December 6, 2017
SentinelOne vs WannaCry
SentinelOne successfully detects and block this ransomware strain. No update is needed.
WannaCry does not seem to be the end of these threats. Attackers can use these same exploits to not only lock up data to demand ransom but also to steal employee credentials to exfiltrate other sensitive information (think of this as a two-for-one attack – advanced threat combined with ransomware). Worse yet, as seen in this particular case, attackers can bypass traditional and next-generation security measures, including hundreds of intelligence, feeds. Further, security researchers who’ve tested security tools claim that these threats bypass 99% of security tools out there and we’re likely sitting with thousands and more computers infected across several industries.
Buyers are asking to validate the effectiveness of various traditional and next-generation endpoint security suites against the EternalBlue and Doublepulsar exploits/backdoor. These threats were unearthed by “The Shadow Brokers” hacking group and are said to have been used by the NSA-linked Equation Group to launch cyber-attacks. The EternalBlue exploit received recent worldwide attention due to the WannaCry outbreak that used this exploit to infect over 230,000 machines in over 150 countries.
WannaCry does not seem to be the end of these threats. Attackers can use these same exploits to not only lock up data to demand ransom but also to steal employee credentials to exfiltrate other sensitive information (think of this as a two-for-one attack – advanced threat combined with ransomware). Worse yet, as seen in this particular case, attackers can bypass traditional and next-generation security measures, including hundreds of intelligence, feeds. Further, security researchers who’ve tested security tools claim that these threats bypass 99% of security tools out there and we’re likely sitting with thousands and more computers infected across several industries.
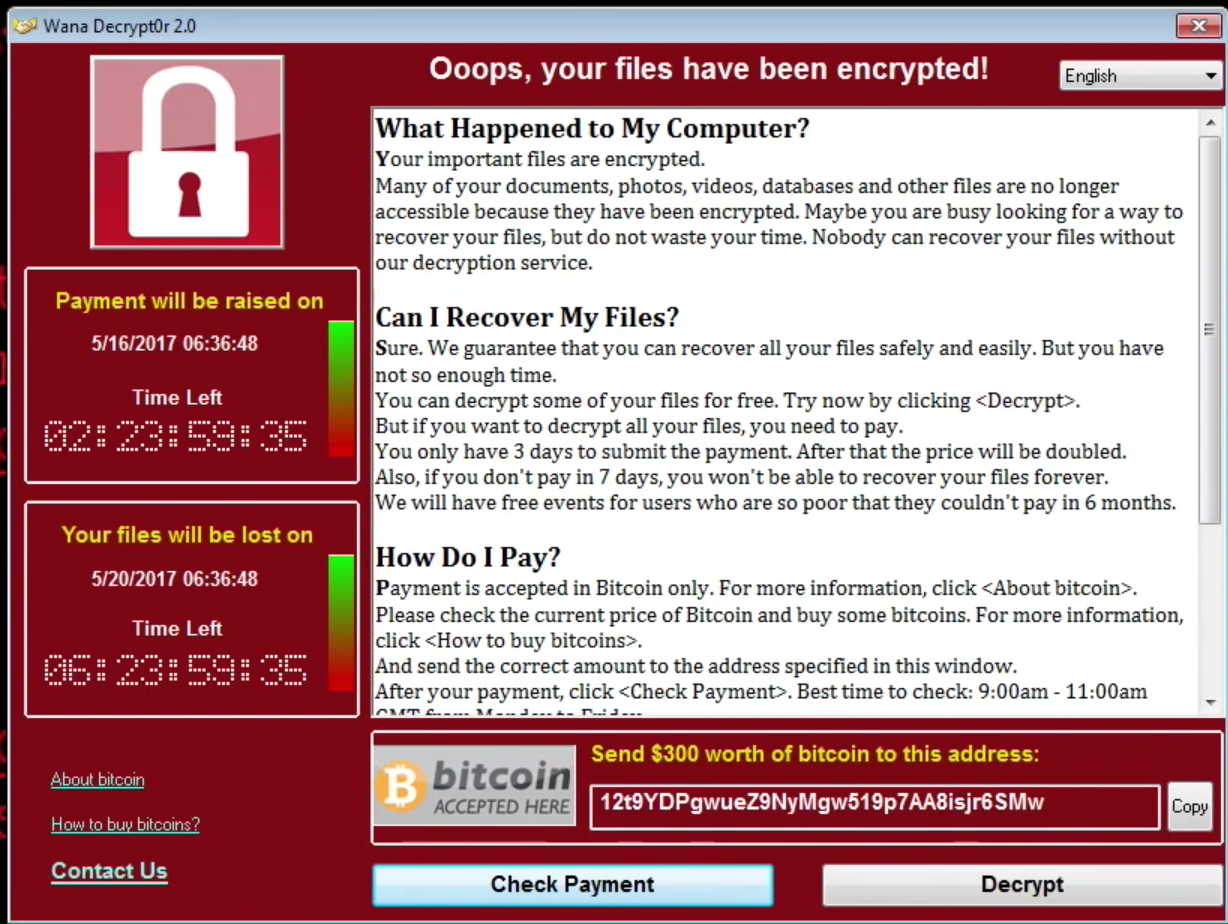 Another interesting aspect is the tactics used by WannaCry to other capabilities that may be exploited in the future. For instance, WannaCry is a strain of Windows ransomware that took advantage of the EternalBlue exploit along with a file-based payload. However, the EternalBlue exploit could easily be used with fileless (in-memory) malware that can completely work around the defenses of solutions that miss the exploit or focus on file-based detection. This methodology is discussed in the blog and was also used in the wild by another ransomware family dubbed UIWIX. In other words, customers without holistic protection will leave themselves exposed to another WannaCry-like attack in the future. So look at your security vendors carefully.
To learn more about how SentinelOne can help, check out our Endpoint Protection Platform or contact us for a free demo.
