security teams to make the MITRE ATT&CK framework the new language of threat hunting at Black Hat Conference, August 7-8, 2019 in Las Vegas, Nevada at booth South Expo #222. To schedule a demo at the event, please visit our page.
About SentinelOne
SentinelOne delivers autonomous endpoint protection through a single agent that successfully prevents, detects, responds, and hunts attacks across all major vectors. Designed for extreme ease of use, the S1 platform saves customers time by applying AI to automatically eliminate threats in real time for both on premise and cloud environments and is the only solution to provide full visibility across networks directly from the endpoint. To learn more visit sentinelone.com or follow us at @SentinelOne, on LinkedIn or Facebook
Contact:
Maryellen Sartori
fama PR for SentinelOne
(617) 986-5035