Another interesting aspect is the tactics used by WannaCry to other capabilities that may be exploited in the future. For instance, WannaCry is a strain of Windows ransomware that took advantage of the EternalBlue exploit along with a file-based payload. However, the EternalBlue exploit could easily be used with fileless (in-memory) malware that can completely work around the defenses of solutions that miss the exploit or focus on file-based detection. This methodology is discussed in the blog and was also used in the wild by another ransomware family dubbed UIWIX. In other words, customers without holistic protection will leave themselves exposed to another WannaCry-like attack in the future. So look at your security vendors carefully.
To learn more about how SentinelOne can help, check out our Endpoint Protection Platform or contact us for a free demo.
 Another interesting aspect is the tactics used by WannaCry to other capabilities that may be exploited in the future. For instance, WannaCry is a strain of Windows ransomware that took advantage of the EternalBlue exploit along with a file-based payload. However, the EternalBlue exploit could easily be used with fileless (in-memory) malware that can completely work around the defenses of solutions that miss the exploit or focus on file-based detection. This methodology is discussed in the blog and was also used in the wild by another ransomware family dubbed UIWIX. In other words, customers without holistic protection will leave themselves exposed to another WannaCry-like attack in the future. So look at your security vendors carefully.
To learn more about how SentinelOne can help, check out our Endpoint Protection Platform or contact us for a free demo.
Another interesting aspect is the tactics used by WannaCry to other capabilities that may be exploited in the future. For instance, WannaCry is a strain of Windows ransomware that took advantage of the EternalBlue exploit along with a file-based payload. However, the EternalBlue exploit could easily be used with fileless (in-memory) malware that can completely work around the defenses of solutions that miss the exploit or focus on file-based detection. This methodology is discussed in the blog and was also used in the wild by another ransomware family dubbed UIWIX. In other words, customers without holistic protection will leave themselves exposed to another WannaCry-like attack in the future. So look at your security vendors carefully.
To learn more about how SentinelOne can help, check out our Endpoint Protection Platform or contact us for a free demo.
Related Resources
YouTube Video
SentinelOne PartnerOne - America's 2025
⛳️ Last week in Pebble Beach the America's best cybersecurity partners came together for our annual PartnerOne summit. Check out…
Watch Now
YouTube Video
Just a Sec: Cybersecurity Unfiltered—Fast, Frank, and From the Front Lines
Welcome to the first-ever Just A Sec, a no-holds-barred, quick-fire monthly livestream. It’s cybersecurity like you’ve never heard it before—unfiltered,…
Watch Now